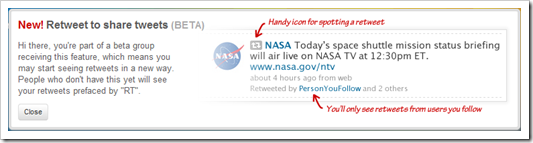
 ColorPix is a useful little color picker that grabs the pixel under your mouse and transforms it into a number of different color formats.
ColorPix is a useful little color picker that grabs the pixel under your mouse and transforms it into a number of different color formats.
You can use the built-in magnifier to zoom in on your screen, click on a color value to copy it directly to the clipboard, and even keep ColorPix on top of all other apps and out of the way.
Best of all, there's nothing to install - just download the tiny app and off you go. So grab it now, it's FREE!
Emergency
The Emergency Number worldwide for Mobile is 112. If you find yourself out of the coverage area of your mobile; network and there is an emergency, dial 112 and the mobile will search any existing network to establish the emergency number for you, and interestingly this number 112 can be dialled even if the keypad is locked.
Have you locked your keys in the car?
Does your car have remote keyless entry? This may come in handy someday. Good reason to own a cell phone: If you lock your keys in the car and the spare keys are at home, call someone at home on their cell phone from your cell phone. Hold your cell phone about a foot from your car door and have the person at your home press the unlock button, holding it near the mobile phone on their end. Your car will unlock. Saves someone from having to drive your keys to you. Distance is no object. You could be hundreds of miles away, and if you can reach someone who has the other "remote" for your car, you can unlock the doors (or the trunk).
Hidden Battery Power
Imagine your cell battery is very low. To activate, press the keys *3370# Your cell will restart with this reserve and the instrument will show a 50% increase in battery. This reserve will get charged when you charge your cell next time.
How to disable a STOLEN mobile phone?
To check your Mobile phone's serial number, key in the following digits on your phone: * # 0 6 #. A 15 digit code will appear on the screen. This number is unique to your handset. Write it down and keep it somewhere safe. When your phone get stolen, you can phone your service provider and give them this code. They will then be able to block your handset so even if the thief changes the SIM card, your phone will be totally useless. You probably won't get your phone back, but at least you know that whoever stole it can't use/sell it either. If everybody does this, there would be no point in people stealing mobile phones.
Finally, When you need to use the 411 information option, simply dial: (800) FREE 411, or (800) 373-3411 without incurring any charge at all. Program this into your cell phone now.
]]>Ottawa, December 27, 2006 – Privacy Commissioner of Canada Jennifer Stoddart is urging Canadians to add good privacy habits to their list of New Year’s resolutions.
"Polls have told us again and again that Canadians value their privacy. The start of the New Year is a great time for everyone to check whether they are doing enough to protect this important right," Ms. Stoddart said. "I hope people will add some good privacy habits to their New Year’s resolutions list."
Ms. Stoddart today released her top 10 resolutions for consumers to protect their privacy in 2007 and beyond. They are:
1. Guard your information
Ask questions when a cashier ringing in your purchases wants your name, address or telephone number. Why is the information being requested? How will it be used? If you are concerned about unwanted junk mail or telemarketing calls, decline to provide the information. It’s as simple as saying, "Sorry, I don’t want to share that personal information." Privacy laws give you a choice. You don’t always have to say "Yes."
2. Check your receipts
Some retailers still use older equipment that prints receipts with a complete credit card number – creating a risk the number will fall into the wrong hands and be fraudulently used. If the number is complete, use a pen to scratch out the middle four numbers on your copy.
3. Become a junk mail buster
If you don't want to be added to marketing lists, check the "no thanks" or opt-out box, or initial a note stating your preference, whenever you give personal information to magazine publishers, retail stores, charities and other organizations.
4. Take three steps to create more quiet nights at home
- Take advantage of the Do Not Contact Service (do-not-call, do-not-mail, and do-not-fax) offered at no cost by the Canadian Marketing Association (CMA). You can make the request online at www.the-cma.org.
- Ask your telephone company to remove you from the lists it sells to external organizations.
- When telemarketers call, insist they remove your name from their calling lists. They are now required by law to maintain do-not-call lists.
5. Develop a shredding habit
Make sure your blue box is not a goldmine for identity thieves. Buy a shredder (many are surprisingly inexpensive). Destroy all documents that include sensitive personal information, such as bank statements, credit card statements, credit card receipts, and pre-approved credit card applications.
6. Check loyalty program fine-print
Re-evaluate your membership in "rewards" or "points" programs. Often stores see your participation as consent to share your information without directly asking for permission. This can mean more junk mail and telemarketing calls. Read the program’s privacy policy. If you have concerns, don't join or ask the store not to share your personal information.
7. Become more privacy-aware on-line
Educate yourself about protecting your privacy on-line. Install the latest anti-spyware, anti-virus and firewall software on your computer. Shop only on secure sites – check for a lock symbol on the bottom right of the window. There’s plenty of advice on the Internet.
8. Stop Spam
Invest in a good spam filter and learn how to use it. Spam affects privacy rights because it involves the inappropriate use of personal information – your e-mail address. Protect your regular e-mail address by using it only with trusted friends and business associates. Get another address for other online uses. If you receive an e-mail from a sender you don’t recognize, or with a subject line that doesn’t make sense, just delete it. Opening spam may send a confirmation that an e-mail address is valid – and lead to more spam. The OPC homepage, www.privcom.gc.ca, includes a link to more information about spam.
9. Caution on the phone
Apply a healthy dose of skepticism when an e-mail or phone caller warns that your bank account or credit card has been compromised. Never reply to such e-mails, which may have been sent by ID thieves. Call your bank instead. Fraudsters are also using the telephone to get personal information. The best way to determine whether a call about account problems is legitimate is to say, "I’ll call you right back," and then call either the number on your credit card or account statement.
10. Protect your SIN
Ask questions when an organization asks for your Social Insurance Number. An ID thief could use your SIN to apply for a credit card or bank account in your name. Companies can’t insist that you provide a SIN unless it is required for a specific and legitimate purpose, such as tax reporting. Ask why the organization needs your SIN and whether you are required by law to provide it. If you are refused a product or service unless you give your SIN, complain to the Office of the Privacy Commissioner of Canada.
But recently, after performing more tests on server platform, I was really into it now and started considering seriously how to apply this technology to the server level. Michael Otey explained The High Cost of Server Sprawl?and indicated that
In most cases, server virtualization is the best way to implement server consolidation. Virtualization doesn't require specialized hardware, and it lets you run multiple OSs with complete application integrity. Better yet, two of the major virtualization products, Microsoft Virtual Server 2005 Release 2 and VMware Virtual Server 1.0, are both production ready and completely free.
Besides, one other thing that caught me really is its hardware-independent feature which could be a perfectly alternative solution for the disaster recovery purpose. I have been thinking the disaster recovery strategy for my company for long time and none of the solutions that I thought about or learned before could compare to this hardware-independent technology. Think about how easy it is while bad thing happens to my main server that hosts several of my critical servers. All I need to do is just moving the image files to the different server that has virtual server software loaded and fire them up again. I can bring all critical servers up and running within one hour or two. The down time allowance is totally fine for the size of my company.
The solution seems perfectly to me. But there are also more questions that need to be answered clearly before implementing the whole idea, such as how the backup strategy works with it, and how the switch over works when the disaster happens, etc.
I have created another category called Virtualization in this blog and hopefully will post more about this in the future.
]]>My most being used application in my computer. Might be used even more than IE, Firefox, and Outlook. Windows native notepad has been gone long ago.
Cropper was my favorite screen capture tool and still is but this tool offers more features and generates more attractive screen shots. And it's free too.
If you are an IT pro, this is a must have tool set for you. The author of this wonderful tool has joined into Microsoft team early this year. Another words, this tool set is not belonged to Microsoft.
This collection includes a bunch of free tools that you might find useful. I have used ProduKey to successfully recover the key code used to install the software on my computer but I lost long time ago. You definitely should check it out. It might surprise you.
]]>In Outlook or other email programs, what happens when you try to reply an email in sent folder. Right, it will reply to yourself. You might say it make sense because my name is on the from field but no, it doesn't make sense at all in real world. In a lot of cases, I actually want to continue the conversion with the person whom I previously emailed. In Outlook, if I want to do so, I have to click Forward and manually type the sender's address again. But in Gmail, because all conversions are all groupped together you can reply to anyone among in the conversion and whichever you pick to reply it always automatically put the person you want to communication with rather than yourself into the To box, which is exactly what I want. Sigh...only Google knows what I want after using email many years. Thanks!!
I have to say that small thing like this makes Google much prettier.
]]>Remote Desktop Connections Organizer
I know a lot of you probably use Windows Server 2003 Management Kit to manage many of your servers, same as?me, but it's also good to know that there are other FREE?tools out there available for the similar functionality with a little bit more.
Royal TS from code4ward?- some of the good features inlcude organize your connections in custom categories, connect to the console directly, check the session info even before logging into the machine, and connect to the machines that have different RDP port setup.
Visionapp Remote Desktop?- also has some other good features like, user-credential settings, disconnect from all select servers at once, and specify display and local device settings for each connection.
Free Personal?Anti-Virus Software
Symantec products are still pre-loaded on many of new computer but people hates they have to pay every year for the service, me too.? And more important, if you disregard the warning that tells you the service would be stopped if you don't register within such days, your computer would become vulnerable to any virus even the oldest ones without any protection.? So here are?two choices.? Both are free but the provider also offer the commercial versions too that have more features that support enterprise users.
Free avast! 4 Home Edition?- the software vendor claims as below to explain why they offer this free version.
avast! 4 Home Edition is a full-featured antivirus package designed exclusively for home users and non-commercial use. Both of these conditions should be met! Our company offers the Home Edition free of charge, since, in our opinion, it is possible to avoid global virus spreading by efficient prevention; however, many users are not able to or do not want to pay for antivirus software. This page will show you the most important features of this program.
AVG Anti-Virus Free?- same as above, the product is strictly being used for personal, non-commercial, and single home computer only.
Some other Tools
AJax DNS?- a AJax-based website that allows you to quickly check DNS information online.
Zamzar - Free online file conversion?- very cool online tool that supports most of popular file format.
CSS Tab Desinger?- a very cool simple tool that makes your CSS friendly tab design so easy.
Free Web Ringtone Maker?- cool, I am going to upload the CTU ringtone to my cell.? You should be familiar with this?ringtone if you know who Jack Bauer is
]]>
Confirming what might have been this year's worst kept secret, Microsoft Tuesday said users who buy PCs this holiday season loaded with Windows XP will get coupons for free or discounted upgrades to Vista when it ships next year.
The program is a moot point for users under Microsoft's volume licensing program, who are expected to get access to Vista at the end of November.
But consumers, small businesses and companies buying desktop PCs labeled "Windows Vista capable" will be eligible for the Vista upgrade coupons.
So if you happen to buy the new computer with “Windows Vista Capable” tag on, please make sure to take advantage of this offer once the new Vista comes out to the market.
]]>So far we’ve sold over 23,000 copies of Getting Real in PDF format. We introduced it on March 1 of this year, so we’re pretty thrilled with the results.
But 23,000 readers isn’t enough. We want millions of people to read the book. So today we introduce two new flavors that make the content even more accessible. And, in one case, completely free.
Good book, worth your precious time to read it.
20. hotmail.com - despite of the reason why it was nominated, which was considered as a virtual Switzerland for spammers, the well-known web-based email pioneer didn't dominate this market anymore. The fancy AJAX-based version of the hotmail live is still on beta. I tried but turned back to the classical version within a couple of days because I can't stand the performance they provided and compare the other two major email provider, GMail and Yahoo! Mail, honestly, the live version of hotmail is inferior. Hopefully, their team would make it better in the next beta version.
16. Microsoft Windows Update - the reason why it was listed is because it only can be accessed in IE. To me, it never was the problem. Besides, you can either turn on your Windows Automatic Updates which you should be doing anyway or load IETab extension in your Firefox so you can run it right from your favorite browser.
1. MySpace - the reason is good enough and because it is just too popular.
]]>The song, named “Drift Away”, was written by Mentor Williams, originally recorded by Dobie Gray in 1972, and being covered by bands and people all over the world for years.
Quoted from Drift Away - Wikipedia, the free encyclopedia
This song is also a famous "goodbye" or ending song for concerts. Its use is often as filler for a last song, usually in preparation for an encore, since it has a catchy beat and a guitar solo can be easily added to the end of the song in order to spice things up before the encore. As such, many live covers have been performed by a multitude of bands and it has become a hit among soft rock fans.
Drift Away Lyrics - Uncle Kracker
]]>
The tool is called vmware-vdiskmanager.exe which not only support expanding the virtual disk but do other stuff as well, i.e. defragment, shrink, create, etc.???First of all, I ran the following command in?the MS-Dos Prompt window to resize my Vista virtual disk to 30G.
vmware-vdiskmanager.exe -x 30Gb “windows vista.vmdk“
Because?of?VMware Virtual Disk Manager Does Not Expand Partitions, I have to run either Partition Magic or Windows DiskPart utility (diskpart.exe) to get my already loaded partition resized.? Wait...because?this is Vista which makes my life much easier, I don't need those tools anymore, all I need to do is opening the disk management from Computer Management console, right click the partition I want to expand and click “Extend Volume”.? Once I finished the short Extend Wizard, my main Vista partition now is extended to the new virtual disk size.
]]>Windows Server 2003 R2 Datacenter is coming soon to a via a volume license!? Although this was announced a while ago at the World Wide Partner Conference in July, as of October 1st you will be able to purchase Windows Server 2003 R2 Datacenter Edition through volume license channels.? So what does this mean to you?
Well if you are using Virtual Server 2005 R2 in your production enviroment, it can have a huge impact on your licensing costs.? Windows Server 2003 R2 Enterprise Edition allows for a single installation on a physical server, but also allows for up to four (4) virtual machines running any version of Windows 2003.? Windows Server 2003 R2 Datacenter Edition takes this one step further allowing for UNLIMITED virtual machine licenses.? Yes I said unlimited!!!
Just to drive this point home, you have one physical server, you purchase one OS license for said physical server, you then install Virtual Server 2005 R2 and install as many virtual machines as you require without the need (limit of four with R2 Enterprise Edition).? This could lead to some signifigant cost savings and most definately easy your license management.
The handy features in this version of freeware tool includes:
- Tree View synchronized with Node Text View for quick editing of node names and values.
- Incremental search (Ctrl+I) in both tree and text views, so as you type it navigates to matching nodes.
- Cut/copy/paste with full namespace support.
- Drag/drop support for easy manipulation of the tree, even across different instances of XML Notepad and from the file system.
- Infinite undo/redo for all edit operations.
- In place popup multi-line editing of large text node values.
- Configurable fonts and colors via the options dialog.
- Full find/replace dialog with support for regex and XPath.
- Good performance on large XML documents, loading a 3mb document in about one second.
- Instant XML schema validation while you edit with errors and warnings shown in the task list window.
- Intellisense based on expected elements and attributes and enumerated simple type values.
- Support for custom editors for date, dateTime and time datatypes and other types like color.
- Handy nudge tool bar buttons for quick movement of nodes up and down the tree.
- Inplace HTML viewer for processing xml-stylesheet processing instructions.
- Built-in XML Diff tool.
 I have been using VMWare Workstation 4.02 for quite a while, and am pretty happy with that until recently I tried to install the new Windows Vista RC1 on it by following the trick found on Joel's Installing Vista in VMWare Workstation, and was successful.? However, the VMWare Tools couldn't be loaded on the virtual machine whatever the settings I tried.? The installation wizard didn't even show up.? After googling a bit, and found the earliest version that supports to run Vista is 4.5.? So mine is too out-of-dated.
I have been using VMWare Workstation 4.02 for quite a while, and am pretty happy with that until recently I tried to install the new Windows Vista RC1 on it by following the trick found on Joel's Installing Vista in VMWare Workstation, and was successful.? However, the VMWare Tools couldn't be loaded on the virtual machine whatever the settings I tried.? The installation wizard didn't even show up.? After googling a bit, and found the earliest version that supports to run Vista is 4.5.? So mine is too out-of-dated.
 After another poked around in VMWare website trying to find if there is free upgrade package available to upgrade my version to at least the version that supports it, surprisingly I found VMWare offers even a better products, VMWare Server, for *FREE*.? I think that's probably because Microsoft offers its Virtual Server RC1 for free.? So I quickly downloaded it and loaded it on my XP machine first and replaced my old VMWare Workstation.? The installation ran quite smoothly other than a warning saying there might be some issue because the server version is supposedly running on a server platform, but I ignore it.? The program runs perfectly fine except that you can't monitor the status of the virtual machine remotely through web browser.? I opened the previously loaded Vista virtual machine, and successfully installed VMWare Tools on it.? Now I am on Beta and evaluating this version...and enjoying the moment both VMWare Server and Vista brought to me.
After another poked around in VMWare website trying to find if there is free upgrade package available to upgrade my version to at least the version that supports it, surprisingly I found VMWare offers even a better products, VMWare Server, for *FREE*.? I think that's probably because Microsoft offers its Virtual Server RC1 for free.? So I quickly downloaded it and loaded it on my XP machine first and replaced my old VMWare Workstation.? The installation ran quite smoothly other than a warning saying there might be some issue because the server version is supposedly running on a server platform, but I ignore it.? The program runs perfectly fine except that you can't monitor the status of the virtual machine remotely through web browser.? I opened the previously loaded Vista virtual machine, and successfully installed VMWare Tools on it.? Now I am on Beta and evaluating this version...and enjoying the moment both VMWare Server and Vista brought to me.
The trick on Joel's post is to set svgaMaxWidth and svgaMaxHeight in .vmx file to bypass the hung in the first phase of installation.? And this Guest Operating System Installation Guide?from VMWare website provides more details on how to install Vista on VMWare platform.? Here is the steps I took to get my Vista loaded:
1. Created a new virtual machine, and picked Windows XP as the guest.
2. Edited the .vmx files to add these two lines mentioned on Joel's post.
3. Turned on the virtual machine, and started loading the Vista.
4. Once it's done, loaded the VMWare Tools after the Vista was fully booted.
5. Then added the another following line to the .vmx file because the network driver didn't work this time.? This trick was also mentioned in that Guide document.
Ethernet0.virtualDev = "vmxnet"
6. Then after another couple of updates were loaded, my Vista was fully functional on my VMWare Server machine.
Also, I am very happy with the performance that VMWare products brought to me.? Personally, I think it's better than the two virtual products Microsoft offers.
]]>IETab
IE Tab, an extension from Taiwan, embeds Internet Explorer in a Mozilla/Firefox tab.
This extension is derived from the famous extension IE View, but much different.
While IE View always open IE-only pages in a seperate Internet Explorer window, IE Tab can view them in a Mozilla/Firefox tab.
Web Develop Extension
The Web Developer extension adds a menu and a toolbar to the browser with various web developer tools. It is designed for Firefox, Flock, Mozilla and Seamonkey, and will run on any platform that these browsers support including Windows, Mac OS X and Linux.
If you are viewing this page in FireFox, you can install them right from below:
IE Tab
it's true, you can run Windows Updates right from your FireFox browser, isn't it nice??
Web Develop Extension
compare to IE developer toolbar, this seems to offer more features for web developers
You could refer to Aaron’s post from last winter that described some of the old and new shortcuts available in IE7. Or, you might spend a few minutes searching through Help (haven’t used Help before? Just press F1!). These resources are great, but can be difficult to access during the key moment when you are trying to remember a shortcut. Alternatively, maybe you need to remember how to change tab settings, or perform another common task within the browser. Again, looking through Help can be time consuming and not really necessary if you just need a quick piece of information.
Enter the Internet Explorer 7 Quick Reference Sheet! We’ve created this sheet to bring together keyboard shortcuts and directions for common tasks in one, easy to access location. Rather than provide an exhaustive listing of ALL the IE shortcuts (there are a lot!), we focused on outlining only the ones that perform the most popular actions within the browser. Limiting the scope in this way allowed us to create a document that can be printed on a single page of paper, which you can keep handy near your computer as you browse the web.
Good stuff like this is always good to have.
]]>Utilities for Communicating
1. FileZilla
2. OpenSSH
Utilities for Sniffing
3. WinDump
4. Ngrep
5. Ethereal
Utilities for Scanning, Auditing, and Monitoring
6. BareTail
7. NeWT
8. Winfingerprint
Round-up of 50 AJAX Toolkits and Frameworks
Very good resources from Max Kiesler, highly recommended to those AJAX-enthusiasts.
]]>
I recently installed a new SonciWall TZ 170 firewall to replace our two IPCop boxes. One of the main reason why I picked up this appliance is its WAN Failover and Load Balance feature which is not oftenly you can find in this range product, and yes, we have two Internet Access line serving in our office. There are four modes of Failover and Load Balance in this product, which are:
- Basic Active/Passive Failover;
- Per Connection Round-Robin;
- Spill-over-Based;
- Percentage-Based
I picked last one as the method we use for this feature and the setting I mentioned above that might be causing this issue is the option under this method, called “Use Source and Destination IP Binding”, which is turned off by default in the first time when you set it up.
About Source and Destination IP Address Binding
When you establish a connection with a WAN, you can create multiple interfaces, dividing up the task load over these interfaces. There are both Primary and Secondary WAN interfaces. This task distribution model maintains high performance, ensuring that one interface does not become an impasse to the point where it blocks traffic from passing. This process is WAN Load Balancing.
While WAN Load Balancing addresses performance challenges, it can create other problems, including losing track of sessions. Session confusion can occur because some applications fail to adequately track multiple user sessions load-balanced on multiple interfaces. These applications treat incoming packets as originating from different users because they use IP addresses to differentiate user sessions instead of application-layer user identification tags.
To ensure that you have proper connectivity in all applications, SonicWALL provides a feature called Source and Destination IP Addresses Binding, a solution that maintains a consistent mapping of traffic flows with a single outbound WAN interface.
Here we go, that's it. That's the main reason why the session keeps getting timed out because the accessing could be through different lines during the session and in most cases you will be kicked out if the website you try to access is highly secured. Once I turned it back on, the problem then was gone completely. So keep in mind that ensure to have this option ticked when you set up the Failover & Load Balance feature on your firewall.
]]>The ideas mentioned in this article that might help are:
- You can do anything but not everything -- and you can only do one thing at a time.
- The biggest time-management mistake is keeping track of commitments in your head...so just get it out of your mind.
- Once you know the task, figure out the action you need to take within 24 hours.
- Start by blocking an hour or half-hour each day as power time to accomplish priorities. That may mean coming in early or hiding in the cafeteria to escape interruptions.
- Break tasks into 10-minute segments; when you get interrupted, jot a phrase or cue to bring you back into the task later.
Good luck on it.
]]>Software Virtualization Solution allows you to instantly activate, deactivate or reset application and completely avoid conflicts between applications. It ensures applications use the correct files and registry settings, without modifying the operating system and without interfering with other applications. With this SVS in hand, you don't need to worry the bad designed software ruin your system any more. Is it difficult to use? Not at all. Just install, create layer for the application that you want to virtualize, and go. And more attractively, you can download the personal-use version for free. It definitely worth a try.
]]>Custom formatting HTML in Visual Web Developer and Visual Studio 2005
]]>Method 2
If a domain controller configuration corresponds to scenarios 3 and 4, select any file on the volume that includes Active Directory database files in the right pane of NTBACKUP. This file can be a dummy file. In this configuration, this volume is backed up by NTBACKUP.
Useful SQL Queries to Analyze and Monitor SharePoint Portal Solutions Usage
]]>NT Objectives' NTOinsight and NTOweb from http://www.ntojectives.com/freeware
ScreamingCobra from http://samy.pl/scobra
Massive Enumeration Tool from www.gnucitizen.org
Foundstone's SiteDigger from http://foundstone.com/resources/s3i_tools.htm
]]>Here's how to unblock blocked attachments.
(Substitute the appropriate version numbers for your installation, 12 is 2007, 11 is 2003, etc.)
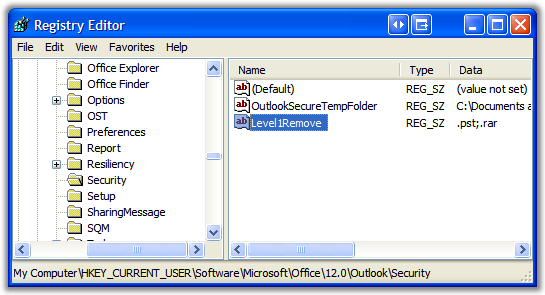
Add a registry string value under HKEY_CURRENT_USER\Software\Microsoft\Office\<VERSION>\Security called Level1Remove and add the extensions you want with leading dots and trailing semicolons like:
.pst;.rar

Skype is a little program for making free calls within the US and Canada to all phones until the end of the year. Skype to Skype calls anywhere in the world are also free. It's easy to download and use, and works with most computers.
http://www.idude.net/iHTML/articles/browser_cache_override.asp
]]>Free CSS Navigation Menu Designs from Exploding-Boy that I found on his latest links, which is pretty useful.
]]>SQL Prompt provides Intellisense? style auto-completion for Microsoft SQL Server editors. It will tell you the exact formatting you should use for your SQL commands, while you are writing them and will therefore help you write fast, perfectly formatted SQL statements. SQL Prompt improves the productivity of all SQL script creation.
No more thinking, remembering...Go download quick because it's free for download until 1st September 2006
]]>Delete the MSLicneses registry folder under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
This works on a Windows machine, but what if I get this message on a Mac machine, thanks Vera Noest, MVP for Terminal Server, for providing this instruction to me:
- uninstall your rdp client completely from the Mac and reboot
- delete the license from /Users/Shared/Microsoft/RDC Crucial Server Information/RDC GLOBAL DATA.
- reboot again and re-install the rdp client.
Check Vera Noest's Terminal Server and Citrix Troubleshooting website
]]>So now, can't stay with this beta version anymore...and can't even back to beta 1...Sigh...now I am back to IE version 6.
]]>I discovered the first glitch right after I installed the program. Two websites that I go quite often are www.nhl.com and www.nba.com. Both websites use the Flash a lot to get rich and very attractive visual effect, and their main menu like scores, stats, and standing are all embeded in the Flash. I don't have any problem before even in IE 7 Beta 1.0. However, in this new beta, I have to click twice to get into the page, the first click is to make the flash part in active, and the second is to active the link. I don't know why it would like this but kind annoying.
The second glitch is even more annoying. The back button in the top left corner sometimes doesn't really go back to the page that you just previously visit, it went to the previous website instead. This is very bad. For people like me who often use back button instead of the back link in the page would in danger to lost the data in the form in the current page. The best guess is that for those pages that don't go back properly usually contain the scripts or forms that refresh the current page to get updated data listed or something like that. This version of IE doesn't work well with this part.
The two glitches are still minor compare the overall achievement they made on this version. However, they would make it more close to perfect if they can fix them in the next release.
]]>Charles Plumb was a U.S. Navy jet pilot in Vietnam. After 75 combat missions, his plane was destroyed by a surface-to-air missile. Plumb ejected and parachuted into enemy hands. He was captured and spent 6 years in a communist Vietnamese
prison. He survived the ordeal and now lectures on lessons learned from that experience!
One day, when Plumb and his wife were sitting in a restaurant, a man at another table came up and said, “You're Plumb! You flew jet fighters in Vietnam from the aircraft carrier Kitty Hawk. You were shot down”! “How in the world did you know that?" asked Plumb. “I packed your parachute,” the man replied.
The man pumped his hand and said, “I guess it worked!” Plumb assured him, “It sure did. If your chute hadn't worked, I wouldn't be here today.” Plumb couldn't sleep that night, thinking about that man. Plumb says, "I kept wondering what he had
looked like in a Navy uniform: a white hat, a bib in the back, and bell-bottom trousers. I wonder how many times I might have seen him and not even said 'Good morning, how are you?' or anything because, you see, I was a fighter pilot and he was just a sailor."
Plumb thought of the many hours the sailor had spent at a long wooden table in the bowels of the ship, carefully weaving the shrouds and folding the silks of each chute, holding in his hands each time the fate of someone he didn't know.
Now, Plumb asks his audience, "Who's packing your parachute?" Everyone has someone who provides what they need to make it through the day. He also points out that he needed many kinds of parachutes when his plane was shot down over enemy territory--he needed his physical parachute, his mental parachute, his emotional parachute, and his spiritual parachute. He called on all these supports before reaching safety.
Sometimes in the daily challenges that life gives us, we miss what is really important. We may fail to say hello, please, or thank you, congratulate someone on something wonderful that has happened to them, give a compliment, or just do something nice for no reason. As you go through this week, this month, this year, recognize people who pack your parachutes.

download the evaluation version from here
The evaluation provides you the full features without time limitation except leaving a watermark on a repaired copy of PDF file. However, I discovered that this cross-page watermark can be easily removed in Acrobat Standard edition but would be very time-consuming if the PDF file contains hundreds of pages because you have to manually remove it from every single page.
ToDoList 4.5.2 - A simple and effective way to keep on top of your tasks
]]>AltovaXML from Altova (http://www.altova.com)
AltovaXML™ 2006 is an XML standards processor that includes engines that drive the award-winning Altova XMLSpy®, MapForce®, and StyleVision® development tools for use in your custom applications - royalty-free! AltovaXML™ 2006 is a single download that include the Altova:
| XML validating parser | |
| XSLT 1.0 engine | |
| XSLT 2.0 engine (schema-aware) | |
| XQuery 1.0 engine (schema-aware) |
AltovaXML™ 2006 includes COM, Java, and .NET interfaces so that it can be used from a variety of different applications, and you can also call its functionality from the command line. It is a free executable file available for royalty-free use in your applications.
Altova also has another pretty cool free tool, called XMLSpy 2006 Home Edition, an XML editor that makes XML editing technologies available in a FREE application ideally suited for hobbyists, entry-level developers, and students.
FusionCharts Lite from Infosoft Global (http://www.infosoftglobal.com)
 FusionCharts Lite is a free charting component that you can download and use in your private and commercial projects. It contains six basic charts including Area, Bar, Column, Line, Pie and Pipe. Use with any scripting language and database!
FusionCharts Lite is a free charting component that you can download and use in your private and commercial projects. It contains six basic charts including Area, Bar, Column, Line, Pie and Pipe. Use with any scripting language and database!
Open source developers can redistribute this with their applications for FREE.
]]> The etiquette of tipping is confusing. You'll tip your barista at the coffee joint, but not the gas jockey at the pump. You'll tip your hairdresser at the salon, but not the associate at the department store.
The etiquette of tipping is confusing. You'll tip your barista at the coffee joint, but not the gas jockey at the pump. You'll tip your hairdresser at the salon, but not the associate at the department store.
Some people get tips just for doing their job, some don't. So where do bloggers sit on that tip scale? Are they worthy of a few paypal pennies? You pay for the newspaper you read each day, should you pay for a blog you like to check out?
Some do have subscription fees, but for the casual blogger looking to make some spare change, the blogger's tip jar has just been created.
Pro level bloggers using typepad can now set up a simple tip jar in their menu bars. It's just another way to make some spare change along with the google ads everyone seems to include amongst their text.
To make it easy, the Tip Jar feature works via PayPal, so millions of weblog readers can simply drop cash in to your weblog from their PayPal accounts or directly from their credit cards.
Now since all events in other cities across United States are all full, if you didn't get one, don't worry, just head over to the place where holding the event. You should be able to check in and get all those copies.
]]> You sure have many options to use to find your own stuff from your local computer, for example, Google Desktop Search, MSN Desktop Search, or even run local built-in search function. But when it comes down to find your stuff in your inbox from your Outlook, Microsoft Lookout is my choice.
You sure have many options to use to find your own stuff from your local computer, for example, Google Desktop Search, MSN Desktop Search, or even run local built-in search function. But when it comes down to find your stuff in your inbox from your Outlook, Microsoft Lookout is my choice.
Microsoft Lookout is a free Outlook add-on that provides better indexing and retrieval capabilities than Outlook's standard Find, Advanced Find, or Search Folders features can provide. And one of the benefitial over Googl Desktop Search is that it indexes email attachments and Exchange public folders, which mean that it works with Exchange server and you can search by the name of the attachments.
]]>- Nmap - http://www.insecure.org/nmap
- N-Stealth - http://www.nstalker.com/eng/products/nstealth
- SNMPWalk - http://net-snmp.sourceforge.net
- Fpipe - http://www.foundstone.com
- SQLRECON - http://specialopssecurity.com/labs/sqlrecon
- Enum - http://www.bindview.com/services/razor/utilities
- PsTools - http://www.sysinternals.com/utilitites.html
- Netcat - http://www.vulnwatch.org/netcat
- John the Ripper - http://www.openwall.com
- The Metasploit Framework - http://www.metaspoit.com
what else features do Exchange 2003 SP2 offer to you? see the top 10 reasons here
]]>I guess Google put more weight on the words in the main title than in the other parts in the page. So I would suggest if you want your name shown up in the first or first couple of page in Google, you better put your name in your main title rather than any other places.
]]>Also, curious on how Google does this? Joel Spolsky?pointed out that:
A very senior Microsoft developer who moved to Google told me that Google works and thinks at a higher level of abstraction than Microsoft. "Google uses Bayesian filtering the way Microsoft uses the if statement," he said. That's true. Google also uses full-text-search-of-the-entire-Internet the way Microsoft uses little tables that list what error IDs correspond to which help text. Look at how Google does spell checking: it's not based on dictionaries; it's based on word usage statistics of the entire Internet, which is why Google knows how to correct my name, misspelled, and Microsoft Word doesn't.
]]>- due to the capacity limitation of 2 Gigabyte, I can't use it for archiving the mailbox that is over this limitation. Well, I can use multiple PST file to archive the message but the only advantage I can see is leading to mess.
- the PST file only can be accessed by one user. It will be lucked if one user accessed it in one computer but doesn't exit properly.
- it seems that the Auto-Archive feature is not a server-based feature, which means if you have multiple outlook running on multiple computer and they are not setup the same way, you would be in trouble. For example, you open your outlook in your working computer during your working hour and also use another outlook through remote desktop. It would be mess if two outlooks have different Auto-Archive settings.
So, if you are not 100% sure how these 2 features work, don't use it. If you do need archive feature, I would suggest the 3rd party software, like GFIMailArchiver from GFI Software. How can we disable them if we really don't need them?
from Microsoft Knowledgebase, article ID 258277
- quite all programs.
- click Start, and then click Run.
- in the Open box, type regedit, and then click OK.
- locate one of the following keys in the registry, as applicable:
HKEY_LOCAL_MACHINE\Software\Microsoft\Office\xx.0\Outlook\
note that the **xx** in the line above will be 8 for Office 97, 9 for Office 2000, 10 for Office XP, and 11 for Office 2003 - on the Edit menu, click Add Value, and then add the following registry value:
Value Name: DisablePst
Data Type: REG_DWORD
Value: 1 - quit Registry Editor.
First of all, he pointed out two things you have to avoid.
Number one. If you ever find yourself implementing a feature simply because it has been promised to one customer, RED DANGER LIGHTS should be going off in your head. If you're doing things for one customer, you've either got a loose cannon sales person, or you're slipping dangerously down the slope towards consultingware.
Number two, not to decide what features to implement. Don't do things just because they're inevitable. Inevitability is not a high enough bar.
Then, he presented a good way how to prioritize the tasks which he learned at the time during the planning Excel 5.0. Basically,
- List all the features;
- Vote on each feature by just a quick “thumbs up“ or “thumbs down“, and throw out all features that only have one or two votes;
- Assign cost for each of these features, on a scale of 1 to 10;
- Make a menu of all these features and their “costs“. Everybody on the team got a copy of the menu and was given $50 to play with. They could allocate their money any way they wanted, but they only had $50 to spend.
- Add up how much everyone spent on each feature;
- Divide the amount spent by the cost;
- Finally, sort by this number to find the most popular features.
Ha...quite amazing!
]]>Most Innovative Product: DesktopStandard's Policy Maker (http://www.desktopstandard.com)
Best Software: Sunbelt Software's iHateSpam (http://www.sunbeltsoftware.com)
Rookie of the Year (Best New Product): Sunbelt Software's CounterSpy Enterprise (http://www.sunbeltsoftware.com)
Disaster Prevention & Recovery
Enterprise Backup/Recovery/Archive Software: Winternals Software Recovery Manager 2.0 (http://www.winternals.com)
Desktop Backup/Recovery/Archive Software: Veritas Software VERITAS Backup Exec for Windows Servers (http://www.veritas.com)
Enterprise Backup/Recovery/Archive Hardware: Dell PowerVault Storage (http://www.dell.com)
Replication/Data Availability Solution: Neverfail Group Neverfail for Windows Product Suite (http://www.neverfailgroup.com)
Messaging and Collaboration
Mail Server: Microsoft Exchange Server 2003 (http://www.microsoft.com)
Exchange Backup/Disaster Recovery: Neverfail Group Neverfail for Exchange (http://www.neverfailgroup.com)
Mail Archiving: GFI Software GFI MailArchiver for Exchange (http://www.gfi.com)
comments: highly recommended. With its method of storing internal and external messages in Microsoft SQL Server database (saving as much as 80 percent over personal folder store - PST storage), this solution is a sweet dream.
Antispam/Server: Sunbelt Software iHateSpam for Exchange (http://www.sunbeltsoftware.com)
My vote, however, is GFI Software GFI MailEssential for Exchange/SMTP (http://www.gfi.com)
IM Monitoring and Security: Websense Web Security Suite (http://ww2.websense.com)
Collaboration Solution: Citrix Systems Citrix GoToMeeting Corporate (http://www.citrix.com)
Network Management
Load Balancer: Microsoft Windows Server 2003 (http://www.microsoft.com)
Network Analyzer: Sunbelt Software LanHound (http://www.sunbeltsoftware.com)
Network Layout and Design Tool: Ipswitch WhatsUp Professional (http://www.ipswitch.com)
Remote Computing
Remote Control Software: Microsoft Windows Server 2003 Terminal Services
VPN Solution: Microsoft Windows Server 2003 with Service Pack 1
Security
AntiVirus/Mail Server: Trend Micro ScanMail for Microsoft Exchange (http://www.trendmicro.com)
My vote: Symantec Mail Security for Microsoft Exchange
Firewall/Server or Standalone: Check Point Software Technologies Check Point VPN-I Pro (http://www.checkpoint.com)
Proxy Server/Web Access Control and Monitoring: Websense Enterprise (http://www.websense.com)
Intrusion Detection and Prevention: eEye Digital Security Blink (http://www.eeye.com)
Vulnerability Scanner: Sunbelt Software Sunbelt Network Security Inspector (http://www.sunbeltsoftware.com)
Password-Management Software: RSA Security RSA Sign-On Manager (http://www.rsasecurity.com)
Authentication Solution (Two-Factor/Nonbiometric): RSA Security RSA SecurID (http://www.rsasecurity.com)
Authentication Solution (Biometric): Lenel Systems International OnGuard ID CredentialCenter (http://www.lenel.com)
System Management
Active Directory Management Tool: Microsoft Group Policy Managment Console
Performance Tuning Tool: Microsoft Operation Manager 2005
Patch Management Tool: Microsoft Windows Server Update Services
Disk Imaging Software: Symantec Norton Ghost (http://www.symantec.com)
Help Desk Software: Help Desk Technology International HelpSTAR (http://www.helpstar.com)
My vote: AdventNet Help Desk & Asset Management (http://www.adventnet.com)
Monitoring and Alerting Software: Sunbelt Software ServerVision
My vote: AdventNet OpManager (http://www.adventnet.com)
Registry Management Tool: DesktopStandard PolicyMaker Registry Extension (http://www.desktopstandard.com)
Remote Client Management Tool: LANDesk Software LANDesk (http://www.landesk.com)
Virtualization Software: Microsoft Virtual Server 2005
My vote: VMWare VMWare Workstation (http://www.vmware.com)
Application and Operations Management Tool: Microsoft Operations Manager (MOM) 2005
Asset Management Software: Microsoft Systems Management Server (SMS) 2003
Software Deployment Tool: Microsoft Systems Management Server (SMS) 2003
Utilities
Defragmentation Utility: Raxco Software PerfectDisk (http://www.raxco.com)
Emergency Recovery Console Utility: Winternals Software ERD Commander 2005 (http://www.winternals.com)
File-Compression Tool: WinZip Computing WinZip (http://www.winzip.com)
Undelete Utility: Diskeeper Undelete (http://www.executive.com)
]]>Ask: How do I know my small business idea will work?
Answer: It isn't your idea that will make you millions, but what you do with it.
Ask: How to make your idea work?
Answer: 1. Write that business plan; 2. Do your homework; 3. Launch it already; 4. Get to work.
Getting things started is the best way to learn from your inevitable mistakes.
Also see the cheat sheets at Cheat Sheet Round
[Update on Oct. 7, 2005] CSS Hacks Chart via RoudyBob.Net
]]>One of my colleagues was working on his laptop the other day. All of sudden, he called me to come to his desk to check what this noisy sound came from. I went to his desk, and immediately pointed out the HD in his laptop is dying because that sound is typically a sign indicating that there is something wrong inside the HD. I said I can try to recover some data but no guaranty. He was very depressed at that time becuase it would lose his 2-year class notes. He was lucky as I successfully recovered data before the HD completely dead. This is just one of the cases. How many times did it happen to me? At least 6 times this year so far. I think this number is not low because I am not working on a computer hardware shop at all.
I agree that backing up your local data is not a easy step to accomplish if you don't have the right tool. But these 2 free tools make me feel so easy to do this kind of boring but important job by just couple of clicks. Check it out and back up your data right now.
]]>I know the performance of SATA would meet my expectation for the server but I wasn't sure what makes almost all vendors to use it instead of SCSI HD. Should I go with it and trust its performance and reliability? Serial ATA: opening new markets for ATA RAID - Serial ATA explains pretty clearly why it happens. This is something I should trust and rely on, so I decided and purchased one IBM server with 2 SATA Swap HD (still don't know what this **Swap** means to me).
Also you can check more detail technical information about SATA from the Serial ATA International Organization (SATA-IO) website.
[Updated on Oct. 6, 2005]: This white paper also explains more in detail: Serial ATA in Servers and Networked Storage
]]> Have you started using Dfs (Distrubuted File System) that has been released as a useful feature since Windows Server 2000? If you haven't, you really really should start playing around with it. It's so useful, not only because it releases the pain for managing all your network shared folders across the whole network, but also it provides some kind of fault-tolerant feature and fail-over function on your network shared resources, which saying that if Dfs is configured properly in your system, you don't have to worry about what I should do if one of the servers gets crashed or dead because the replicated network resources in Dfs are still available transparently to the end users.
Have you started using Dfs (Distrubuted File System) that has been released as a useful feature since Windows Server 2000? If you haven't, you really really should start playing around with it. It's so useful, not only because it releases the pain for managing all your network shared folders across the whole network, but also it provides some kind of fault-tolerant feature and fail-over function on your network shared resources, which saying that if Dfs is configured properly in your system, you don't have to worry about what I should do if one of the servers gets crashed or dead because the replicated network resources in Dfs are still available transparently to the end users.
I had one server failed last week, but with Dfs configured on that server, I managed to get all people back to work after only a really short down time period. So I thought I should put emphasis on it and share with other people how good this feature is. Here are some benefits you can get from Dfs if the bad thing happens on your system, like the motherboard on the server is dead:
Minimum down time
With multiple replica configured in Dfs, one failure server doesn't fall down the whole resources, the end users are still able to access the resources from other servers. People might not even notice it.
Give more time to work on the failure server
When the server gets down, people like me would feel very stressful because none of the bosses would like to have the server down for period of time, sooner gets the server back the better.
No need to update the login script any more
If you use the traditional mapping method and you changed the server after the server crash, you need to change the login script and ask all users to logoff and log back in to get the updated mapped driver. Now with Dfs, people don't have to do that, it all does automatically and transparently because all mappings are not based on the server name but the domain name now.
]]>Here are the top 10 on the list:
- Nessus
- Ethereal
- Snort
- Netcat
- TCPDump / WinDump
- Hping2
- DSniff
- GFI LanGuard
- Ettercap
- Whisker/Libwhisker
Sounds from typeing on computer keyboards are distinctive enough to be decoded, allowing security breaches caused by “acoustic snooping.” University of California, Berkeley researchers said Wednesday.
The researchers said they were able to feed sound recordings of typing on keyboards into a computer and use an algorithm to recover up to 96 percent of the keyboard characters entered by typists.
Sigh, security risk everywhere!!
[Prose from the Pros] There are many sites where website templates are available free to download. Those who do not know web design basics they just simple download them. However flash templates are most interactive websites. If you want to do online business you can outsource your web design contract. Even you can find cv template for personal use.
]]> Found this tool from regular Microsoft Download Newsletters. Did you feel painful every time when you want to backup your data from your local computer to somewhere else? I do. This pain makes me so laze to backup my stuff out of my local computer. Now with this awsome tool from Microsoft, I can easily backup my stuff off to the network drive for just only a couple of clicks. Badly, I don't have any excuse for not doing it regularly from now on.
Found this tool from regular Microsoft Download Newsletters. Did you feel painful every time when you want to backup your data from your local computer to somewhere else? I do. This pain makes me so laze to backup my stuff out of my local computer. Now with this awsome tool from Microsoft, I can easily backup my stuff off to the network drive for just only a couple of clicks. Badly, I don't have any excuse for not doing it regularly from now on.
SyncToy v1.0 is available as a free download on the Microsoft Download Center. The easy to use, customizable application helps you copy, move, rename, and delete files between folders and computers.
SyncToy is a free PowerToy for Microsoft Windows XP that provides is an easy to use, highly customizable program that helps users to do the heavy lifting involved with the copying, moving, and synchronization of different directories. Most common operations can be performed with just a few clicks of the mouse, and additional customization is available without added complexity. SyncToy can manage multiple sets of folders at the same time; it can combine files from two folders in one case, and mimic renames and deletes in another. Unlike other applications, SyncToy actually keeps track of renames to files and will make sure those changes get carried over to the synchronized folder.
Microsoft Corp. and Canon Inc. today announced another major milestone resulting from the companies’ strategic alliance: a new color management system for the upcoming Microsoft® Windows Vista™ operating system. The new Windows® Color System will enable greater fidelity and predictability of color throughout Microsoft’s new operating system. The system will provide better screen-to-print matching, better overall color appearance, and support for higher fidelity printing, giving users new tools to take advantage of the capabilities of today’s powerful color devices such as digital cameras and color printers.
New Color Management System for Windows Vista Highlights Alliance between Microsoft and Canon
]]> CCleaner is a freeware system optimization and privacy tool. It removes unused files from your system - allowing Windows to run faster and freeing up valuable hard disk space. It also cleans traces of your online activities such as your Internet history. But the best part is that it's fast (normally taking less that a second to run) and contains NO Spyware or Adware! :)
CCleaner is a freeware system optimization and privacy tool. It removes unused files from your system - allowing Windows to run faster and freeing up valuable hard disk space. It also cleans traces of your online activities such as your Internet history. But the best part is that it's fast (normally taking less that a second to run) and contains NO Spyware or Adware! :)
File Hippo - Free Software Download - I found it also contains a lot of free program, from all kinds of area.
]]>Keep important files at your fingertips - anywhere. All file changes are automatically synchronized between linked computers, so you are always accessing the latest documents, photos, music, and files.
Obviously, the reason why we don't see the TextBoxes with the specified width in FireFox is because they are rendered without the width set at all. That just sucks. The reason why the TextBox's Width property is rendered as style=”width:125px;” in IE but not in FireFox is because FireFox is seen as a down-level browser in ASP.NET 1.x so it is rendered without the style attribute.
...
A better way to fix the problem is to force ASP.NET to recognize FireFox as an up-level browser that supports things like style, etc so that controls will automagically render themselves properly as they do in IE. To do this, we can either modify the web.config file for the web page or modify the machine.config file so that the change is recognized in all sites/pages hosted on that machine.
BrowserCaps and other Browser Testing/Detection Resources - slingfive.com
]]>Today, by reading one of the Q & A from the recent issue of Exchange & Outlook Administrator, I have also learned that there is another reason why we still need to keep it. The original question is whether Exhcange will suffer if WINS is removed, and the short answer is:
Microsoft recommends that you use WINS; though the service isn't required, Microsoft won't support Exhcange configurations that don't use it. The Microsoft article “Exchange Server 2003 and Exchange Server 2000 require NetBIOS name resolution for full functionality” clearly states this recommendation but doesn't clearly explain why WINS is required or what to do if you're determined to remove it.
So...WINS is still alive, for certain circumstance, we do need it in a Windows environment.
]]>The article explains how to update the feed to FeedBurner very clearly and in detail, there are 4 steps in short:
- Make physical Rss.aspx replaced with an HTTP 301 status code;
- Change the web.configure file to tell the ASP.Net engine to take care of requests to this new made Rss.aspx file;
- Update the appropriate <HttpHandler>
line to tell the engine to use the new feed address; - Update the link to the site's feed in the My Link section.
Microsoft Makes WinFS Beta 1 Bits Available from Microsoft Watch
Microsoft Storage Fundation (WinFS) Preview from Paul Thurrott's SuperSite for Windows
]]>This post doesn't only explain how he debugged this issue in detail, but also shows a good example how to use these three wonderful tools, Process Explorer, Filemon and Regmon, which are all made by www.sysinternals.com.
]]> WindowBlinds is a program that enables users to safely add thousands of new visual styles to Windows to change the look and feel of your computer.
WindowBlinds is a program that enables users to safely add thousands of new visual styles to Windows to change the look and feel of your computer.
 Stardock CursorXP is a program that lets you use and create incredibly cool looking Windows mouse cursors.
Stardock CursorXP is a program that lets you use and create incredibly cool looking Windows mouse cursors.
It does this by taking advantage of the new visual effects features of Windows 2000 and Windows XP.
 ObjectDock is a program that lets you organize your short-cuts and running tasks onto an extremely customizable dock that sits on your desktop.
ObjectDock is a program that lets you organize your short-cuts and running tasks onto an extremely customizable dock that sits on your desktop.
Comment: Some of the extensions like GoogleNotifier and GoogleAdsenseNotifier are really cool. I am just wondering why there are no such great add-ons on IE, or if there is why is so hard to find them because 90% of my surfing time is still rely on IE?
]]>- Free upgrade to 2G web / SQL storage space after I renew the contract this November;
- Unbelievable Hosting Panel, in which you can almost do whatever you need to do to configure your website without calling or emailing the request to their support team. The hosting panel also has SQL Server Manager enabled, easy for the customer to manager their SQL database online through web browser;
- A lot of free .Net add-on, including Community Server 1.1, nGallery, and other ASP.net starter kits;
- Free Microsoft SharePoint Services enabled;
- Unlimited mutliple Domains and Sub-Domains support, another wonderful unbeatable feature in which I can virtually provide web hosting services to my customers;
- Very good detail web stats, and it can be based on your multiple domains and sub-domains;
- Tech support is very good. You have two choices to contact their support team if you have any issue related on their services, either place a call online in their online tech support website or give them a call directly. By either way, they provide a rapid, and good quality of service to make sure your issues are addressed in a very short period.
- Provides affiliate program, you can earn 20% commission of the purchase. Another small reason why I wrote this post here. However, even without this reason, I would still highly recommend this wonderful web hosting service.
Gauss, originally came from the name of German mathematician and astronomer known for his contributions to algebra, differential geometry, probability theory, and number theory, expresses the centimeter-gram-second unit of magnetic induction. The following definition explains it in more detail.
quote from The Sharpened Glossary
Ever wonder what that "degauss" button on your monitor does besides make a buzzing noise and cause the screen to go crazy for a second? Though that's its main purpose, the degauss button has another useful feature. To understand it, you'll first need to know that the earth has natural magnetic fields. The magnetic charges from these fields can build up inside your monitor, causing a loss of color accuracy. Degaussing scares the bad magnetism out of the monitor and fills it with good karma. If your monitor doesn't have a degauss button, fear not -- many new monitors automatically degauss themselves. If you have a flat-panel display, there is no degauss button because magnetism doesn't build up in flat screen displays.
So, what features in dasBlog actually attract me to use it?
- Easy to implement, their XML based infrastructure makes the whole installation, upgrade, and maintain really easy. Having a strong backend database to store all data is always a good idea for many reasons. However, to a blog, XML is good enough.
- Upload images and files while you prepare your post. It is quite difficult or inconvienience to do it on .Text but I can live with it for now.
- Email to post. I haven't used it yet but it sounds very attractive.
- Easy to customize the theme for your own. The structure of theme on dasBlog is cool, really easy to customize it to make one for your own. I actually made one and will share it blow for anyone who might be interested.
- There are others I am sure I haven't digged it out.
The recently released version of dasBlog, called 1.8 Gold, provides a lot of new features, including a bunch of new themes. I used one called “calmBlue” as a template and made one for my own called “Jungle”(see the image below). Feel free to download it below.
download the dasBlog theme Jungle here
note: after you extract the file into theme folder, please copy all images under images folder to the your dasBlog images folder. These images are configured at css file but so far I still didn't figure out how to correctly put a related path for these images if I saved them under my jungle theme folder.
- Create and edit databases in Microsoft SQL Server 2000 or Microsoft SQL Server 2000 Desktop Engine (MSDE)
- Perform ad-hoc queries against databases and save them to your file system
- Export and import database schema and data
These application templates are tailored to address the needs and requirements for specific business processes or sets of tasks for organizations of any size. The applications are the first out-of-box custom scenarios for the Windows SharePoint Services platform, though they also provide a starting point for partners and developers looking to build deeper Windows SharePoint Services solutions.
I will be testing it in the following couple of days to see how it goes and will share some good ones here.
]]>The first thing that I tested right after the installation is to test if this version of IE is still compatible with the websites that are desiged for IE 6 because one of the biggest improvement of IE 7 is to more compatible with the CSS and HTML standard. And yes, IE 7 still renders same way as IE 6 renders the site. So I guess, Microsoft didn't only suit their web browser to the industrial standard, but still work with their own standard as well, which is good at this moment. At least, it would save my time to just adjust the view of the website.
The second thing that I tested is to test how tab works in IE7. Honestly, I am quite disappointed on this part. The function is great, works the way like how Firefox works. But to me, it lacks some advanced features that some other tabbed IE-based add-on browsers provide, i.e. Avant browser and Maxthon Browser. If the following beta version or final version doesn't get this improved somehow I guess I would still stay with add-on browser just because of the conveniency. Some features that are missing are:
- flexible placing tabs either on the bottom or on the top;
- some mouse actions that could easily close or open new tab, or easily go forward or backward;
- It opens another new browser rather than open another new tab in existing opened browser when I click a link in your email or other application.
- No skin still, which is not that important to me.
The third thing that I tested is to test how new print feature works. The “Shrink-to-Fit” print option works great, better than “Fit-Width Print” add-on for IE 6, and orphan control looks awesome.
I guess I will continue testing the other features that come with this new version of IE and keep updating any thoughts I might have in here.
]]>
Download Nattyware / Pixie here
P.S. Johnny Hughes is the designer of dasBlog theme Portal
]]> GMail Drive is a Shell Namespace Extension that creates a virtual filesystem around your Google Gmail account, allowing you to use Gmail as a storage medium.
GMail Drive is a Shell Namespace Extension that creates a virtual filesystem around your Google Gmail account, allowing you to use Gmail as a storage medium.
GMail Drive creates a virtual filesystem on top of your Google Gmail account and enables you to save and retrieve files stored on your Gmail account directly from inside Windows Explorer. GMail Drive literally adds a new drive to your computer under the My Computer folder, where you can create new folders, copy and drag'n'drop files to.
 I have been suffering this problem badly recently (see the problem in the figure) every time when I tried to print the webpage from IE, and even worse that I can't get anything printed off from Outlook or Outlook Express. Simply anything related on HTML can't be printed. I guess some sort of Adware or Spyware got passed through to my computer the other day and this problem immediately happened right after I ran the anti-spyware software and cleaned them up. I even ran three major anti-spyware software, Microsoft Anti-Spyware, LavaSoft Ad-Aware, and Spybot, to see if it fixed the problem up but unfortunately no.
I have been suffering this problem badly recently (see the problem in the figure) every time when I tried to print the webpage from IE, and even worse that I can't get anything printed off from Outlook or Outlook Express. Simply anything related on HTML can't be printed. I guess some sort of Adware or Spyware got passed through to my computer the other day and this problem immediately happened right after I ran the anti-spyware software and cleaned them up. I even ran three major anti-spyware software, Microsoft Anti-Spyware, LavaSoft Ad-Aware, and Spybot, to see if it fixed the problem up but unfortunately no.
So the best guess is that either IE system file got corrupted or some registry key settings got messed up. I googled by putting the whole URL message “res//c:\windows\system32\shdoclc.dll/preview.dlg”, and surprisely got too many information related on this with various line number in it and only a few are exactly the same as what I had. Followed some articles' instructions like checking registry key, re-register some dll files, but none of them fixed my problem. Finally, on Microsoft IE newsgroup I found one post that had the exactly same message as I have and got fixed by doing a slight differently than other ones I found on Google. Magically, it fixed my problem by following their instructions which likes below:
1. Re-installing the latest version of Microsoft Script, http://www.microsoft.com/downloads/details.aspx?FamilyID=c717d943-7e4b-4622-86eb-95a22b832caa&DisplayLang=en;
2. Re-register the following DLLs:
jscript.dll
vbscript.dll
urlmon.dll
mshtml.dll
msjava.dll
actxprxy.dll
oleaut32.dll
browseui.dll
shell32.dll
3. Reboot my computer to take all changes effect.
The jscript.dll and vbscript.dll are not listed on other articles that I found from Google, which is why I said it fixed the problem a slightly different. And also, after I did search these 2 files on my computer, I found the size of these two files are slightly different than from other no problem computer. So I copied these 2 files over as well from good computer but I am not sure if this helped to fix the problem. Anyway, the problem that has been annoying me for a couple of weeks has been gone now. I am back in business again without re-formatting my computer which might take me couple of weeks to fully configure it. Big thanks to Robear Dyer (PA Bear) who pointed out the great solution below and helped me out on IE newsgroup.
]]>- download the XML version of add-on from ELMAH GotDotNet webspace;
- place XmlErrorLog.dll file into your web application bin directory;
- edit the web.config file to point to the new provider. If you are using connection string, remove it and replace with ErrorLogPath attribute which should point to the physical location where the logs are saved, see the sample below:
<errorLog
type="GotDotNet.Elmah.XmlErrorLog, GotDotNet.Elmah.XmlErrorLog"
LogPath="C:\Inetpub\wwwroot\wdd\errorlog" />
When building a large site, understanding the subtleties of these pieces of the puzzle can be the difference between successfully organizing your CSS and creating a house of cards that could collapse at any moment.
]]> HD Tune is a freeware, hard disk utility that has the following functions:
HD Tune is a freeware, hard disk utility that has the following functions:
- Transfer Rate
- Access Time
- CPU Usage
- Burst Rate
- S.M.A.R.T. Information (Self-Monitoring Analysis and Reporting Technology)
- Power On Time

PDF Online (formerly goBCL / goHTM) provides you with quick and free document conversion into PDF and HTML formats. As a web-based server solution, PDF Online allows you to convert documents automatically, from your PC or your Mac, from your home or your office…from anywhere in the world!
PDF Online lets you submit documents from your web browser. PDF Online then processes your document and, within minutes, generates and emails you an accurate PDF or HTML (complete with JPEG files) representation of your document. Although the service can process files of any size, we have imposed a maximum upload file size of 2MB.
When converting to HTML, PDF Online offers many advantages over the HTML export filters that come with most document authoring tools.
Configuration
- Remember to enable anonymous access on the IIS
I forgot about it when I did on the previous version, SUS, which caused me hours to try to figure out why the client machine always failed to get updated. - Add local build-in user ASPNet on Windows Server 2000 and Network Service on 2003 into the security list on default WSUS web location. It might not be necessary but would be nice to try if you are having some weird problems that you can't figure it out why.
Useful Command
- Detect Now Option
wuauclt.exe /detectnow - Resetauthorization Option - which expire the cookie, initiate detection, and have WSUS update computer group membership
wuauclt.exe /resetauthorization /detectnow - Restart Automatic Updates services
net stop wuauserv
net start wuauserv
Check the Log files
- Client computer - check the log file to see if it successfully communicate with the WSUS server.
The log file is named windowsupdate.log without space between windows and update, and it is located under default windows root folder. - WSUS server - check the IIS log file to see if the client machine gets updated successfully.
Check the IIS log file which is located at System32\Logfiles folder under default Windows folder.
Tip 1: For some reason, some time the workstations just can't get updated and rebooted on schedule. One of the reason is because there is another update service running at that time. Kill the process wuauclt.exe from Task Manager or Stop the Update services may help to fix this issue.
Tip 2: If you have workstations and laptops in your organization, seperating them into two different OU might be a good approach to work with because those laptops might not get updated on schedule.
Tip 3 (updated on Aug 5, 2005): When you update the workstation on AD by adding GP on it, you can run "gpupdate /force" to get the new GP settings updated on the workstion without rebooting it.
]]>
The guy in the middle is the one who is created by some kind of photo editor program. :)
And according the formula to calculate the tall of your kids, which is listed below, their daughter will be 199.2cm and son will be 224.6cm.
Gile in cm = ( Father + Mother ) * 1.08 / 2
Boy in cm = ( Father * 0.923 + Mother ) / 2
well, curiously, I calculated for my daughter who will be 162.6cm, and my son, if I would have, will be 183cm.
]]> Switched to this browser today for couple of reasons:
Switched to this browser today for couple of reasons:
- Intergrated with IE more seamlessly. On my previous tabbed browser, Avant, some pages can't be viewed properly but does on this one. One of the sample is to view Photo on MSN space.
- Native IE plug-in can be used as well as the plug-ins for Maxthon. Fit-width Print is the one I really want to have on any browsers.
- External utilites can be embeded on the toolbar, from which you can easily access them without minimize or close the browser.
- Enhanced AD-blocker. It blocks not only popup ones but ads in the web page as well. With Web Ads Blocker enabled, Google Ads on my page will be disappeared even though I don't really want to.
- Shows the dimension of the window on the right bottom corner while you resize the browser, which is quite helpful while I am doing some web design work.
- Also, it shows workstation's IP address on the status bar and the speed of download, seems a little gift to me.
- Seems faster, plus all features I loved on Avant Browser.
Both broswers look really good, highly recommed to anyone who has to stay with IE and wants Tabbed feature.
]]>- New fallback printer driver capability
It makes local printing more accessible for Terminal server clients by configuring Terminal Services to default to a printer driver compatible with PostScript(PS) or Print Control Language(PCL). This new feature is exceptionally useful if a terminal server doesn't have a printer driver installed that machines the Terminal Server client user's specific printer brand and model. - Authentication and Encryption for Terminal Services
This is the feature I found today the first that doesn't show up on Windows server 2003 without Service Pack 1 installed. It enhance the security of Terminal Server by configuring TS connections to use Secure Sockets Layer (SSL) / Transport Layer Security (TLS) 1.0 for server authentication, and to encrypt terminal server communications.
Why is this change important while RDP does provide data encryption? Because, by default, it doesn't provide authentication to verify the identity of a terminal server. - New group policy settings for Terminal Services Licensing
Three new group policy settings added with new service pack:
1) Set the Terminal Server Licensing mode;
2) Use the specified Terminal Server license servers policy setting;
3) Show ToolTips for licensing problems on Terminal server policy setting.
Terminal Services has a week side on granting the valid client license from the license server since Windows Server 200. Some time the client just got the temporary license which will expire in 90 days whether the license server is correctly installed or not. It just either can't find the right server or can't get the right license over the server. Fortunately, it has a work around by deleting “MSLicensing“ keyset from registry editor every time when the license on the client machine expires. And hopefully this new feature would solve this problem. - Update to group policy setting for starting a program on connection to a terminal server
Now, we can modify the Start program on connection policy setting in Group Policy for the local policy object, meaning that we can configure this policy setting for individual terminal servers within a domain.
What's new in terminal services for Windows Server 2003 Service Pack 1 from Microsoft
]]> The Error Logging Modules And Handlers (ELMAH) were written by Atif Aziz and Scott Mitchell, and demonstrate an easy means to add error logging capabilities to an ASP.NET Web application. ELMAH illustrates how HTTP modules and handlers can be used to provide a high degree of componentization for code that is orthogonal to the Web application (such as application-wide logging). ELMAH is a truly pluggable solution, meaning that it can be dynamically added to a running ASP.NET Web application without any need for recompilation or redeployment.
The Error Logging Modules And Handlers (ELMAH) were written by Atif Aziz and Scott Mitchell, and demonstrate an easy means to add error logging capabilities to an ASP.NET Web application. ELMAH illustrates how HTTP modules and handlers can be used to provide a high degree of componentization for code that is orthogonal to the Web application (such as application-wide logging). ELMAH is a truly pluggable solution, meaning that it can be dynamically added to a running ASP.NET Web application without any need for recompilation or redeployment.
Regardless of the reason, when an exception occurs, especially on a live site, it is important that the details of the exception are recorded in order to assist with diagnosing the problem. ELMAH provides a mechanism for centralized error logging and notification. Whenever an exception occurs in an ASP.NET application that is not caught, ELMAH is notified and handles the exception as spelled out in the Web.config file. This may include recording the details of the exception to a database, sending an e-mail to an administrator, or both.
You can implement this wonderful module as simple as the 4 steps described below:
- Download the file from ELMAH GotDotNet Workspace;
- Upload the package to your webserver;
- Run SQL script to create the SQL table and Store Procedures. You can also configure it not to use SQL backend database as the storage to store all logs;
- Wire up Web.Configure file.
Download from ELMAH GotDotNet Workplace
If you haven't got it implemented in your web application, you really should run and get it. Highly recommened.
]]>1st version of code using Response.Flush();
Response.ContentType = "application/binary";Response.AddHeader("Content-Disposition", "attachment; filname=" + MapPath(filename));
Response.WriteFile(MapPath(filename));
Response.Flush();
The downside of this code is that Response.Flush() on the code above would add the original html page file in the bottom of the download file, which we call it as extra junk. In order to avoid it, we can simply replace it with Response.End(); but you can't delete the file after downloading it (one of the reason why we need to delete it is the file is created on-the-fly and always needs to be up-to-date) because Response.End() ends the whole session. So we need to add "Content-Length", FileSize to chop off the extra junk. The following code also shows how to get the exact file size of the original file.
2nd version of code using Response.Flush(); with Content-Length and delete the original file after downloading
System.IO.FileInfo myFileInfo = new System.IO.FileInfo(MapPath(fileName));Response.ContentType = "application/binary";
Response.AddHeader("Content-Disposition", "attachment; filename=" + fileName);
Response.AddHeader("Content-Length", myFileInfo.Length.ToString());
Response.WriteFile(MapPath(fileName));
Response.Flush();
System.IO.File.Delete(MapPath(fileName));
Sharing Big Files on the Internet
It is not always easy to attach those big files to e-mail messages as the attachment limit for most ISPs is about 10MB. Don’t be disappointed - there are some slick –and free–Web sites for sending really big files. Both Dropload and YouSendIt let you send single files of up to 1GB in size.
...
see the full article here
MBSA 2.0 can identify security issues and missing updates for Windows 2000, Windows XP, Windows Server 2003, Internet Information Server (IIS) 5.0 and 6.0, SQL Server 7.0 and 2000, Internet Explorer (IE) 5.01 and later, and Office 2000, 2002, 2003, and Office XP.
]]>1. Learn to say, "I don't know." If used when appropriate, it will be often.
2. It is easier to get into something than it is to get out of it.
3. If you are not criticized, you may not be doing much.
4. Look for what is missing. Many know how to improve what's there, but few can see what isn't there.
5. Viewgraph rule: When something appears on a viewgraph (an overhead transparency), assume the world knows about it, and deal with it accordingly.
6. Work for a boss with whom you are comfortable telling it like it is. Remember that you can't pick your relatives, but you can pick your boss.
7. Constantly review developments to make sure that the actual benefits are what they are supposed to be. Avoid Newton's Law.
8. However menial and trivial your early assignments may appear, give them your best efforts.
9. Persistence or tenacity is the disposition to persevere in spite of difficulties, discouragement, or indifference. Don't be known as a good starter but a poor finisher.
10. In completing a project, don't wait for others; go after them, and make sure it gets done.
11. Confirm your instructions and the commitments of others in writing. Don't assume it will get done!
12. Don't be timid; speak up. Express yourself, and promote your ideas.
13. Practice shows that those who speak the most knowingly and confidently often end up with the assignment to get it done.
14. Strive for brevity and clarity in oral and written reports.
15. Be extremely careful of the accuracy of your statements.
16. Don't overlook the fact that you are working for a boss.
* Keep him or her informed. Avoid surprises!
* Whatever the boss wants takes top priority.
17. Promises, schedules, and estimates are important instruments in a well-ordered business.
* You must make promises. Don't lean on the often-used phrase, "I can't estimate it because it depends upon many uncertain factors."
18. Never direct a complaint to the top. A serious offense is to "cc" a person's boss.
19. When dealing with outsiders, remember that you represent the company. Be careful of your commitments.
20. Cultivate the habit of "boiling matters down" to the simplest terms. An elevator speech is the best way.
21. Don't get excited in engineering emergencies. Keep your feet on the ground.
22. Cultivate the habit of making quick, clean-cut decisions.
23. When making decisions, the pros are much easier to deal with than the cons. Your boss wants to see the cons also.
24. Don't ever lose your sense of humor.
25. Have fun at what you do. It will reflect in your work. No one likes a grump except another grump.
Impersonation is disabled by default. To enable it, you can just simple change the code to the following on Web.Config file.
<identity impersonate="true" />
And either disable the IIS Anonymous access from IIS directory security settings or add the following code to Web.Config file.
<authorization>
<deny users="?" />
</authorization>
This is to force the application to get the authentication token from IIS web server. And after getting the authentication, you can get the user name by programmatically reading the identity of the impersonated user.
[C#]
string username = System.Security.Principal.WindowsIdentity.GetCurrent().Name;
[Visual Basic]
Dim username as String = System.Security.Principal.WindowsIdentity.GetCurrent().Name
<script language="javascript">
<!--
var blnReturn = true;
function trapReturn(e)
{
var iKeyCode = 0;
if (window.event) iKeyCode = window.event.keyCode;
else if (e) iKeyCode = e.which;
blnReturn = (iKeyCode != 13);
}
// -->
</script>
and add the two event handler attributes to the form tag on the web page:
<form id="default" runat="server" onkeypress="trapReturn(event);" onsubmit="return blnReturn;">
However, it seems that it traps the mouse event as well. It had no response while I hit the button by click the mouse left button. So I added the third event handler attribute to the form tag, onmousedown="blnReturn=true;", which works great.
// get the char code of ENTER
char[] chars;
byte[] bytes = new byte[] {13};
System.Text.ASCIIEncoding ascii = new System.Text.ASCIIEncoding();
int charCount = ascii.GetCharCount(bytes,0,1);
chars = new char[charCount];
int charDecodedCount = ascii.GetChars(bytes,0,1,chars,0);
...
msgSearch.Text = msgSearch.Text.Replace(chars[0].ToString(), "<br>");
Basically, the first part of code is for getting the char for hard return (ASCII code 13), the second part is for replacing the hard return char in the text box to html return tag “<br>“. Works perfectly.
]]>Scott Hanselman's 2005 Ultimate Developer and Power Users Tool List
]]>We are working hard to improve printing in IE7 but we'd like to share some approaches to ease the pain when printing with IE today.
...
Our goal is to be able to print most web pages without losing any content using the default settings. For pages where this is impractical, we want to provide you with simple controls within print preview so that you can quickly and easily adjust the settings needed to print the way you want. We're still finalizing the details of the new functionality for printing but I will post an update once we get it locked down.
Those approaches are:
For developer, CSS @media rule can change the layout of the pages. This allows you to specify CSS attributes that get applied based on whether the page is displayed on screen or printed to paper.
Example:
@media print {
#menu, #logo, #sidebar {display: none; }
}
For end user,
- Adjust the size of the margins used when printing to make the content fit;
- Set the page orientation from portrait to landscape;
- Print part of a page...that is what I am doing the most right now.
If you want to take the hassle out of printing or if the suggestions above don't work on the pages you need to print, there are several Internet Explorer add-ons that might help.
Internet Explorer Fitted-Width Printing seems to be the best one and it is free while the other two are not. Hopefully, it will be addressed on the IE7 or at least improved. However, thanks IE group for these appraches.
P.S. Reading IE blog is fun, especially all these comments from all different people who love or hate IE. Highly recommended ... you will know what I mean after you read it.
]]>
- Notepad2 - a great enhanced text editor. A must. Personally, I use have notepad2 be your view source editor, and use add notepad2 to the explorer context menu.
- Cropper - a fabulous screen capture applet. Usually, PrtSc or Alt-PrtSc key does most of the job but I found it is a little bit inefficiency while I want to capture something from the remote desktop. And this does the job elegantly.
I have one loca drive C, one CD-RW drive D, and one virtual DVD-Rom E. Plus, I had a mapped network drive F at that day. And all sounds in my iTunes were sychronized to F: drive, which I didn't realized at the first place and found it accidently after a while when I was looking for the other files on that drive. Then I realized why my 6G iPod turn to 20G and no songs got copied over.
So in this case, I am assuming the "disk use" enabled iPod will take one of the drive letter from C to F and it doesn't seem to look for other spare letters. Wasn't sure the problem is due to the iPod software or Windows USB Plug-n-Play component, but would highly recommend that before connecting you iPod with "disk use" enabled to your computer, be sure there is at lease one drive letter from C to F is available. Otherwise, who knows what would happen?
Anyway, enjoy your cool tool
]]> Appearantly, Microsoft wants to enter into this area again. I recall that Microsoft had one similar product before called "Microsoft Photo Draw" that was published with Office 2000 but was discontinued before Office XP came to the market. According their said, this code-named 'Acrylic' is aimed at print, web, video and interactive media designers.
Appearantly, Microsoft wants to enter into this area again. I recall that Microsoft had one similar product before called "Microsoft Photo Draw" that was published with Office 2000 but was discontinued before Office XP came to the market. According their said, this code-named 'Acrylic' is aimed at print, web, video and interactive media designers.
I am using Macromedia Fireworks mainly for my web design work, and am currently reviewing some other programs to see which one is more workable for me, for example, Paint.net, Adobe PhotoShop Elements, Adobe PhotoShop, and this new Acrylic beta. Haven't tested a lot on this new beta, however, so far I still prefer Fireworks. I am not a professional graphic designer and all I want is to easily get my web design parts like logo, banner, polished text, icon, and button exported. So "Slice" is a must to have feature to me but not all programs could do it as easy as Fireworks does, PhotoShop Elements doesn't even have it. However, more program I learn more choices I can have in my hand.
]]>Since I don't know how to stop it or how to disable the track/pingback function if there is no way to stop those spammers, and don't have time to dig it deep to figure it out, I will just "delete blog_content where posttype = 4" periodically.
Anyone who knows the solution how to stop them, you are more than welcome to leave the comments here. I do appreciate your contribution.
]]>What should I say on this? Excited ... or upset? Maybe both. As an IT pro, I am excited and eager to learn the new technology. But as a new father, I felt upset as that probably means to reduce my time with my baby.
]]>Like Windows Update, Microsoft Update provides patches and updates for Windows products, but it also supports other Microsoft products, including Office and SQL Server.
Although there is no upgrade from SUS 1.0 to this new WSUS, you can migrate approvals and updates to WSUS. If you use multiple SUS servers to target updates to specific client computers, the WSUS migration tool enables you to consolidate approvals from specific SUS servers to WSUS computer groups.
]]>by Paul Robichaux
1. Assign a default recipient policy that assigns an SMTP proxy address that would be invalid on the Internet.
2. Assign a secondary recipient policy that assigns the correct SMTP proxy address.
3. Apply the secondary recipient policy to those users or groups who need to be able to send mail to the Internet.
4. Configure your Exchange server system to use one bridgehead to send SMTP mail to the Internet.
5. On that bridgehead machine, use sender filtering on the SMTP virtual server to drop any email from senders whose addresses match the default recipient policy.
question: it doesn't say what we should do if the main server and bridgehead machine are on the same computer.]]>
The freeware version, worth US$250, enables these features for three servers, as well as all the additions recently introduced in the latest version of GFI Network Server Monitor. New features include a totally new interface for fast and easy configuration, the capacity to monitor Linux servers, and the ability to check service availability by simulating a real service request (such as an actual terminal server login).
 Extensive checks for monitoring Linux servers have been included in GFI Network Server Monitor 6, released earlier this year. GFI Network Server Monitor can also check the status of a terminal server by actually performing a complete login to check if the session is established correctly. Similarly, it actually tests the status of a service as opposed to simply deducing the status from generated events. This is in stark contrast with other monitoring solutions, such as Microsoft MOM, that rely solely on events generated by the service.
Extensive checks for monitoring Linux servers have been included in GFI Network Server Monitor 6, released earlier this year. GFI Network Server Monitor can also check the status of a terminal server by actually performing a complete login to check if the session is established correctly. Similarly, it actually tests the status of a service as opposed to simply deducing the status from generated events. This is in stark contrast with other monitoring solutions, such as Microsoft MOM, that rely solely on events generated by the service.
"Our offer of a free three-server version of GFI Network Server Monitor provides small businesses, which would not normally make the investment, with an automatic network server monitoring solution. Administrators can monitor and receive alerts about critical machines such as their mail server, web server and file server for free," said Andre Muscat, Product Manager at GFI.
This is a great news to hear. I will definately give it a try to see how it is and share the experience here
]]>First of all, Hotmail uses what Microsoft calls SmartScreen technology, which the company explains as a probability-based system. While Microsoft didn't come right out and say it, SmartScreen sounds a lot like other commonly used Bayesian filtering systems. After enough data is collected the filter can become very effective at detecting junk mail by calculating a probability based on the words contained in any given email message. Microsoft relies on end users to provide feedback about the email they receive to help build a database than can be used to calculate probabilities.
Hotmail uses Symantec Brightmail, which relies on a "probe network" that is essentially a collection of about 200,000 email addresses. The addresses aren't used for any purpose other than to attractive junk mail, so any email received in the boxes are most certainly junk mail. Other Hotmail filters check messages to ensure they conform to common Internet standards as defined by relevant RFCs. Hotmail also allows users to configure their own whitelists and blacklists of email addresses.
A couple of other filters in use are Microsoft's Sender ID technology and IronPort System's Bonded Senders. Sender ID is basically a system that provides domain authentication to ensure email actually came from the domain as claimed by the sender. Bonded Senders is a program where people post a bond in order to be considered a legitimate sender of email. You can think of the program as a verified whitelist that can be used as the basis for the assumption that email from program participants is not unwanted junk mail.
Microsoft made a new service available, Smart Network Data Services, that is designed to let companies know how their networks fare in terms of mail delivery to Hotmail inboxes. So for an example, an ISP could request access to Smart Network Data Services and then look up their IP addresses. The results might show how much email came from those addresses as well as the results of the delivery attempts. Results could include how much of the email was considered to be junk and which IP addresses sent the junk mail. Such information could help ISPs located computers that are part of botnets or accounts used by spammers.
Another useful service that can be used by anyone is SenderBase, provided by IronPort Systems. SenderBase is a set of email-related data collected from over 50,000 organizations around the world. The data reveals which domains and IP addresses sent the most junk mail over a 24 hour period. As quick view of the data on May 26 showed the most heavily used networks for sending spam were Comcast Cable, whose users sent 403.2 million messages, and Yahoo!, whose users sent 304.7 million messages. Hotmail was in sixth position where some 109.5 million junk messages were sent during the same observed period of time.
 Attended couple of training sessions recently, this one that talks about the new organization system is the most useful one. I never happened to become a very organized person and ever thought will be even though I tried to find some better way, at least the suitest way to me, to improve this poor talent. This one might work for me. Well, at least worth to give a try.
Attended couple of training sessions recently, this one that talks about the new organization system is the most useful one. I never happened to become a very organized person and ever thought will be even though I tried to find some better way, at least the suitest way to me, to improve this poor talent. This one might work for me. Well, at least worth to give a try.
The 6D Organization System
Laura Stack, http://www.theproductivitypro.com
The Physical "Tickler" File Organization System:
- Create 43 hanging files, 12 for the months, 31 for the days.
- Hang them in your closest, most accessible drawer (so you don't have to get up to get at it).
- Put the current month first, and the current day right behind it. Then the following days until the end of the month.
- Put the next month behind the last day of this month.
- As you pass a day, put that day's file behind the following month.
- Put the rest of the months in order behind the second month.
Use the 6D method for paper:
1. Delete
2. Delegate
3. Do it if < 3 minutes
4. Date/Defer
5. Drawer
6. Deter
Once you touch a piece of paper, use the "Super-Glue" method, i.e. it is stuck to your fingers until you decide what to do with it.
Different Types of Files
1. Tickler file (active/follow-up) - for things "to do"
2. Contact management file - likely contacts in Outlook, but also physical files or Rolodex, business card file, etc.
3. Client/customer files.
4. Project files - current files of projects your are working on.
5. Idea files - for things you don't want to throw away that might be good ideas for the future
6. Topical files (to read) - for information about specific topics that you may want to refer to the future.
7. Reference (permanent) files - for work completed in teh current year/period.
8. Archive (history) files - old files that you haven't touched for a year. You should go through your files each year and pull out anything you haven't touched in a year. You may be able to destroy them, or you may want to put them in a bankers box and put them in file room storage or offsite.
I just spent an hour or two to build the system...so let's see how it goes. Actually, it requires a lot of hanging files, which cost a bit of money.
]]>Whoppix is a stand alone penetration testing live cd based on Knoppix. With the latest tools and exploits, it is a must for every penetration tester and security auditor. Whoppix includes Several exploit archives, such as Securityfocus, Packetstorm, SecurityForest and Milw0rm, as well as a wide variety of updated security tools. The new custom kernel also allows for better WIFI support, for tools such as Aireplay.
The Whoppix site has some demos online that you can watch, such as brute force cracking the login ID and password for a MySQL server and cracking WEP keys in 10 minutes. The demos are basically live animated screen captures that show the use of some of the tools included with Whoppix. Watching the demos is essentially like watching a short movie, and they're effective and to the point.
]]>Windows IT Pro - InstantDoc #46381
Although most of the major Windows Server 2003 Service Pack 1 (SP1) changes concentrate on the core OS, SP1 doesn't neglect Microsoft IIS. The service pack contains several significant enhancements to Microsoft Internet Information Services (IIS) 6.0, the Web server application that's bundled with Windows 2003. Those changes include
- Secure Sockets Layer (SSL) support in kernel mode—SP1 moves SSL support into the kernel, yielding about a 50 percent performance improvement for serving SSL Web pages and using SSL to run Windows 2003 Terminal Services.
- format changes for log files—SP1 makes more information available in IIS’s httperr(x).log files. A new registry setting lets you log application pool name-related events.
- metabase auditing—In an important enhancement, SP1 lets you track changes in the IIS metabase (an XML file that stores IIS configuration information).
- tracing—Probably SP1's biggest improvement to IIS is its new tracing capability. Pre-SP1 IIS 6.0 essentially functioned as a black box: You could use Netmon to see request events arrive, but you had no insight into how IIS handled those requests. The new tracing capability lets you diagnose Web application and Web server problems by exposing a view of the events that are taking place within the Web server.
See more detail about Windows Server 2003 Service Pack 1 here
]]>Now I am using Google a lot instead. By simply typing the problem into the text box just like before, I could easily find the right solution not only from Microsoft but from other resources as well, for example, the blog, especially the bloggers who have MVP title with them. Great appreciate what the effort they have been providing!
What I can say about the Google, which is still my first choice!
]]>What is casuing the problem?
Earlier versions of IIS include a wildcard character MIME mapping, which permits IIS to serve any file regardless of its extension. IIS 6.0 does not include this wildcard character MIME mapping and does not serve any type of extension that is not defined at the MimeMap node in the IIS metabase.
What is the solution
To define a MIME type for a specific extension, follow these steps:
1.Open the IIS Microsoft Management Console (MMC), right-click the local computer name, and then click Properties.
2.Click MIME Types.
3.Click New.
4.In the Extension box, type the file name extension that you want (for example, .msg). You can also put "*" here If you want to serve all files regardless of the file name extension. However, it is not recommended.
5.In the MIME Type box, type application/octet-stream.
6.Apply the new settings. IIS now serves files with the extension that you added. In this example, IIS now serves files with the .msg extension.
IIS 6.0 Does Not Serve Unknown MIME Types
notes: this solution is not particularly for opening .msg file. It should work for any file that has the extension name that is not defined as MIME type on the IIS 6.0.
]]> ]]>
]]> Guess what I got on Monday...yeah, an iPod, the coolest toy in the world. I even got a whole set of accessories, including the case, charger, and cool iTrip. In case anyone of you doesn't know what it is, here explains what it is.
Guess what I got on Monday...yeah, an iPod, the coolest toy in the world. I even got a whole set of accessories, including the case, charger, and cool iTrip. In case anyone of you doesn't know what it is, here explains what it is.

Griffin iTrip iPod mini
Your iPod mini can play music through your car radio with the iTrip FM Transmitter, which connects to the headphone and remote jacks of your iPod mini.
My iPod is blue...yes, my favorate color, and with my name laser graved on the back...cool, that is my own toy now. Big thanks to the couple who gave me this gift, they really know what I like.
]]>]]>
LSoft Technologies' Active@KillDisk
]]>how to remotely enable remote desktop
comment: it didn't mention if it works for Windows XP Pro. However, it works.
]]>

Many free (or nearly free) break-in tools are readily available on the Internet. You can easily find these utilities by searching the Internet with the keywords break-in tools.
You should take a quick look at the free break-in utilities for two reasons:
1. The quantity, general availability, and feature set of these tools should give you a wake-up call to physically secure your servers and defend against their potential use in your environment.
2. You might find some of these tools useful and wat to try them in a test environment.
Here's a sampling of free tools that will probably keep you awake at night:
Adanced Windows Password Recovery enables recovery of logon passwords, Microsoft .NET passport passwords, stored user passwords, RAS and dial-up passwords, passwords to VPN connections, and passwords and access rights to shared resources.
http://www.elcomsoft.com/awpr.html
Austrumi is a Linux bootable .ISO image for recovering Windows NT passwords.
http://sourceforge.net/projects/austrumi
Emergency Boot CD is a bootable CD-Rom that lets you perform emergency boots, recover the Master Boot Record (MBR) of hard disks, and change the password of any local user account. The tool also lets you recover deleted files, perform disk wipes, recover data from an accidentally formatted disk, and copy and move files.
Offline NT Password & Registry Editor lets you change the password of any local user account. It works offline, so you boot from a floppy disk or CD-Rom.
http://home.eunet.no/~pnordahl/ntpasswd
XP Password Cracker doesn't change an Administrator password, but it tells you the existing passord for that account.
]]>1. Create the Correct Size Icon
For Internet Explorer 5, the required size of a shortcut icon is 16x16 pixels. To create the icon, use an icon editor, such as the one included in Microsoft Visual Studio or one of the many other icon editors available. Regardless of the program you use, make sure you set the editor to create an icon that is 16x16 pixels. Otherwise, the icon will be ignored by Internet Explorer.
2. Associate the Icon with Your Web Page
After creating the icon, you must associate it with your Web page. One way is to save the icon with the default file name of favicon.ico in the root directory of your domain - for example, www.microsoft.com/favicon.ico. Each time your Web page is added to a user's favorites, Internet Explorer automatically searches for this file and places the icon next to all the favorites and quick links originating from your site.
You can also associate the icon with your Web page by saving the icon with a file name other than favicon.ico and adding a line of HTML code in the head section of your Web document. The line of code includes a link tag that specifies the location and name of the file. You can include this link tag on a per-page basis.
<link href='http://www.mydomain.com/myicon.ico">
]]>Don't know which patch caused this but will find later...

Update: Just found that the additional option on the shutdown window shows up only when there are updates available to install.
]]>

Bill Gates' Living Room
]]>Writing an Incident Handling and Recovery Plan
by William Lynch - Senior Consultant for CTG's Information Security Services Practice - Wednesday, 16 March 2005.
Introduction
While many websites and papers discuss incident handling and incident response plans, aside from RFC 2350 very few of these lay out exactly what an actual plan might look like. The following is an outline of a typical generalized incident handling and response plan for a small to mid-sized organization that doesn't have a dedicated incident response staff. Using this outline as a starting point, the reader will need to adapt sections to his or her organization or industry as necessary and flesh out the plan in detail in order to create an adequate customized plan.
Incident Handling and Recovery Plan Outline
- Definitions
- Incidents - What constitutes an incident?
- Classification - What type of incident has occurred? Explain each category below.
- Loss of confidentiality of information
- Compromise of integrity of information
- Denial of Service
- Misuse of Service
- Damage to Systems
- Priority and Urgency - Identify the response level of effort (LoE) for a given type of incident. These may be reordered to suit the organizations needs.
- Threats to the physical safety of human beings
- Root or system level attacks to any host or system
- Compromise of restricted confidential service accounts or software areas
- Denial of service attacks to infrastructure, confidential service accounts or software areas
- Any of the above at other sites which originate from the organization’s systems
- Large scale attacks of any kind (worms, sniffing attacks, etc)
- Threats, harassment, or criminal offenses involving individual user accounts
- Compromise of individual user accounts
- Compromise of desktop systems
- Forgery, misrepresentation, or misuse of resources
- Classification - What type of incident has occurred? Explain each category below.
- Incident Response Team (IRT) - Who will respond to the incident?
- Mission Statement - Why does the team exist and what is its purpose?
- Roles and Members - Who should be on the team?
- Leader - Primary coordinator and point of contact
- Management Sponsor - Lends authority to help minimize "red tape" barriers
- Systems Engineer - Responsible for affected systems
- Network Engineer - Responsible for affected networks
- Public Relations Advisory - Interfaces with the public as necessary
- Legal Advisory - Provides advice for differing legal courses of action
- Incidents - What constitutes an incident?
- Incident Handling Process
- Determine if an incident has occurred - Some activities may not warrant IRT action
- Contact the IRT Leader
- If the IRT is to be activated, the Leader documents the discovery
- Contain the Incident - Prevent problems with affected areas from spreading
- Identify and isolate the area under investigation
- Notify law enforcement personnel and legal advisory if applicable
- Notify Public relations advisory if necessary
- Document containment information
- Eradicate the Incident - Put an end to whatever caused the incident
- Gather evidence
- Identify the source of the incident
- Determine the full extent of the incident
- Implement stopgap measures to eliminate any active threats
- Update documentation with eradication information
- Determine if an incident has occurred - Some activities may not warrant IRT action
- Recovery Process and Follow-Up
- Assess damages - Determine the impact of the incident to the organization
- Identify the affected systems and networks
- Identify the affected data
- Identify possible courses of remediation
- Reverse damages if possible - Minimize the costs, both tangible and intangible, associated with the incident
- Restore affected data from backup
- If necessary Public Relations Advisory establishes a plan to customer and public faith
- Nullify the source of the incident - Prevent recurrence of the same incident
- Patch any open vulnerabilities
- Improve access restrictions to the affected areas
- Further remediation as necessary
- Review the Incident - Learn from the mistakes
- Determine why the incident was able to occur
- Determine if the appropriate safeguards are in place to prevent recurrence
- Determine the risk level of similar incidents to other information assets
- Review the Incident Handling Plan - Adapt and increase efficiency in the response process
- Validate that the incident handling and response plan was appropriate
- Modify the incident handling and response plan with new insight gained
- Documentation - Keep tidy records, as they will almost certainly be needed again
- Create final documentation of the incident in an appropriate level of detail
- Perform debriefings of the IRT, if necessary
- Reporting - Assist others in disaster aversion
- If necessary, report the incident to industry regulation boards
- Assess damages - Determine the impact of the incident to the organization
- Incident Examples - Description of the plan in action will help all parties to fully understand the plan
- Physical Security Breach - Describe how the plan would be applied during a physical security breach
- External Network Breach - Describe how the plan would be applied during an external breach
- Internal Network Misappropriation - Describe how the plan would be applied to misuse of resources
- Appendix
- Table of Contact Information for IRT Team members
- Flow diagram of the incident handling process
| Registry Settings |
| User Key: [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer] System Key: [HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer] Value Name: NoRecentDocsHistory Data Type: REG_DWORD (DWORD Value) Value Data: (0 = disable restriction, 1 = enable restriction) |
]]>
Spam URL real-time blacklists (SURBL) checking, to detect spam based on URLs in the message body. Links or domains are extracted from the message body, these are then queried to check whether they are listed on public spam URL blacklists such as sc.surbl.org. More information on SURBL can be found at http://www.surbl.org.
Configure custom real-time blacklist (RBL) servers and multiple DNSRBL servers, add their own, and define the order of priority of servers to be checked. This improves on the product's existing third party DNS blacklist checking module.
A new senders feature provides users with an instant view of emails sent from people they never had previous (email) contact with. This helps users better organize emails in their email client, as well minimize false positives.
A detail list of new features available in GFI MailEssential fro Exchange/SMTP 11
]]>Bluestumbling, Bluesnarfing, and Bluejacking
Bluestumbling is the process by which you can discover other Bluetooth devices around you, in particular, devices taht are either operating in Security Mode 1 or are flawed and allow access to services without authentication.
Bluesnarfing is the practice of obtaining information from a Bluetooth-enabled device without first pairing with it.
Bluejacking is an abuse of the Object Exchange (OBEX) profile that is intended to be a means of exchanging data between two Bluetooth-enabled devices without requiring authentication.
Securing Bluetooth
A basic security rule is to disable anything you don't need or use from your Bluetooth-equipped devices.
If you must leave Bluetooth enabled, I recommend ensuring that your device isn't discoverable.
If you need to pair Bluetooth devices, I recommend never doing so in a public place. Instead, pick somewhere quiet where there's little chance of someone eavesdropping on Bluetooth radio signals.
When pairing devices, you should use authentication and encryption on the link between devices, where possible.
If you pair mutlple Bluetooth devices, I recommend selecting a unique, random passkey for each pairing. If a pairing is lost or broken and you need to pair the devices again, I recommend using a different passkey.
Finally, when procuring Bluetooth devices, do some research into the security of the devices you're considering.
]]>C# Open Source - http://csharp-source.net/
Free Conference - http://www.freeconference.com/
SqlBuddy - http://sqlbuddy.sourceforge.net/
NSurvey - http://www.nsurvey.org/
Orthogonal Toolbox - http://www.orthogonalsoftware.com/products.html
]]> Based on the feedback, Fyodor published “The Top 75 Secruity Tools,” which you can find at http://www.insecure.org/tools.html. NST includes most of these tools.
Based on the feedback, Fyodor published “The Top 75 Secruity Tools,” which you can find at http://www.insecure.org/tools.html. NST includes most of these tools.
When you reboot a system with the NST CD-Rom loaded, a trimmed-down version of Redhat Linux9 opens. After the OS is running, you can access the tools on the CD-Rom through the local console, through a serial connection, via the network from another system, or through a web browser.
]]>source: Sysinternals Freeware
What is a Rootkit?
The term rootkit is used to describe the mechanisms and techniques whereby malware, including viruses, spyware, and trojans, attempt to hide their presence from spyware blockers, antivirus, and system management utilities. There are several rootkit classifications depending on whether the malware survives reboot and whether it executes in user mode or kernel mode.
Persistent Rootkits
A persistent rootkit is one associated with malware that activates each time the system boots. Because such malware contain code that must be executed automatically each system start or when a user logs in, they must store code in a persistent store, such as the Registry or file system, and configure a method by which the code executes without user intervention.
Memory-Based Rootkits
Memory-based rootkits are malware that has no persistent code and therefore does not survive a reboot.
User-mode Rootkits
There are many methods by which rootkits attempt to evade detection. For example, a user-mode rootkit might intercept all calls to the Windows FindFirstFile/FindNextFile APIs, which are used by file system exploration utilities, including Explorer and the command prompt, to enumerate the contents of file system directories. When an application performs a directory listing that would otherwise return results that contain entries identifying the files associated with the rootkit, the rootkit intercepts and modifies the output to remove the entries.
The Windows native API serves as the interface between user-mode clients and kernel-mode services and more sophisticated user-mode rootkits intercept file system, Registry, and process enumeration functions of the Native API. This prevents their detection by scanners that compare the results of a Windows API enumeration with that returned by a native API enumeration.
Kernel-mode Rootkits
Kernel-mode rootkits can be even more powerful since, not only can they intercept the native API in kernel-mode, but they can also directly manipulate kernel-mode data structures. A common technique for hiding the presence of a malware process is to remove the process from the kernel's list of active processes. Since process management APIs rely on the contents of the list, the malware process will not display in process management tools like Task Manager or Process Explorer.
Well-known Sysinternals Freeware developed a free tool called RootkitRevealer, an advanced root kit detection utility that might be able to find rootkits on your systems. It runs on Windows NT 4 and higher and its output lists Registry and file system API discrepancies that may indicate the presence of a user-mode or kernel-mode rootkit. The tool is relatively new and still under development, however you can try it now by downloading a free copy from their website.

see the more details about RootkitRevealer here
comment: it seems to find the false positives if the computer is set as using the different language. My computer has Chinese language set as the default, the tool found a couple of false positives named in Chinese.
]]>see the full article here written by the Microsoft Regional Director of Chennai
]]>quote from Microsoft abotut What SAM is
By engaging in software asset management you can streamline processes, reduce costs, and enhance reliability and security. While software inventory and tracking are integral parts of SAM, so are the policies, procedures, technologies, procurement, delivery, deployment, and support of a company's software assets.
Implementing a SAM plan involves three main steps:
![]() Perform a Software Inventory
Perform a Software Inventory
In this step you take a survey of all software installed on your company’s PCs, workstations, servers and other devices and collect the information in a report. The inventory can be performed manually or you can use software inventory tools to perform inventories automatically.
![]() Match Software Installed to Licenses Acquired
Match Software Installed to Licenses Acquired
Once you know which software titles are installed on your company’s computers, you can find your license documentation and match it to the software installed. This will make it easy to see if you are over-licensed or under-licensed for certain software titles.
![]() Review Policies and Procedures
Review Policies and Procedures
Once you know what you have and where it is, the next step is to review or write policies and procedures that your company’s employees can use to ensure proper software asset management. Topics you may cover include the acquisition, deployment, use, and recovery of software.
![]() Develop a SAM Plan with Proper Documentation
Develop a SAM Plan with Proper Documentation
The final SAM step is to establish a baseline and plan for ongoing software management.
download the documents here to get all the information you need to get a SAM plan started
comment: As a system administrator, I feel how much pain I have to manage the software asset. The tool is not solving the whole problem for you but is a good start to help you collecting the information. At least, it would tell you how many Microsoft products you have in your network.
]]>

comments: the whole idea is quit neat, using SNMP rather than agent to retrieve the data from the target machine, but the installation part is quit disappointing, more sad thing is that it even asks to remove IIS from the computer. I bet this part will eliminate a lot of IIS fans including me.
]]>
- Flash animation filter
- Built-in pop-up stopper
- Additional mouse functions - very cool one
- Multi-window browsing
- Real full screen mode and alternative full desktop mode
- Built-in Yahoo/Google search engine
- Full IE compatibility
- Records cleaner
- Safe recovery
- Skins - give you different nice-looking face if you are bored with IE
The network will allow companies that have become victim's of phishing attacks to report fraudulent Web sites to the network's centralized database. Companies can also join the network to receive aggregate reports of fraudulent sites which can then be used as data for content management systems (such as Web and email filtering software) that could block access to the fraudulent sites, thereby preventing users from becoming victims of fraud.
But such aggregate data won't come cheap. A spokesperson for the Phish Report Network told Windows IT Pro Magazine that participation in the network costs $15,000 USD per year.
Techworld.com (09 Feb 2005)
A dangerous spoofing security hole has been found in every browser on the market — except one.
Mozilla, Firefox, Safari, Opera and Netscape all suffer from the "moderately critical" vulnerability that allows the spoofing of address bar URLs and SSL certificates, but, incredibly Microsoft Corp.'s Internet Explorer gets a clean bill of health.
Publicized by security company Secunia, the flaw affect the range of browsers using the open-source Geko browser kernel. Anyone using an affected browser would be able to visit spoofed Web sites without being aware of it, something that would aid any crime based on setting up bogus websites, such as phishing.
On my first post, I only mentioned the software called ManageEngine OpManager 5.5 from AdventNet but didn't put any comments on it because I haven't got chance to do a test even a quick one at that time. Now, today I finally got the time to get it downloaded and installed on my test computer. Looks really good!! The installation procedure is very straightforward but before running it you have to do some configurations on the server you want to monitor to load the SNMP so that the OpManager could retrieve the data from the monitored server. That is something cool actually because a lot of similar software I used before require to install a client/agent on the monitored server to be able to send or receive the data. Windows 2000 and 2003 Server even NT all have this SNMP component available by default but you have to install it from Add/Remove Programs. Once you have this all set up, you can either launch a windows client or web-based client to manage it, add nodes, alerts, monitors, etc. a lot of things you can monitor from the program.
The another thing about this tool is the cost, free for monitoring 10 nodes, $795 for one user to monitor unlimited nodes, very very attractive for the small, and medium business.
]]>Antispam Solutions
A. Filtering at the client
Many antispam solutions install on a user's PC alongside an email client (e.g., Outlook, Eudora). This type of solution is usually easy to deploy for an individual user, and it has an immediate beneficial effect on the user's productivity. However, it is not suitable for enterprise level. An example of this type of solution is Qurb from:
B. Filtering at the email server
This solution deals with spam at the email server end before they arrive in a user's inbox. But they do this at the expense of creating extra work on the servers; you need more queues and processing power. The spam messages still have to travel the length of your email system before they are detected, so there is no beneficial effect outside the server environment. An example of this type of solutions is Microsoft Exchange Inelligent Message Filter at:
http://www.microsoft.com/exchange/downloads/2003/img/
C. Filtering at the Internet Gateway
Many vendors provide spam-filtering solutions that work at the point that email messages enter your organization. Some of them are software products that install on a standard Windows or UNIX server; others are all-in-one appliances that plug into the right place in your network and that you configure and manage through a web interface.
These solutions provide a good level of relief to your email infrastructure. If spam can be dealt with at the gateway, it doesn't clog up your email servers or your internal network infrastructure. Gateway solutions require some reconfiguration of the way email traffic flows into your company and you should be aware that a spam-filtering gateway can become a single point of failure for your email network. An example of this type of solutions is GFI MailEssential from:
D. Filtering outside your network
A filtering solution provided away from your network by a managed service provider (MSP), has the features of the gateway offerings but also has some extra benefits. A simple change to the DNS records for your domain will cause all your email traffic to be delivered by the MSP's resilient servers. Those servers filter the email traffic for spam and only deliver to your gateway the mail you actually want to receive. No unwanted traffic flows through your Internet connection. An example of this type of solutions is Postini Perimeter Manager at:
Spam Detection Technology
The spam detection landscape, which is constantly evolving, has been likened to an arms race. As antispam developers come up with a new technique to recognize and block spam messages, the spammers counter this with new methods of their own to get around the filters.
Content tests
- Keyword checking
It used to be an effectifive measure - messages that contained particular words were easily recognized as spam. But now this simple filters are no longer very effective. - Bayesian
It happened to be the most effective way of detecting the spams by testing the content. Some solutions, using Bayesian algorithms that analyze the patterns of words found in spam and non-spam messages, are able to predict whether a message is spam based on evidence from all the previous messages they've seen. Another words, it needs to be trained before acting as a good detective.
Connection-level tests
Those methods above rely on being able to analyze the content of an email message. But recently, spam senders have been able to bypass this kind of analysis by sending messages that have little or no spam content. These spam messages may, for example, only contain a URL that loads an advertisement into the message from a remote web server when the receiver views the message.
Fortunately, there are other mechanisms for detecting spam, which rely on the characteristics of how a message arrived at the server, for example, which IP address it came from, what other recipients it was sent to, whether other people have received spam messages recently from the same source, how well the sending server complied with established SMTP protocols, and so on. These connection-level tests can be very effective at detecting spam messages, regardless of whether they have any content that can be analyzed.
- DNS Blacklist
- Header Checking
- SPF (the Sender Policy Framework) - the new technology developed to fight with those spams sent from the forged sending addresses as most of today's spammers spoof email addresses. Visit http://spf.pobox.com for more information.
- Directory Harvesting
A good antispam solution needs to apply these connection-level tests, as well as content tests, to give you good protection. Gateway and MSP solutions that intercept the email traffic on its way to your network, are well placed to cover both angles.
Consideration
When you start thinking about putting the solution in-place to prevent the spam, first of all you have to consider which kind of solution is suitable for your organization. I highly recommend the solution C unless your organization doesn't have proper person to manage it and the message flow is not that high confidential.
Secondly, you have to choose the right software/hardware, a good software/hardware should include the feature like below. Personally, I would vote GFI MailEssential product as the best.
- Auto-whitelist - to minimize the on-going false positives.
- Bayesian - to catch the most content-based spam.
- DNS Blacklist
- Header Checking
- Flexible configuration to tune the filter like learning mode, more setting on each feature listed above, etc.
Thirdly, once you decide which solution is going to be used and which software is going to be in-placed, you have to make a detail plan how to get it implemented seamlessly. A bad plan will turn your whole job down whether you choose the right solution and software or not. Plan it as much detail as you can ahead and do it as much carefully as you can after would definately accomplish your project successfully. Also, every anti-spam software needs to be tuned and trained to achieve their best performance, so be prepared properly would turn down the trouble to the minimum from the beginning.
- Prepare a company customer email list and import it to the whitelist.
- Run the bayesian learning wizard to scan some existing mailboxes' sent folder to raise the number of the legitimate in bayesian database before enabling it.
- Do not set up to delete the spam, instead, set up to forward to a central mailbox and assign a person to monitor it at least for a couple of weeks.
- Adjust the other settings on keyword checking, header checking to make sure it works on your situation.
- Turn on the auto-whitelist.
- Move missed spams to spam folder to improve the database for the future.
- Move false positives to legitimate folder to improve the database for the future.
Finally, I hope we all can win the battle and say "There is no door here for you" to all spammers.
Tips. not every software says they can turn on filter for these users and turn off for the others. However,here is the trick you can accomplish it on most of products. If you want exclude a user from spam filtering, simply enter the email address of the user, and select MIME TO option.
]]>Google News Alerts
It is essentially an online newspaper clipping service that continually browses over 4,500 news sources. You may want to use it to keep tabs on a spcific industry or technology - or even a competitor.
Salesforce
Salesforce.com offers a customer relationship management (CRM) product that is popular with larger enterprises. What many small businesses don't know is that there is a personal edition available for free on their website. And it should provide enough information for you to decide whether you want to upgrade to the full-featured version in the future.
http://www.salesforce.com/products/personal.jsp
Constant Contact
Most small businesses cannot afford to afford to outsource a monthly email newsletter. While there are many web based email marketing services available, Constant Contact seems to be incredibility popular with do-it-yourselfers. Their solution is designed to be affordable for small businesses as monthly fees are based on the number of subscribers on your list.
]]>Spyware is the general term used to describe any software which employs a user's internet connection in the background without their knowledge or permission. These agents can be:
- Adware - displaying advertising while a program is being run;
- Malware - modifying system settings and running unwanted tasks;
- Hijackers - redirecting your browser to web sites;
- Dialers - dials a service such as a porn site and sticks you with the bill or
- Collectware - collecting information about you and your surfing habits.
Detecting Spyware
Chances are, if you have been on the internet for any great length of time, you will have some type of spyware on your computer. It can come from opening spam email, clicking on an innocent-looking pop-up window, downloading a free utility, or even just visiting a new website. Some indications of spyware infection include:
- a different start page for your browser;
- more pop-up advertising than usual (even while offline);
- internet connection seems sluggish;
- your search engine redirects you to unfamiliar sites;
- unusual additions to your browser (new links or toolbars).
Solutions
Prevention being the best cure, one of the best things you can do about spyware is to install a personal firewall. A good firewall from a manufacturer like Zone Alarm or Norton will allow you to surf the net virtually invisible to others (it's hard to harm you if they can't see you!). These firewalls can monitor for any unusual activity or transmission to and from your computer and, in the case of spyware, will let you know if a program is attempting to relay information to an outside location.
Additionally, you can adjust your internet browser settings to prevent unwanted programs being downloaded and malicious code to be run. Keeping your operating system up to date is a good way to keep your system clean and healthy.
Of course, if you know you already have spyware, then the best action is to install a spyware-detecting program and just “see whatcha got“! Good programs include the free Ad-Aware by Lavasoft and AntiSpyware (doesn't have real-time protection on free version), a free beta program just released from Microsoft (does have real-time protection on this beta version but not sure if it is on the final release). Be sure to get the latest definition files, as these scanning applications are only really useful when they are aware of the latest spyware developments.
Also, it seems hard to find a good version for enterprise level like Symantec Antivirus Corp Edition which provides the central location to manage all the workstations in a enterprise environment. Anyone knows any good one on this level, please be kind to share it here.
]]>Promqry and PromqryUI can accurately determine if a modern (Windows 2000 and later) managed Windows system has network interfaces in promiscuous mode. If a system has network interfaces in promiscuous mode, it may indicate the presence of a network sniffer running on the system.
Promqry cannot detect standalone sniffers or sniffers running on non-Windows operating systems.
System Requirements
- Supported Operating Systems: Windows 2000, Windows Server 2003, Windows XP
- Microsoft .Net Framework
The following map shows the direction how to get to my home from my work place, looks quite stupid (seems take 10 miles more than the normal way I was taking) but maybe faster even though I doubted because crossing the Lion Gates Bridge is not easy at the rush hour. Well, but it is still good because people always needs the map and direction when they need to go to the place they don't know or aren't familar with.

I am on the team of one too and often found that it is such a pain to track this things down but I have to. Right now, I was using an internal only .Text blog site to record but it doesn't help me that much so I wish there are some good tools out there could do much better. Thanks Scott and the comments posters, the information you provided would really help me out of this. I have taken a quick look at these, and found Gemini from CountSoft is pretty good. It is free for 10 users and is based on ASP.net and MS SQL server, which I mostly prefer to use. I will give it a try shortly and hopefull can work out for me.
]]>InstantDoc #45074 at WindowsITPro.com
A lot of thought goes into provisioning and maintaining employees' mailboxes, but little thought typically goes into what to do with those mailboxes after their owners leave the company.
Maintaining a former employee's mailbox is a good idea for many reasons. The mailbox might contain important messages and documents, so deleting it could erase quotes or proposals related to active projects or important messages that haven't been opened.
Nine Exchange configurations and options can help you balance functionality, system stability, and resources when you close out mailboxes.
- Disable, don't delete - you need to have some sort of policies in place to decide how long to keep closed-out mailboxes online.
- Hide the mailbox and review access.
- Turn off rules.
- Configure out-of-office notifications.
- Change the SMTP address.
- Disassociate DLs - recommend to remove the account from distribution list (DL) memberships if you're concerned about storage space and don't want the account to receive messages.
- Stop all mail - to prevent the mailbox from accumulating new messages, assign an empty DL as the alternate recipient for the mailbox.
- Save the mailbox contents - export the content of the mailbox to a .pst file, which provides one more level of recoverability if you need to access the mailbox contents later.
- Deal with legacy delivery - configuring recipient filtering is a simple and easy way to block messages sent to legacy addresses over the Internet.
InstantDoc ID 44693
WindowsITPro
Phishing scams hijack big-name brands and use customers' trust in those brands to convince people to divulge personal financial information such as usernames, passwords, Social Security numbers, and credit card numbers.
...
I listed the 10 most common phishing attacks. If any of these appear in your inbox, don't be fooled.
10. Westpac - subject: Security Server Update
9. Halifax
8. AOL - subject: Confirm AOL billing info
7. Barclays
6. Lloyd's
5. Fleet - subject: New Security Standards for Customers
4. PayPal - subject: PayPal account limited
3. US Bank - subject: Bank Fraud Verification Process
2. eBay - subject: Verify your Account
1. CitiBank - subject: Maintenance upgrade
| • |
Generate a list of issues, such as suboptimal configuration settings or unsupported or nonrecommended options. |
| • |
Judge the general health of a system |
| • |
Help troubleshoot specific problems |
Microsoft Exchange Server Best Practices Analyzer Tool main page
]]>ManageEngine OpManager is a network monitoring software that offers combined WAN, Server and Application monitoring. OpManager automates several network monitoring tasks and removes the complexity associated with network management.
]]>by Raymond Chen
By default, the Background Intelligent Transfer Service (BITS) which is used by Automatic Updates will use idle network bandwidth for downloading updates. This is normally not a problem.
One case where it can be a problem is you have a large LAN that shares a single DSL connection. BITS doesn't see that that DSL connection is shared. Consequently, each computer on the LAN will be using its idle network bandwidth to download updates and the total of all the LAN computers doing this will eversaturate the DSL connection.
Another example where this can be a problem is if you have a network card that connects to a hardware firewall which in turn uses a dial-up modem to connect to the Internet. (For example, you might connect through a classic Apple AirPort which is in turn connected to a modem.) BITS sees your fast network card and can't see that there is a bottleneck further downstream. As a result, it oversaturates the dial-up connection.
To tweak the BITS settings, you can fire up the Group Policy Editor by typing "gpedit.msc" into the Run dialog. From there, go to Computer Configuration, Administrative Templates, Network, then Background Intelligent Transfer Service. From there you can configure the maximum network bandwidth that BITS will use. You can even specify different BITS download rates based on time of day, so that it downloads more aggressively while you're sleeping, for example.
As Seth Godin points out, blogs only work when they meet four of the following five conditions:
- Candor
- Urgency
- Timeliness
- Pithiness
- Controversy
Well, I can't fully agree with that. Everyone has their own reason, purpose to have their own blog. That “only work” word completely misunderstands what the blogs' spirit is. But overall, this is a quite good article.
]]>Why not let someone else collect and configure several worthwhile tools into a ready-made, portable toolkit? Many savvy administrators are doing just that. Numerous toolkit developers and organizers are using Linux, which lets them customize the OS around their chosen suite of tools, to make bootable CD-ROM toolkits. One such kit is the free Auditor security collection, a set of security tools and utilities organized into the following categories: Footprinting, Scanning, Analyzing, Spoofing, Bluetooth, Wireless, Bruteforce, and Password cracker. If you haven't yet created a security toolkit, Auditor is a great place to start. Those who already have a kit will find it an able, easy-to-use platform, with a few caveats (be sure to read the sidebar "Before You Begin,").
]]>Yes, .Text does lack some good features. However, there are numbers of people have done a lot of wonderful job to get the .Text better and better. Search on .Text based blog is the most lacked part on .Text world. The one on Ryan Farley's blog is the most easiest and impressive one I have ever found. It uses Google or MSN's RSS search feature and Scott Mitchell's RssFeed ASP.Net Server Control to show the content indexed on the search engine (another word, anything that hasn't been indexed yet can't be found), not perfect but very good. Also I have noticed that the pre .Text 0.96 version has the full-text search feature build-in but I haven't happened to implement it successfully. I am hopping there are someone out there could do something on it as anyone of you could find it is hard to find your own stuff while it gets bigger. Right now, I developed a piece of code to give me the ability to search my stuff, not full-text searchable but at least gives me something.
Here are some of them...(it can't be a complete list, instead, it is just something I came cross and found from the Internet)
Skin:
RoudyBob.net .Text Skin Catalog
Calendar
Giving .Text a Calendar view from Scott on Writing
Calendar Control from Scott Watermasysk
An improved calendar for .text from Scott Willeke
Comment Spam Block
Preventing .Text blog spam using triggers
CAPTCHA Image Control for .Text
Search
]]>What is it?
Paessler Site Inspector is a comprehensive set of website and web page analysis tools. This web page analyzer is the perfect companion for people creating websites or working with the Internet. Site Inspector brings various analysis techniques and selected online resources together in one place and plugs them into the application already running on your desktop when you surf the Web: Internet Explorer.
What does it do?
Site Inspector adds a toolbar and several new menu items to the context menu of Internet Explorer. Through the IE toolbar and the context menu items a large number of analysis functions is available to look behind the technology and structure of a web page and to get extensive background information about the current website.
There are analysis features for all aspects of a website. Site Inspector lets you view source code, images, forms, JacaScript source, other scripts and more. Also, functions to check the links and HTML validity of a page as well as performance checks are included. Even the owner of a domain or the website's current global traffic ranking can be accessed. - And all this from inside the one application that you use all the time anyway: Your Internet Explorer!
Paessler Site Inspector]]>originally published at Windows ITPro Meg Instant Doc ID 38924
10. Display the Administrator Logon dialog box - to display a Windows 2000-style logon screen, press Ctrl+Alt+Del twice. However, the administrator logon dialog box will be shown by default if the XP machine is joined into the domain.
9. Use the Windows Classic Start menu and desktop - to give users the familiar Win2K-style Start menu, right-click Start, select Properties from the pop-up menu, then click the Classic Start menu option.
8. Create an MS-Dos boot disk - Insert a 3.5” disk in the disk drive, open My Computer, and right-click the floppy-disk icon. Select Format from the pop-up menu, then select Create an MS-Dos startup disk.
7. Bypass activation on reinstallation - after the initial activation, simply copy the wpa.dbl file in the system32 directory, then restore the file after you reinstall XP. However, it might not work if you changed the network adapter.
6. Enable ClearType - right-click the desktop, choose Properties, then click the Appearance tab. Click Effects, select Use the following method to smooth edges of screen fonts, then select the ClearType option from the drop-down list.
5. Identify startup option with MSConfig.
4. Uninstall Windows Messenger - open the sysoc.inf file in the \windows\inf folder and finding the line
msmsgs=msgrocm.dll, 0cEntry, msmsgs.inf, hide, 7
delete the word hide from the line, then save the file. An option to remove Windows Messenger will then be available in the Control Panel Add/Remove Windows Components applet.
3. Configure alternative IP address support - good for the person who regularly move their laptop between a network that requires a fixed IP address and one that uses DHCP.
2. Backup to a CD-ROM - to work around, open NTBackup, select the files to back up, then select c:\documents and settings\username\local settings\application data\microsoft\cd burning\backup.bkf as the backup destination. When the backup finishes, XP will prompt you to write the files to the CD-ROM.
1. Use Remote Assistance over Network Address Translation (NAT) - my experience, not much useful.
]]>Eevn though this Malware remove tool along with their beta Anti-Spyware software more like target on the cosumers not enterpise level, this is the neccessary and important step that would lead them to the next level of the security solution on the enterprise level. Good job...and keep going.
]]>Thanks Christian Nordbakk's HabaHaba 0.95 and Ryan Farley's wonderful icons.
]]>Google also suggested that the web software community should quickly adopte this attribute. I know some versions of .Text has been improved by adding moderation feature or picture identify technology to prevent the blog spam coming. Top of that, this new feature from search engine giant would make these spams less than useless to the reader as they will not be indexed on the search engine database. I wish if some .Text fan would do anything on it.
]]>http://www.shebeen.com/win32-forensics/index.html
]]>http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dnsql2k/html/sqlxml_optimperformance.asp.
The white paper includes lots of nifty tips and tricks for developers to improve the performance of SQLXML. In addition, the white paper also includes a sample application that illustrates and models lots of best practices for coding and design.
]]>C:\>ping 131.94.57.182
Pinging ? with 32 bytes of data:
Reply from 131.94.57.182: bytes=32 time=73ms TTL=236
Reply from 131.94.57.182: bytes=32 time=74ms TTL=236
Reply from 131.94.57.182: bytes=32 time=73ms TTL=236
Reply from 131.94.57.182: bytes=32 time=73ms TTL=236
Ping statistics for Où?:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds: Minimum = 73ms, Maximum = 74ms, Average = 73ms
I am pretty sure that the full spyware scan caused this problem. Don't know what exactly happened inside but it did corrupt all TCP/IP or WinSock component, which stops all network related services like “Net Logon”, “Personal Firewall”, etc. Then, I looked up the Microsoft knowledge base to see if there is a way to uninstall and reinstall the TCP/IP component as Windows XP does not allow it by default. Microsoft knowledge base #325356 describes how to do it in Windows 2003 server, however, it works on Windows XP as well. Here are the steps:
| 1. | Restart the domain controller. |
| 2. | When the BIOS information appears, press F8. |
| 3. | Select Directory Services Restore Mode, and then press ENTER. |
| 4. | Use the Directory Services Restore Mode password to log on. |
| 5. | Click Start, and then click Run. |
| 6. | In the Open box, type regedit, and then click OK. |
| 7. | Locate the following registry subkeys:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Winsock
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Winsock2 |
| 8. | Right-click each key, and then click Delete. |
| 9. | Click Yes to confirm the deletion of each key. |
| 10. | Close Regedit. |
| 11. | Locate the Nettcpip.inf file in %winroot%\inf, and then open the file in Notepad. |
| 12. | Locate the [MS-TCPIP.PrimaryInstall] section. |
| 13. | Edit the Characteristics = 0xa0 entry and replace 0xa0 with 0x80. |
| 14. | Save the file, and then exit Notepad. |
| 15. | In Control Panel, double-click Network Connections, right-click Local Area Connection, and then select Properties. |
| 16. | On the General tab, click Install, select Protocol, and then click Add. |
| 17. | In the Select Network Protocols window, click Have Disk. |
| 18. | In the Copy manufacturer's files from: text box, type c:\windows\inf, and then click OK. |
| 19. | Select Internet Protocol (TCP/IP), and then click OK. Note This step will return you to the Local Area Connection Properties screen, but now the Uninstall button is available. |
| 20. | Select Internet Protocol (TCP/IP), click Uninstall, and then click Yes. |
| 21. | Restart your computer, and then select Directory Services Restore Mode as mentioned in steps 2 - 4. |
| 22. | In Control Panel, double-click Network Connections, right-click Local Area Connection, and then select Properties. |
| 23. | On the General tab, click Install, select Protocol, and then click Add. |
| 24. | In the Select Network Protocols window, click Have Disk. |
| 25. | In the Copy Manufacturer's files from text box, type c:\windows\inf, and then click OK. |
| 26. | Select Internet Protocol (TCP/IP), and then click OK. |
| 27. | Restart your computer. |
Yeah...after I followed all these steps, my computer finally got back to work.
I am not blaming on this software here as I have seen this before on other anti-spyware as well. I am still having it running on my computer to prevent the spyware but will be careful to do the full scan and any operations afterwards. If the same thing happened on your computer, do the fix above would fix your problem.
]]>Microsoft AntiSpyware Preview
http://www.winsupersite.com/reviews/ms_antispyware_preview.asp
Download Microsoft Windows AntiSpyware Beta 1
http://www.microsoft.com//spyware/
Also, Jonathan Hardwick posted some more info on his blog
http://blogs.msdn.com/jonathanh/archive/2005/01/06/348224.aspx
| To use Google's built-in calculator function, simply enter the calculation you'd like done into the search box and hit the Enter key or click on the Google Search button. The calculator can solve math problems involving basic arithmetic, more complicated math, units of measure and conversions, and physical constants. Try one of the sample expressions below, or refer to our complete instructions for help in building your own. |
These sample queries demonstrate the utility and power of this new feature:
Click here to see what else feautres you can find from Google.
]]>Why? see here for the reason.
How? see the tips for registering your blogsite
Where? see the best blog directory and RSS submission sites
and the white paper here for corporate blogging.
]]> Looking for a way to contain your WiFi signals and block unwanted outside signals? Paint might be your answer. Force Field Wireless has a product line, DefendAir Radio Shield, that might help.
Looking for a way to contain your WiFi signals and block unwanted outside signals? Paint might be your answer. Force Field Wireless has a product line, DefendAir Radio Shield, that might help.
Haha...looks interesting.
]]>This white paper talks about why we should use account lockouts.
A full tools package from Microsoft can be downloaded here.
However, someone points out that there is one potential thread that people can us this lockout feature as a DoS attack. Well, there is no perfect solution at all in this world on anything even though someone is always looking for it. It is just like another "You can't have fish and bear palm at one time" (chinese slang).
Everything you need to balance. For most of cases, password lock out is still working to those organizations that don't have that much chance to get this DoS attack, but for others, not using it may be better. If that does happen the only way to still make sure you are secure seems to be giving more complex password or pass phrase.
By the way, pass phrase is really a good idea to enhance the power of password. However, you need to balance it as well. Not everyone can type such long characters into the password fields.
The Great Debates: Pass Phrases vs. Passwords. Part 1 of 3
]]>- In Dos-prompt window, type telnet domain-name.com 25 to open a SMTP session.
- helo
250 Hello domain-name.com - mail from: kent@kjctech.net
250 OK - rcpt to: chen@kjctech.net
250 OK - rcpt to: gates@microsoft.com
550 Relaying Prohibited.
A 550 response code stats that relaying is prohibited, you are safe. If it doesn't, your server is an open relay, close it right away.
To test an authenticated relay, after you get 550 response code, type auth login to provide the username and password, and after you successfully authenticate, type the command listed on step 5 again.? This time, you should see a 250 response stating that relaying with authentication is permitted.? Please notice that on some Active Directory based windows environment, type domain\username as the username.
As you develop your testing scenarios to guard against SMTP relays, make sure you document them, then intergrate them as a standard operating procedure to be performed periodically. In most environments, multiple people can make changes, which increases the risk that the system could be mis-configured. Test often to ensure that the system's relay security hasn't been compromised.
]]>- Domains and Trusts
- IP Security (IPSec)
- Networking
- SQL Server service
- Web service
- Exchange Server
- NetMeeting
- miscellaneous
Like Portqry, Portqryui can be configured to run against the local box (IP address 127.0.0.1, the standard loopback address) or a remote IP address or Fully Qualified Domain Name (FQDN). When you view the output of the Portqryui tool, you'll see the actual commands that portqryui.exe passes to portqry.exe, which shows below. You could write a script that lets you automate these commands.
 ]]>
]]>Quote from http://builder.com.com/5100-6375_14-5136758.html?tag=nl.e601

Read more about the winners of the 2004 Open Source Awards:
- Open Source Awards 2004: Julian Seward for Valgrind
- Open Source Awards 2004: VideoLAN
- Open Source Awards 2004: Paul Davis for JACK
- Open Source Awards 2004: Pango
Julian Seward for Valgrind
Sooner or later, in the life of every developer, you'll have to turn to a debugger. There's only so much you can do with embedded println statements. For the Linux-on-Intel-x86 crowd, one of the most popular options available is Julian Seward's valgrind. It works by emulating the Intel CPU so that it can see exactly what your program is doing, and it is a fair match for commercially available Linux debuggers such as Purify, at a fraction of the price—free. Read more about Mr. Seward and his remarkable debugger.
VideoLAN
Can a university in Paris, France challenge the might of Seattle's Microsoft and Real Networks in the streaming multimedia game? Absolutely—VideoLAN started as a school project, but it has blossomed into a full-featured solution for streaming media on the Web. It handles multimedia streaming of MPEG-1, MPEG-2, MPEG-4, and DivX files, DVDs, digital satellite channels, digital terrestial television channels, and live video. Plus, it's truly cross-platform, running on various Linux flavors as well as on Mac OS X and Windows. Read more about VideoLAN and the team that helped create it.
Paul Davis for Jack
What would you do if you found that the only way to get audio from one application into another was by running a cable from your sound card's speaker jack into the microphone jack? If you're Paul Davis, you start an open source community project. Two years ago, Mr. Davis realized that one of the critical issues in multimedia being truly useful on Linux was the question of how to get different audio applications to talk to each other. This is exactly what the Jack Audio Connection Kit (JACK) does. Read more about Paul Davis and the audio API he helped create.
Pango
Those of us based in the United States tend to forget this fact, but not everyone on the World Wide Web uses English as their primary language. This is where Pango comes in—to provide a framework for the layout and rendering of internationalized text. Using Unicode for all of its encoding, Pango can potentially render any language. It just requires someone in the open source community to create the language-specific pieces that Pango needs to make that rendering possible. Read more about how Pango is trying to bring order to this Tower of Babel.
And more to come…
There will be additional bronze awards granted throughout the year, and this summer the OSI committee will announce the Grand Master and Special awards during the O'Reilly Open Source Convention.
It appears that the overall quality of code, and more importantly, the amount of QA, on various browsers touted as "secure", is not up to par? with MSIE; the type of a test I performed requires no human interaction and involves nearly no effort. Only MSIE appears to be able to consistently handle [*] malformed input well, suggesting this is the only program that underwent rudimentary security QA testing with a similar fuzz utility.
This is of course not to say MSIE is more secure; it does have a number of problems, mostly related to its security architecture and various features absent in other browsers. But the quality of core code appears to be far better than of its "secure" competitors.
See the full article here: http://blogs.crsw.com/mark/articles/652.aspx. And the sample starts below:
WindowsITPro InstantDoc #44862
' John Savill
' This is based on Richard Mueller's script on Interger8Date
' conversion, which is copyrighted as below.
' Copyright (c) 2003 Richard L. Mueller
' Hilltop Lab Web site - http://www.rlmueller.net
'
' I simply changed it to output all objects in a passed DN.
Option Explicit
Dim strLdapPath, objConnection, objChild
Dim lngTZBias, objUser, objPwdLastSet
Dim objShell, lngBiasKey, k
' Check that all required arguments have been passed
If Wscript.Arguments.Count < 1 Then
Wscript.Echo "Arguments required. For example:" & vbCrLf _
& "cscript listuserpasslastchange.vbs ou=test,dc=demo,dc=test"
Wscript.Quit(0)
End If
strLdapPath = Wscript.Arguments(0)
' Obtain local Time Zone bias from machine registry.
Set objShell = CreateObject("Wscript.Shell")
lngBiasKey = objShell.RegRead("HKLM\System\CurrentControlSet\Control\"_
& "TimeZoneInformation\ActiveTimeBias")
If UCase(TypeName(lngBiasKey)) = "LONG" Then
lngTZBias = lngBiasKey
ElseIf UCase(TypeName(lngBiasKey)) = "VARIANT()" Then
lngTZBias = 0
For k = 0 To UBound(lngBiasKey)
lngTZBias = lngTZBias + (lngBiasKey(k) * 256^k)
Next
End If
Set objConnection = GetObject("LDAP://" & strLdapPath)
objConnection.Filter = Array("user")
For Each objChild In objConnection
Set objPwdLastSet = objChild.pwdLastSet
WScript.Echo objChild.Name & vbTab & _
Integer8Date(objPwdLastSet, lngTZBias)
Next
Wscript.Echo "Operation Completed"
Function Integer8Date(objDate, lngBias)
' Function to convert Integer8 (64-bit) value to a date, adjusted for
' local time zone bias.
Dim lngAdjust, lngDate, lngHigh, lngLow
lngAdjust = lngBias
lngHigh = objDate.HighPart
lngLow = objdate.LowPart
' Account for error in IADslargeInteger property methods.
If lngLow < 0 Then
lngHigh = lngHigh + 1
End If
If (lngHigh = 0) And (lngLow = 0) Then
lngAdjust = 0
End If
lngDate = #1/1/1601# + (((lngHigh * (2 ^ 32)) _
+ lngLow) / 600000000 - lngAdjust) / 1440
' Trap error if lngDate is ridiculously huge.
On Error Resume Next
Integer8Date = CDate(lngDate)
If Err.Number <> 0 Then
On Error GoTo 0
Integer8Date = #1/1/1601#
End If
On Error GoTo 0
End Function
To run the script, use the syntax
cscript listuserpasslastchange.vbs ou=test,dc=demo,dc=test
You'll see output that's similar to this:
CN=Bruce Wayne 11/17/2003 1:30:14 PM CN=Clark Kent 11/17/2003 1:31:30 PM CN=Hal Jordan 12/6/2004 2:52:56 PM CN=Wally West 3/17/2003 9:04:45 AM
1. Create a xml map file which acutally is a simply xml file containing at least 2 sets of the data. See the example below:
<?xml version="1.0" encoding="ISO-8859-1" ?>
<data>
<users>
<id>id</id>
<fullname>full name</fullname>
</users>
<users>
<id>id</id>
<fullname>full name</fullname>
</users>
</data>
2. From Excel, click Data->XML->XML Source... to open the XML Source window on the right side of work sheet.
3. Click XML Maps button and Add button to add the XML map file.
4. Pick up the column and double-click the proper XML filed name to link each other.
5. Repeat step 4 to link all the columns you want to export.
6. Once it's done, click Data-XML->Export... to export the data into XML format file.
]]>Haven't fully tested yet so don't have much to comment but thought it is something good to know.
]]>Quote from http://hublog.hubmed.org/archives/000942.html
- Everything you search for using Google
- Every web page you visit that has Google Adsense ads on it
- Which country you're in
- Every Blogger page you visit, and the referring page
- If you have an Adsense account
- Your full name, address and bank account details
- The IP address of everyone who visits your pages with Adsense ads on them
- The number of visitors to each of your pages with Adsense ads on them
- If you use a GMail account
- Who you send emails to
- Who sends emails to you
- The contents of those emails
- The contents of all emails received from any mailing lists of which you are a member, even if they are private mailing lists.
- Even if you don't use a GMail account
- The contents of any emails you send to anyone who does use a GMail account
- The contents of any emails you send to any mailing lists of which any one member uses a GMail account
- If you're a member of Orkut
- Your online social network, interests and groups
Google knows a lot about you. They do everything they can to try to track your activities online, and even put a cookie on your PC. If you ARE worried: this page tells you how to anonymize the Google cookie and more in the following:
- disable cookies in your browser
- don't use the Google Toolbar or turn off the features that "phone home": it's easily done
- don't use other Google services that index your hard drive or track your surfing
- use a different blog service
- use a different affiliate, if you think that will mean they are not tracking you
 Microsoft this week dropped McAfee virus protection technologies from its Hotmail Web-based email service and replaced it with a solution from McAfee competitor Trend Micro. With 187 million active users, Hotmail is a huge coup for Trend Micro, which is already touting the deal in online and periodical-based advertisements. Neither Microsoft nor McAfee has issued an explanation for the change.
Microsoft this week dropped McAfee virus protection technologies from its Hotmail Web-based email service and replaced it with a solution from McAfee competitor Trend Micro. With 187 million active users, Hotmail is a huge coup for Trend Micro, which is already touting the deal in online and periodical-based advertisements. Neither Microsoft nor McAfee has issued an explanation for the change.
See the whole story here: http://www.trendmicro.com/en/about/news/pr/archive/2004/pr122004.htm</P
]]>
More details: http://www.symantec.com/veritas/
 ]]>
]]>Here is the full article:
Companies often use a .local or .pvt TLD to name an AD tree. However, as I explain shortly, it's better to use a standard naming method--for example, create a name by using a subdomain of your company's DNS address space (e.g., if your company's DNS domain is ntfaq.com, you could name your AD tree ads.ntfaq.com). When you use this method, though, you must remember that the DNS information for the AD tree is hosted on internal DNS servers, not on your external DNS servers. This means that external users can't see information about your internal infrastructure because external users can access only the external DNS server, which has no information about your internal infrastructure. Alternatively, if you want to create a second-level name for your AD domain, reserve another name--for example, ntfaq.net--but don't set your AD domain to the same name as your external name, to avoid causing confusion in name resolution.If you're determined to use a nonstandard TLD in your domain name, avoid the use of .local or .pvt because they aren't reserved. Instead, use one of these reserved top-level domains:
- .test
- .example
- .invalid
- .kentjchen.webhost4lifemysql.com
You can find more information about these names in Internet Engineering Task Force (IETF) Request for Comments (RFC) 2606. Remember, if you use these nonstandard DNS names, you can't obtain certificates from a third-party Certificate Authority (CA), which might cause problems for your organization.
]]>(Microsoft Press, 2004), tackles modern-day code construction problems and provides all-new code examples written in C++, Visual Basic (VB), and Java. This book should be on every programmer's desk—read it and you'll write better code. Here are five code-writing concepts:
Class Creation
Building classes is a common programming task that programmers frequently perform incorrectly. Classes, collections of methods that share a given responsibility, usually model real-world objects.
Building Routines
Building good code routines that reduce complexity, make programs easier to read, and avoid code repetition.
Naming Conventions
The way you name the objects that your programs use is the single biggest contributing factor to code readability. The book devotes an entire chapter to showing you how to write variable, class, and routine names that are readable, appropriate, and memorable.
Debugging Techniques
Debugging early in the development cycle can help you test code paths and find logic errors in your code. To help make your debugging more efficient, the new edition presents a scientific method for debugging. You'll learn how to form a hypothesis about an error's source, use testing to prove or disprove your hypothesis, then locate and stabilize the error.
Defensive Coding
Programmers often write code that assumes the data it works with is perfect. While the code might function as it's designed to under typical conditions, it can fail miserably when confronted with bad data or other unexpected conditions. Basically, coding defensively means that you design your code to handle incorrect input and to not pass along bad data. Defensive coding takes significantly more time, but a lack of defensive coding causes poor software quality.
Now I am interested in hunting more related information to give me more clear figure.
Read the full article here: http://www.windowsitpro.com/Articles/Print.cfm?ArticleID=44352
]]>According they said, the Gift of Google is appropriate for all ages and connection speeds. Batteries not included.
 ]]>
]]>Article: http://blogs.msdn.com/msnsearch/archive/2004/12/13/282000.aspx
Download: http://beta.toolbar.msn.com/
 ]]>
]]>You can download this tool from http://www.microsoft.com/technet/scriptcenter/default.mspx
and for those of you who don't know what Scriptomatic is, you can read a very funny article here, Scriptomatic Tool (http://www.microsoft.com/technet/scriptcenter/tools/wmimatic.mspx)
And the Scriptomatic Tool version 2.0 is on its way out...
]]>He continued, "And that's the way it is with stress management. If we carry our burdens all the time, sooner or later, as the burden becomes increasingly heavy, we won't be able to carry on." "As with the glass of water, you have to put it down for a while and rest before holding it again. When we're refreshed, we can carry on with the burden." "So, before you return home tonight, put the burden of work down. Don't carry it home. You can pick it up tomorrow. Whatever burdens you're carrying now, let them down for a moment if you can." "Relax; pick them up later after you've rested. Life is short. Enjoy it!"
And then he shared some ways of dealing with the burdens of life:
1. Accept that some days you're the pigeon, and some days you're the statue.
2. Always keep your words soft and sweet, just in case you have to eat them.
3. Always read stuff that will make you look good if you die in the middle of it.
4. Drive carefully. It's not only cars that can be recalled by their maker.
5. Eat a live toad in the morning and nothing worse will happen to you for the rest of the day.
6. If you can't be kind, at least have the decency to be vague.
7. If you lend someone $20 and never see that person again, it was probably worth it.
8. It may be that your sole purpose in life is simply to serve as a warning to others.
9. Never buy a car you can't push.
10. Never put both feet in your mouth at the same time, because then you won't have a leg to stand on.
11. Nobody cares if you can't dance well. Just get up and dance.
12. Since it's the early worm that gets eaten by the bird, sleep late.
13. The second mouse gets the cheese.
14. When everything's coming your way, you're in the wrong lane.
15. Birthdays are good for you. The more you have, the longer you live.
16. You may be only one person in the world, but you may also be the world to one person.
17. Some mistakes are too much fun to only make once.
18. Don't cry because it's over. Smile because it happened.
19. We could learn a lot from crayons. Some are sharp, some are pretty and some are dull. Some have weird names, and all are different colors but they all have to live in the same box.
20. A truly happy person is one who can enjoy the scenery on a detour.
21. Happiness comes through doors you didn't even know you left open.
Have an awesome day and know that someone has thought about you today...............I did.
]]>Attracting qualified Internet traffic to a website (i.e. customers that are interested in the products or services being offered) ought to be the ultimate goal of any online marketing strategy. This effort cannot be simply limited to the selection of a series of search keywords and engines, all chosen beforehand. Instead, a more global approach must be adopted that encompasses web optimization, search engine submissions, inclusion of references in external areas such as forums, user groups or value-added portals, the publication of articles, and the contribution of content to other websites. This expanded strategy will enhance our overall Internet presence and will enable the most popular search engines to locate a website applying a greater variety of search concepts. Lastly, by applying the feedback obtained from the web traffic reports, the global Internet presence can be continually improved and sustained to ensure consistent and effective results.
Click here to see the full article.
]]> ]]>
]]><script language="javascript">
function redirect()
{
window.location = "http://www.kjctech.net/blog/"
}
setTimeout("redirect();", 0)
</script>
 ]]>
]]>Wiki is a term derived from the Hawaiian word for "quick" and describes websites that can be accessed and changed using a simple browser-based user interface.
JotSpot is still taking applications for its beta at http://www.jot.com/request_beta/index.php.
 ]]>
]]>1. Analytical or systems thinking - being able to see how things work together.
2. Client relationship management
3. Coaching and mentoring - driving out shared skills and learning from peers
4. Consensus and agreement building
5. Change leadership
6. Modeling - including data and process modeling and functional design
7. Facilitation or requirements solicitation - the ability to pull together experts to get the right information from them.
8. Professional knowledge - an understanding of the business
9. Requirements planning and management
10. Verbal and written communications
If you want to be a business analyst, take a look at yourself and where you stand on these things and address any gaps and figure out what you have to do to fill in your experience.
]]>Cisco Systems Inc. and Microsoft Corp. have gotten the word: IT managers are tired of constantly plugging security holes in their networks. As a result, the two technology giants have hatched an agreement to develop and promote interoperability between their network access technologies. The two companies will collaborate by sharing technical information on Cisco's Network Admission Control and Microsoft's Network Access Protection to ensure interoperability.
The end result is that, by 2007, when Microsoft releases its latest version of Windows server software, the two security technologies should be compatible, allowing companies to examine Windows software and Cisco network infrastructure simultaneously.
]]>SQL injection is a strategy for attacking databases. The attacker "injects" a SQL statement into another statement--often to inflict damage upon your database. Web sites that interface with databases are particularly vulnerable to SQL injection because they often rely on dynamic SQL. Here's a simple example.
An ASP page asks the user for a name and a password, and then sends the following string to the database:
SELECT FROM users WHERE username = 'whatever' AND password = 'mypassword'
It seems safe, but it isn't. A user might enter something like this as her user name:
' OR 1>0 --
When this is plugged into the SQL statement, the result looks like this:
SELECT FROM users WHERE username = '' OR 1>0 -- AND password = ''
This injection comments out the password portion of the statement. It results in a list of all the names in the users table, so any user could get into your system.
The easiest way to prevent this sort of injection is to parse the SQL string and remove any occurrences of "--" before passing the statement.
You also have to beware of injections that contain semicolons because semicolons delimit SQL statements. Think about the implications of a user name like this:
' OR 1>0 ; DELETE Customers ; --
There are numerous ways a malicious user might penetrate your system using SQL injection and various defenses, but the simplest approach is to avoid dynamic SQL. Instead, use stored procedures everywhere. Thanks to the way SQL passes parameters, injections such as those above will produce errors, and the stored procedure will not execute.
]]>RMS helps businesses keep their most sensitive information within the organization and lets content owners control how their content is used - who can open and modify a certin document, how long users can access it, and so on. RMS lets you prevent accidental distribution and control what people can do with the information. Further, that protection remains with the file wherever it goes - if someone gains access to a diskette that contains RMS-protected information, that person must have a valid use license against that file in order to read it.
Requirements
RMS requires Windows Server 2003, a database such as Microsoft SQL Server, Windows Server Active Directory, and an RMS-enabled application or browser.
Implementation and Use
One of the goals of RMS is that it's easy to deploy. RMS is an Active Directory - intergrated technology, so it can be rolled out by GPO to get the client bits out.
Components
Server Software: download
Client Software: download
RMS-enabled Applications
Licensing
To use RMS, organizations need the following licenses:
• Windows Server 2003 Server License
• Windows Server 2003 Client Access Licenses (Windows Server CALs)
• Windows Rights Management Services Client Access Licenses (RMS CALs)
For more detail information about Microsoft Rights Management Services, click here]]>
Restricting user access
The new Windows 2003 has a new built-in local security group called Remote Desktop Users. We can use this group to manage access to the computer when it's configured as a TS machine. Only members of this group and the local Administrators group have permission to log on remotely to the TS system. In addition to that, we can further manage basic user permissions and privileges by assigning users to the local computer's various security groups.
Restricting data access
To restrict access to particular application, you can apply a Software Restriction Policy GPO or set NTFS ACLs on the directories of the applications that you want to restrict. The GPO route is advantageous because you can link the GPO to a Domain, Site, or OU AD object, and that GPO will be enforced for any objects within that container. For example, if you need to add a server, you can configure it an move it to the GPO-enabled OU. After you restart the computer or run the command gpupdate.exe to update the GPO for its new OU, it will be locked down like the others in that OU. Generally, NTFS ACLs don't scale as well as GPOs, which you can manage centrally; however it lets you discretely restrict access on a per-file or per-folder basis.
Fine-tuning security configuration through a GPO
You might prefer that the user have greater access at his or her workstation that at the TS system. Unfortunately, because the user configuration is associated with the user object, the same user-configuration GPO will be applied regardless of which computer the user logs on to. However, you can solve this problem by using a GPO setting called loopback processing.
With loopback processing, you can apply a GPO on an OU containing the TS computer object that also applies to users contained elswhere. Any user who logs onto the TS server will be governed by that system's user-configuration GPO instead of any other GPO that might be applied to the user. In the GPO editor, navigate to Computer Settings, Administrative Templates, System, Group Policy and enable the GPO policy called User Group Policy loopback processing mode. When you enable this policy, you must select whether to replace or merge the user-configuration settings between the Terminal Server computer GPO and the user's native GPO.
Fine-tuning security configuration through TSCC
You can also configure most Terminal Server security settings directly on a Terminal Server computer by using the TSCC tool. However, if you have set a GPO, the GPO will have priority and the equivalent setting in TSCC will be unavailable.]]>
To get visitors to come to your site via search engine results (SERPs), you need to rank in the top 20 - if not the top 10 - for searches on spcific keywords/phrases that your firm is targeting. While writing search engine-friendly content is out of the control of the Web development team, there is a lot you can do to optimize your site markup for search engines. Here are 10 tips to help you mark-up your code properly.
Tip 1. The first rule of SEO is not to design your site in such a way that the code itself prevents a search engine bots/spiders from being able to index the site. The bottom line: don't build a web site entirely in Flash if you want any traffic from search engines.
Tip 2. To find out what a spider sees on your site, run a spider simulator on a given page. The simulator will show you what text the spider sees and what links it finds. Here is the one.
Tip 3. Each website should have a file called robots.txt, which tells the spiders what directories they should not spider.
Tip 4. Determine the main topic of the page and use it as the page title.
Tip 5. Write a unique description meta tag for each page - something you should ask the content provider to give you.
Tip 6. Put all your JavaScripts in external files and link to them. You will be increasing the ratio of content to code on your page, which helps make your message clearer to search engines and you will be making your markup cleaner and website management easier.
Tip 7. Search engines love content that appears in header tags (h1, h2, etc.) yet very few website actually use them.
Tip 8. Don't spend time creating JavaScript mouseovers, trying using the hover feature of CSS instead. If, for specific reasons, you can't use CSS, then repeat the menu options at the bottom of the page with plain text.
Tip 9. Avoid unnecessary tables where possible. Limit your table embedding to a depth of three. Where possible avoid the whole table thing and start using XHTML with div tags and CSS to define position.
Tip 10. Use either or to mark up important words on your page.
By following this basic outline, you'll be creating search engine-friendly pages. The search engine bots will easily index your pages, and with important words and phrases appropriately tagged; those words will receive proper valuation by the search engines.]]>
10. Security hotfixes rollup
9. Security Center
8. Internet Explorer (IE) Add-on Manager
7. Outlook Express image blocking
6. Popup blocking for IE
5. Data execution prevention (DEP)
4. Integrated Bluetooth support
3. Improved wireless support
2. Secure wireless configuration
1. Windows Firewall
Click here to see the full version of the article.]]>
Components
1. A computer running Windows 2000 or 2003 running SUS.
2. An update to the automatic updating technology in Windows 2000, XP, and 2003.
Installation and Configuration
1. Enable IIS on the server, and make sure the anonymous is enabled on the root site.
2. Download SUS from Microsoft, and install it on the same server.
3. From any computer, access http://servername/susadmin from IE to start configuring SUS.
4. Configure the Group Policy to force the workstation to get updates and patches from SUS server rather than Microsoft Update site.
Resources
Microsoft Site: Software Update Services
Microsoft Software Update Services Newsgroup
SUSServer.com
FAQShop.com]]>
Well, here is one that provides this function. The program called rdesktop from the open source rdesktop.org. Rdesktop is a Linux_based program that allows Linux users to connect to Windows-based machines running Terminal Services or Remote desktop.]]>
 .Text was dead long time ago but since there is no other good alternatives that would migrate my current posts over I was stuck and painfully kept using the built-in online admin tool to do the posting, which was one of the reasons that I didn't do a lot of posts for quite a while. .Text just doesn't work with Live Writer at all.
.Text was dead long time ago but since there is no other good alternatives that would migrate my current posts over I was stuck and painfully kept using the built-in online admin tool to do the posting, which was one of the reasons that I didn't do a lot of posts for quite a while. .Text just doesn't work with Live Writer at all.
Just about a few days ago, Ken Hales who uses my own customized skin on .Text emailed me and asked if I am able to upgrade my KJC skin for Subtext, a fork of .Text. Of course, this is exactly what I have been waiting for. After just a few Google check, I started upgrading my .Text blog engine without any hesitation. I had a little bit problem when testing on my own computer because of my new Vista built-in IIS 7 but was working great after I figured that I had to switch the Application pool mode to classic. And then with Ken's help, I successfully imported my old posts over. There is a little issue that the post categories doesn't work properly but I don't really bother.
Updating my skin is also extremely easy. I updated it within an hour and everything is all ready. I will be sharing my skin with Subtext soon after I clean it up a little bit more to make it more standard.
The first thing I did after I put my new Subtext version of blog online was to test if it works with Live Writer...and bingo. The Live Writer connected my Blog without any problem. Everything now works just like a charm.
Now I am back right on track!!
]]> 1) Protects silver from tarnishing.
1) Protects silver from tarnishing.
2) Removes road tar and grime from cars.
3) Cleans and lubricates guitar strings.
4) Gives floors that 'just-waxed' sheen without making it slippery.
5) Keeps flies off cows.
6) Restores and cleans chalkboards.
7) Removes lipstick stains.
8) Loosens stubborn zippers.
9) Untangles jewelers chains.
10) Removes stains from stainless steel sinks.
11) Removes dirt and grime from the barbecue grill.
12) Keeps ceramic/terra cotta garden pots from oxidizing.
13) Removes tomato stains from clothing.
14) Keeps glass shower doors free of water spots.
15) Camouflages scratches in ceramic and marble floors.
16) Keeps scissors working smoothly.
17) Lubricates noisy door hinges on vehicles and doors in homes
18) It removes black scuff marks from the kitchen floor! Use WD-40 for those nasty tar and scuff marks on flooring. It doesn't seem to harm the finish and you won't have to scrub nearly as hard to get them off. Just remember to open some windows if you have a lot of marks.
19) Bug guts will eat away the finish on your car if not removed quickly! Use WD -40!
20) Gives a children's play gym slide a shine for a super fast slide.
21) Lubricates gear shift and mower deck lever for ease of handling on riding mowers.
22) Rids kids rocking chairs and swings of squeaky noises.
23) Lubricates tracks in sticking home windows and makes them easier to open.
24) Spraying an umbrella stem makes it easier to open and close.
25) Restores and cleans padded leather dashboards in vehicles, as well as vinyl bumpers.
26) Restores and cleans roof racks on vehicles.
27) Lubricates and stops squeaks in electric fans.
28) Lubricates wheel sprockets on tricycles, wagons, and bicycles for easy handling.
29) Lubricates fan belts on washers and dryers and keeps them running smoothly.
30) Keeps rust from forming on saws and saw blades, and other tools.
31) Removes splattered grease on stove.
32) Keeps bathroom mirror from fogging.
33) Lubricates prosthetic limbs.
34) Keeps pigeons off the balcony (they hate the smell).
35) Removes all traces of duct tape.
36) Folks even spray it on their arms, hands, and knees to relieve arthritis pain.
37) Florida's favourite use is: "cleans and removes love bugs from grills and bumpers."
38) The favourite use in the state of New York WD-40 protects the Statue of Liberty from the elements.
39) WD-40 attracts fish. Spray a LITTLE on live bait or lures and you will be catching the big one in no time. Also, it's a lot cheaper than the chemical attractants that are made for just that purpose . Keep in mind though, using some chemical laced baits or lures for fishing are not allowed in some states.
40) Use it for fire ant bites. It takes the sting away immediately and stops the itch.
41) WD-40 is great for removing crayon from walls. Spray on the mark and wipe with a clean rag.
42) Also, if you've discovered that your teenage daughter has washed and dried a tube of lipstick with a load of laundry, saturate the lipstick spots with WD- 40 and re-wash. Presto! Lipstick is gone!
43) If you sprayed WD-40 on the distributor cap, it would displace the moisture and allow the car to start.
]]>You've run Windows Vista, you've played around with the Aero interface, and maybe you've even mucked around a little bit in Vista's innards to see what makes it tick.
Now what?
Now is when the fun begins. There are plenty of ways you can tweak Windows Vista, make it jump through hoops, bend it to your will and generally make it behave the way you want it to behave, not the way Microsoft does.
Where to begin? I've put together 10 of my favorite tweaks for Windows Vista. They'll let you do everything from speed up Windows Aero to unlock a supersecret administrator's account and juice up the right-click context menu -- and yes, even adapt the dreaded User Account Control. So if you want to take control of Windows Vista, read on.
With Windows Vista finally behind us, it's time to turn our attention to the next Windows client release, which is currently codenamed Windows "7", though Microsoft has used other code-names, like "Vienna" and "Windows Seven" in the past. Despite an almost complete lack of verifiable information about this next major Windows release, there are at least two excellent reasons to begin discussing this project now:
1. This Web site, the SuperSite for Windows, is dedicated to discussing upcoming Microsoft products, so it's only natural that I'd post a FAQ like this as soon as possible.
2. Microsoft isn't particularly interested in discussing Vienna yet. "The launch of Windows Vista was an incredibly exciting moment for our customers and partners around the world, and the company is focused on the value Windows Vista will bring to people today," Kevin Kutz, a Director in the Windows Client group at Microsoft said on February 13, 2007. "We are not giving official guidance to the public yet about the next version of Windows, other than that we're working on it. When we are ready, we will provide updates." This quote was provided after I wrote a WinInfo article denouncing recent news reports about Vienna, all of which provided absolutely no new information at all.
Clearly, what's needed is a central location for accurate information about Vienna. This is it.
check out Internet Archive right here
[information improvisation] Many internet marketers are constantly updating their website but it is now possible to look back through internet archive. Latest search engine optimization has provided marketers a platform that they should update their websites for better ranking. Another phenomenon is link exchange programs to increase your search ranking. The pay per click advertising is leading towards more optimized websites. Besides all techniques seo advertising is very common.
]]>The problem is due to the change that disables the ActiveX DHTML Editor in IE 7, which requires a hotfix to be applied on Exchange server in order to get the problem completely fixed. Be noticed that you will have to have Exchange Service Pack 2 installed prior to install this hotfix. You don't need to restart your server after the hotfix is installed but the Exchange Information Store service has to be restarted. I did both on our office's Exchange server and OWA is running way better now. The Red X is now long gone.
]]>I am not going to bother to spend that much money for such a file like this but it does remind me to review what Google suggested. It's been a few years since last time I checked their recommendations.
Referring to what Google says, Sitemap helps speed up the discovery of your pages and is particularly helpful if the site has dynamic content, pages that aren't easily discovered by following links. However, it also states that sitemaps do not replace Google's normal methods of crawling the web. It's important but there are many other factors that influences the process.
Google also has provided an easy way to help you to submit the sitemap file so it may be the time for you to think about re-submitting your site with your new created/updated sitemap. It's much easier than before.
]]> One friend of mine recently forwarded me a web design proposal in which a content management named ExpressionEngine will be used as web publishing backbone system. The name sounds familiar but didn't know in detail. So I went in its website, poked around a bit and am pretty surprised what actually this system can do.
One friend of mine recently forwarded me a web design proposal in which a content management named ExpressionEngine will be used as web publishing backbone system. The name sounds familiar but didn't know in detail. So I went in its website, poked around a bit and am pretty surprised what actually this system can do. The system, a PHP-based with MySQL used as back-end database, offers a feature rich web content management system which would dramatically benefit to both developers and end-users. It is modular by design, enabling you to easily add new features and capability with add-on modules, plugins, and extensions. The support seems to be good, the user base is pretty big, and the features are good enough for most of the web applications, even though I haven't seen how it works with the e-Commerce website. And the best of all, it's inexpensive and even offers a free core that you can start with.
]]>Now, it's also the time to list the tools that I am using now on my Vista and will be updated from time to time when any changes are made.
Security Tools
- AVG Anti-virus Free Edition
- Vista built-in Windows Defender
General Tools that I use on daily basis
- Adobe Reader
- PrimoPDF - the free PDF generator
- NotePad2 - it's much easier to configure Notepad2 in Vista to replace the generic Notepad, just simply rename it to Notepad.exe and replace the original one in Windows\system32 folder and that's it.
- SmartFTP free edition - I had been using CuteFTP on my old XP for years but since I have to pay for the upgrade to get a version that is compatible with Vista I decided that it is the time to switch "Cute" to "Smart"
- BurnOn CD&DVD - for the same reason, I change it this one but I am still looking the good alternatives because this burning tool doesn't recognize APE format.
- Firefox with the following add-on:
- Firebug
- GMail Notifier
- Google Toolbar
- IE Tab
- Web Developer 1.1.4
- IE 7 with IE DevToolbar
- Virtual Daemon - must have virtual CD and DVD Drive Emulation tool that I can't live without.
- WinSnap version 1 - the cool screen capture tool I have to use every day. Hoever, I am only using the version 1 as the new release of version 2 is not free anymore. And fortunately, the version 1 is Vista compatible.
- PureText - another must have little tool that stripes all rich features from the text you copy from either Internet or other documents and paste to your editor in pure plain text.
- WinRAR - why do I still need it? Simply because I still receive the .RAR files that I only can use this to open.
- ColorPix - A free color picker.
Programming Tools
- Visual Studio 2005 with ASP.Net AJAX 1.0
- SQL Server 2005 Express with Management Studio Express
- Gemini - my web-based issue tracking system
- SourceGear Vault - my revision and source code control system
- SQL Prompt version 2 - I am only using version 2 as the new release of version 3 costs $195 and I am glad that I downloaded version 2 before.
- CSS Tab Designer
- XML NotePad
- Fireworks - used as my main graphic editor
Other Tools
- Open Office - use as office tool to replace Microsoft Office. No MS Office on my computer even Outlook.
- Gmail - to manage 2 my personal email account
- Outlook Web Access or Remote Desktop - to access my office email account.
- Windows Live Writer - compose and post my blog
- Server Management Tool - to manage all Windows servers in work
- SyncToy - a tool to synchronize my data to my external USB attached storage
- VMware Player
- Virtual PC 2007
[a reader's toolbox] For protecting from viruses there are many types of computers and software that you can buy for personal use. You can download software freely from internet as many websites are providing free. If you need software for business inventory management software is best and microsoft office software can be used for inventory management. The finance software is especially designed for managing your stock. Using software scripts can help you to customize your software. For virtual businesses crm software is best to provide online customer support.
]]> This is a really good question, at least, I have no idea what had been plugged into my computer. EndPointScan, a free web utility released by GFI a few month back, allows you to check what devices are or have been connected to computers on your network and by whom.
This is a really good question, at least, I have no idea what had been plugged into my computer. EndPointScan, a free web utility released by GFI a few month back, allows you to check what devices are or have been connected to computers on your network and by whom. Using this diagnostic tool, you can identify those areas where the use of portable storage devices could pose a risk to the integrity of the company’s systems.
EndPointScan carries out granular checks across all types of ports – USB, Firewire, Bluetooth, Infrared, PCMIA and Wi-Fi – on all machines. This utility provides complete and thorough information about all portable devices and can scan multiple computers simultaneously.
And as most of other online web services, you will have to install an ActiveX control, which I am assuming it must be run in IE.
Wondering what portable devices has been connected to your computer? Check it now.
]]> What Is The Rejection Hotline?
What Is The Rejection Hotline?
In a nutshell, the Rejection Hotline is a phone number you can give out if you just don't want to give out your real number. Callers hear our humorous Rejection Hotline recording and are not-so-subtly informed of your non-interest. But it's all in good fun and we hope those on the receiving end can look at it like Curt did:
"So I guess I'm one of the 'rejectees' mentioned in the L.A. Times article, because I had a girl give me the Rejection Hotline number at a bar a few weeks ago. But I'm not writing to complain about it at all. Just the opposite, I'm writing to say THANKS! Not only do I think it's hilarious, but I love that I could go on letting my buddies think I had gotten her number that night and none of them were around to give me $h*t when I made the call a few days later and heard the Rejection Hotline message... [and I] realized I've still got a lot to learn when it comes to knowing if a girl's interested or not. Thanks for the laugh and the reality-check!"
-- Curt, Los Angeles
There are numerous numbers in US but not so many in Canada, only one number so far in Vancouver. So be careful to use it now as the article that reveals this line was published on today's Metro newspaper. People in Vancouver will be getting very familiar with this number. You might not save the face but lost the face when giving out this number to the person who knows it.
For more details about the hotline, check out at http://www.rejectionhotline.com
]]>Get a hot fix by going to this link instead of calling Microsoft
]]>Q: I’m interested in evaluating Microsoft virtualization, which should I use, Virtual PC or Virtual Server?
A: The answer to this question really depends on your application and usage. Both Virtual PC and Virtual Server are powerful, easy to use products that offer unique features and functionality. For example:
- Virtual PC offers an intuitive, local UI designed for a single user while Virtual Server offers a Web Administration application allowing multiple users to administer Virtual Servers remotely.
- Virtual Server is designed with extensibility in mind and includes a fully documented COM interface in the Virtual Server Programmer’s Guide. So, if you’re interested in developing your own scripts to configure, create virtual machines, Virtual Server is the way to go.
- Virtual Server is heavily threaded and designed to take advantage and scale on multi-processor computers with large amounts of memory. In fact, Virtual Server can use up to 256 GB of physical memory with the latest version.
And yes, that's exactly the same for VMware Server and VMware Workstation or VMware Player. Virtual Server version is designed to host the servers and PC version is designed for hosting the workstations or servers for testing purposes.
And another yes, the images are compatible in both versions. A guest 2003 server virtual machine can be run on both Virtual PC and Virtual server.
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>- Customer Relationship Management: Highrise
- Customer Relationship Management: FreeCRM.com
- Secure E-Mail: Comodo
- Small Business Accounting: Microsoft Office Accounting Express 2007
- Small Business Accounting: TurboCash
- E-Commerce Web Site Analytics: HitTail Basic
- E-Commerce Shopping Cart: AgoraCart
- Business Plan Workshop: CIT Small Business Lending Corporation
- Business Planning: Planware
- Business Management Courses: SBA Free Online Courses
There are other two lists listed the same on PCWorld, which are also awesome:
15 great free programs you've never heard of
Great Free Files: 20 Fantastic Open Source Downloads Utilities
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>I am curious about how this works. So I downloaded and installed it on my computer. Guess what? It's true. The little tool offers some wonderful wizards from which almost all level of users can easily set up their own home network without any help from computer pros. The network map feature looks cool. It gives you a whole picture of how many computers are on your network. Any intruders can be identified easily from the map.
The software comes with two editions, the free version has the basic features that might not be enough to set up a fully operational home network because the more advanced features like printer sharing, file sharing, and add a device wizard are in the premium version which costs at least $29.99.
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>Greg Chapman, developer, solution provider and system engineer, loves creating solutions that could easy a lot of IT Pro's work from time to time. Many of these very popular utilities are award winning tools that are all free for the downloading.
A nice freeware that tells you where precious space has gone to.

Wondering how long your heavy programmed website takes to load in the user's browser? Give this load time tester a try.
How it works
 The Full Page Test loads a complete HTML page including all objects (images, CSS, JavaScripts, RSS, Flash and frames/iframes). It mimics the way a page is loaded in a web browser.
The Full Page Test loads a complete HTML page including all objects (images, CSS, JavaScripts, RSS, Flash and frames/iframes). It mimics the way a page is loaded in a web browser.
The load time of all objects is shown visually with time bars.
You can view the list of objects either in load order or as a hierarchy. The hierarchy view allows you to see which objects are linked to in for example a CSS file.
Every test also shows general statistics about the loaded page such as the total number of objects, total load time, and size including all objects.
JDoc - a place to search Java API documentation
Needless to say, a wonderful place where you can use as your JavaScript library. It's awesome.

[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>- Make Fewer HTTP Requests
- Use a Content Delivery Network
- Add an Expires Header
- Gzip Components
- Put CSS at the Top
- Move Scripts to the Bottom
- Avoid CSS Expressions
- Make JavaScript and CSS External
- Reduce DNS Lookups
- Minify JavaScript
- Avoid Redirects
- Remove Duplicate Scripts
- Configure ETags
Now, how do we check to make sure the website we are building actually follows these simple rules? No worry, developers from Yahoo know what we want and won't just tell you the principles and leave us no way to prove how bad performance our websites are. They developed YSlow, a Firefox add-on integrated with the popular Firebug web development tool, which analyzes web pages and tells you why they're slow based on the rules for high performance web sites.
Coding Horror's YSlow: Yahoo's Problems Are Not Your Problems also reveals this tool in great detail.
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]> I am not the fun of Blackberry at all and never bothered to try understanding how it works until recently I was asked by one of my colleague who just recently purchased a new Blackberry and wanted to have it properly for both work and personal.
I am not the fun of Blackberry at all and never bothered to try understanding how it works until recently I was asked by one of my colleague who just recently purchased a new Blackberry and wanted to have it properly for both work and personal.
I used to set up a rule in the outlook that automatically forwards all incoming emails to the email address associated with the Blackberry but I realized this was totally WRONG after playing with the set up for a few hous. You should never need the @blackberry.net email address to get all emails transferred between the mail server and the Blackberry handheld because the whole idea works in a pull and push method which means that the service provider pulls the emails from your mailbox and pushes them onto your handheld afterwards for you.
If you want to connect your Blackberry with one of your personal email address, i.e. Yahoo, Gmail, or Hotmail, you can simply configure your Blackberry to use POP3 to pull the emails . If you are the corp user and would like to connect it with your corp mail server, i.e. Exchange server, you can configure it to pull the emails through OWA (Outlook Web Access). The nice thing about Blackberry is that you can have multiple accounts connected to one handheld and all get organized separately so you will never mess up your office emails with your personal emails.
The whole setup can be dramatically simplified by having a Blackberry Enterprise server installed in house. Any organization should have Express edition running internally when there are more than 5 handholds, and Enterprise edition when having between 5-15, and Enterprise edition on a dedicate server when having more than 15. The diagram below shows basically how the Blackberry Enterprise Server works.

Now I am getting serious now to think about having one. The whole idea of how emails get flowed and organized somewhat convinced me that the Blackberry IS something.
[prose from the pros] Devices like black berry have equipped mobiles with new technology and internet phone service has added value to their customers using this device. The skype download on cell phones has ended limitations to make free calls using computer. Companies like vonage are making more sophisticated software for their customers. Many internet phone services are offering more affordable deals for business and reducing their cost of calling. The internet voip is latest technology that has made possible low cost calling. You can see business of voip company is growing because of high demand in market.
]]> Because of that, I am now moving all my daughter's photo up on Flickr. It's so nice. All pictures uploaded to Flickr are all saved in different sizes from 75x75 to 1024x768 (free account) or the original size (pay account). I am so impressed that all these size of pictures are in such good quality. Flickr really does a good job re-sizing the pictures. Good work. Once all pictures are uploaded, I will be sharing it mostly with my family and friends in China, which is another good thing about the Flickr, and only uses the blog solely as blog to record the remarkable moment.
Because of that, I am now moving all my daughter's photo up on Flickr. It's so nice. All pictures uploaded to Flickr are all saved in different sizes from 75x75 to 1024x768 (free account) or the original size (pay account). I am so impressed that all these size of pictures are in such good quality. Flickr really does a good job re-sizing the pictures. Good work. Once all pictures are uploaded, I will be sharing it mostly with my family and friends in China, which is another good thing about the Flickr, and only uses the blog solely as blog to record the remarkable moment.
Once I am done this project, I will be starting uploading the video up on YouTue, which will be another fun work for sure.
[information improvisation] You can get cheapest domain name for making a website. Due to changing technologies web hosting is getting cheaper day to day. You can get to know all domain name rules to register a domain name for you check domain name info before registering whether it is available or not.
]]>Coincidentally, Jeff Atwood had a nice post, Computer Workstation Ergonomics, explaining in very detail how to achieve an ergonomically correct computer workstation, which basically was referenced from Microsoft Healthy Computing Guide claimed by himself as one of the best and most succinct references for ergonomic computing. Here is the summary of the key guidelines which I hope you will find helpful:
1. Get a quality desk and chair that provide the required adjustability. If you don't have the choice to pick the desk, try your best to get a better chair.

2. The top of your monitor should be at eye level, and directly centered in front of you. It should be about an arm's length in front of you.

3. Your desk surface should be at roughly belly button level. When your arms are placed on the desk, your elbows should be at a ~90 degree angle, just below the desk surface. The armrests of your chair should be at nearly the same level as the desk surface to support your elbows.

4. Your feet should be flat on the floor with your knees at a ~90 degree angle. Your seat should not be pressing into the back of your knees; if necessary, tilt it slightly forward to alleviate any knee pressure. Sit fully back in your chair, with your back and shoulders straight and supported by the back of the chair.

5. The last, when typing, your wrists should be in line with your forearms and not bent up, down, or to the side. Your keyboard should be directly centered in front of you. Other frequently used items should be nearby, within arm's reach.

[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
[information improvisation] Whether you are working on workstation or terminal computer, you should have web hosting services. The best hosting service is powweb as there are many people using this hosting service. According to reviews ix web hosting is best web hosting with fastest servers. This is providing best image hosting for image websites and uploading and downloading is so fast. Many hosting services providers are providing same services.
]]>1. Password Management - Issues include poor password policies or enforcement of those policies, re-use of passwords, and password storage.
2. Patches and Upgrades - Some issues here include no inventory (how do you know what to patch?), no reporting on status of patch deployment, legacy applications that are no longer patched, and the "deploy and forget" methodology of software deployment.
3. NTFS and Share Permissions - Remember that permissions are cumulative (except Deny always wins), never grant permissions to users and always use groups, install Windows 2003 fresh rather than upgrade and use security templates and GPO's to set and maintain security. Everyone having Full Control everywhere is never good, remember Anonymous is part of Everyone!
4. Too Much Privilege - Always follow the rule of least privilege! And never use a domain or enterprise admin account to run services.
5. Administrative Practices- NEVER use a domain or enterprise admin account for your day to day activities and don't use those accounts to login from a standard workstation. (in my own practice, bad, I haven't gotten started to use this principle that I have known for years)
6. Unused Services - needless to say, removing unnecessary services will reduce the attack surface.
7. Auditing and Logging - Auditing is crucial but it is also important only to audit what is important. (That is something I really need to focus on, really)
8. Backups - Always test your DR plan as well as your recovery procedures. And remember that backups are only part of your DR plan.
9. Security Education - It's a key to a secure environment.
10. Incident Response - NEVER touch the compromised computer, delete any files, or do anything without the approval of your security officer. Doing so could destroy the evidence needed to determine what happened and how to prevent it from happening again.
[A Reader's Toolbox] Latest file sharing applications have made it possible to share your documents across globe. The advent of data recovery program has enabled companies to recover their data if it is deleted. However data recovery is very useful because it can save all of your precious data. If you do not backup your data then you must have recovery programs. You will find bundle of software in data recovery group.
]]>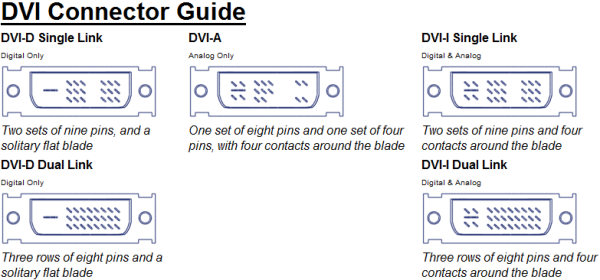
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]> Wondering how I put the snapshot on all the external links on my website? Is it cool by the way? It's so easy that just a few steps that you need to take to get it all set up.
Wondering how I put the snapshot on all the external links on my website? Is it cool by the way? It's so easy that just a few steps that you need to take to get it all set up. 1. Go to Snapshot website, http://www.snap.com/, and click Get Started button on Publisher and Blogger Tools.
2. Follow the instructions to get the code.
3. Copy the code to your website. Because it's Javascript code, just put them in the end of the page before the closing </html>.
4. And you are done.
You can have the choice to have snapshots on both internal and external links but I suggest only including the external ones as the site would look too much when having both. Also, if you are the end user and really want to have the feature on all web sites, you can download the plug-in on your browser.
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>
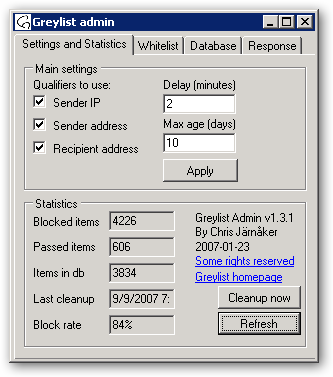 Greylisting, a method of defending email users against email spam, actually hasn't been widely adopted in most of modern anti-spam system. I am so impressed honestly, even at the first time when I heard of it. It greylists any emails from a non-recognized sender for a short time and temporarily rejects it. The assumption is that since temporary failures are built into the RFC specifications for e-mail delivery, a legitimate server will attempt to connect again later on to deliver the e-mail. Why would it work to against the spam? Because if the email is from a spammer, it will probably not bother to be retried.
Greylisting, a method of defending email users against email spam, actually hasn't been widely adopted in most of modern anti-spam system. I am so impressed honestly, even at the first time when I heard of it. It greylists any emails from a non-recognized sender for a short time and temporarily rejects it. The assumption is that since temporary failures are built into the RFC specifications for e-mail delivery, a legitimate server will attempt to connect again later on to deliver the e-mail. Why would it work to against the spam? Because if the email is from a spammer, it will probably not bother to be retried. Sounds good but how can I implement it? It depends on what kind of mail server you are running. Greylisting implementations have a pretty full list how to implement it based on the platform. We are running Exchange server so basically this Grynx Greylist Freeware works for us.
Installation is easy, download the package and extract it onto the server where SMTP server runs, but the configuration is a little bit tricky. First of all, I don't want it run on the same Exchange server so I have to load another Windows 2003 Server with SMTP service enabled, and configure it to relay all incoming emails to the internal Exchange server. Secondly, configure it to use SQL database rather than an Access database. Finally, updating the firewall so from now on all incoming emails will go to the new SMTP gateway with Greylisting enabled first before hitting to the internal Exchange server.
Everything runs beautifully, it has blocked over 4,000 from coming into our mail server just about 10 hours after I implemented it. There is a big issue that could cause it not being used eventually in our organization.
The most significant disadvantage of greylisting is the fact that, like all spam mitigation techniques, it destroys the near-instantaneous nature of email people have come to expect, and throws email back to the early days when it was slow and unreliable. A customer of a greylisting ISP can not always rely on getting every email in a small amount of time. Thus email loses its function as easy and effortless vehicle to transfer electronic information instantaneously.
Because of this, I have to take a step back and put the schedule on the firewall so the rule that redirects emails to the greylisting enabled SMTP server will be only on after hours. It's still a huge help because it reduces a huge amount of spams that we need to monitor. Whoever monitors all filtered spam for any false positives still owes me a big thank-you.
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>It has all the nice features of the reviewed version, is still available in a free version and has a lot of improvements - and more to come.
Cheers,
Chris
www.Grynx.com www.Proxmea.com]]>
So which one looks attractive the most to you? iPod nano suites me so well because the shuffle is too basic while the classic might not worth to have once the touch hits the market early next year, which will be obviously too expensive to me. I am so tempted to get one now because the price is also very competitive, $199 for a 8G nano at the moment.
However, I am still struggling with the idea whether having one of those iPod toys or owning a smartphone that looks have anything I wanted. iPod toys only have the things for entertaining but smartphone has a lot more, including emails, WiFi, network accessing but I just don't know how good they are when I want to use them for entertaining.
By the way, a better quality of ear-bud style of headphone is highly recommended if you want to own one of these toys. Noise-canceling phone is not recommended when using on daily basis because it's too dangerous but noise-isolating style is highly recommended. Apple store has tons of choices for you.
]]>Drill/Driver
As the name suggests, does double duty as a drill and as a screwdriver. So you can use it to assemble furniture you bring back from a retailer in a box, hang the occasional door, replace a lock on a door, hang pictures, etc.
Screwdriver
If a drill/driver seems like a bit too much tool for your needs, then a battery-powered screwdriver might be just what you need.
Circular Saw
Whether you are putting up a fence in the backyard, fixing a deck, undercutting a door, or building a bookcase for the family room, a circular saw will get the job done faster and with less muscle power than any handsaw.
Jigsaw
While circular saws do a great job of long cuts, jigsaws shine in places no circular saw dare go. When laying down hardwood floors, for instance, you may find it necessary to make precise cuts in order to get the flooring material to fit perfectly around door frames or other irregularities. Or you may find it necessary to cut a hole for a new sink and faucet into new countertop material when renovating a kitchen or bathroom. Only a jigsaw has the compact blade, and the compact range of movement to make these precise cuts.
Reciprocating Saw
It can cut through almost anything, which makes them ideal for demolition work. So if you are taking apart an entire room, or simply cutting off the drain pipe underneath your sink, a reciprocating saw will cut through almost anything you let it feed on. Also, due to the unique shape of this power tool, it can easily get into tight corners and cramped quarters, places a jigsaw or a circular saw simply can't negotiate.
Lights
When working in and around the house you'll often find yourself in areas where it's darker than you'd think. An extra light, especially one with a flexible neck, is a really good idea.
Laser Level
Nonetheless to say, it's a must-have tool that runs much better than the old fashioned liquid filled levels.
And if you are planning on tackling larger projects in and around the house, you will need more than just a few basic power tools to get the job done right.
Hammerdrill
These incredible tools like just a regular drill/driver, but with one distinct difference, the hammerdrill setting that not only spins the concrete drill bit, but also vibrates it up and down thousands of times per minutes.
Miter saw
This powerhouse is a must for serious renovators.
Nailer
You have to know what you will be using the nailer for before making an investment. A good bet for all around nailing would be a Brad nailer that shoots 18-gauge nails. It's agreat nailer to use when tacking wood in place until adhesive sets on your projects.
Compressor
A lot of choices are on the market. Which is the best depends on how many power tools you will be hooking up to the compressor at once, and whether or not you mind hte compressor cycling on every few minutes to refill the tanks. You will also have to choose between gas and electric models.
]]>It certainly hurt me too as after spending a little money and tons of time transferring and uploading my little Sammy's photos to Flickr, all my friends and families see is the red cross-marks all over the place on the page. They've been throwing the questions back to me asking why I wanted to share cross-mark pictures with them.
Anyway, after did a few Google search, a simply workaround in the link below can by pass the filter but you have to use Firefox to be able to do it because this little tool is an add-on in Firefox. Sorry IE, there is another booming opportunity for Firefox.
http://www.ericmacknight.com/wordpress/?p=76
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>Google just recently announced that their popular Gmail now supports IMAP. That's so sweet. Sync your inbox across devices instantly and automatically. Whether you read or write your email on your phone or on your desktop, changes you make to Gmail will be seen from anywhere you access your inbox. But how about my customized labeling system? Will it be lost when using IMAP? Not al all. Your own labels appear as the folders in your email program. Just exactly what you want.
Am I going to use it? Hmm...not likely. I am so addicted with web-based email program. Many of Google's features keep me stay tuned with my browser all time as long as I am online.
[advertisement] If you happen to be a fan of mini moto or pocket bike and are looking for a parts for your toy, check it out these parts listed on kncnet's eBay store
]]>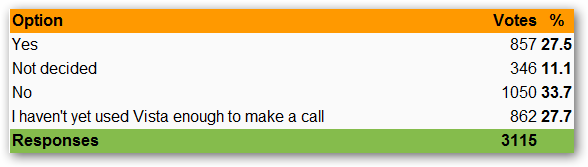
- Ensure your links are large enough to easily click.
- The first link is the most important one.
- Don't link everything.
- Don't radically alter link behavior. Very good point that I don't follow all time but will be from now on.
- Don't title your link "Click Here".
- Don't link things the user might want to select and copy.
- Don't include icons on every link.
- Don't make your content depend on links to work. Good point too. Not everyone will click on the hyperlinks. Either they're too busy to click every single link you put in front of them, or maybe they're reading your article in another format where they can't click on the links: print, offline, or mobile. Either way, it's important to provide the context necessary to make your content understandable without the need to visit whatever is behind those hyperlinks.
- Don't hide your link. Give them a distinct style, or underline them all time.
- Don't mix advertising and links. Single-underline is for the hyperlinks while double-underline is for advertisements.
- Don't obfuscate your URLs.
Jeff also mentioned that Keyvan Nayyeri's Simplify your URLs would be a fantastic starting point. And using DecentURL to polish the ugly URL.
]]>The majority of today's anti-spam products on the market detect spam by analyzing the sender, i.e. DNSBL, SPF, Header Checking, etc., or email content, i.e. Bayesian. This so-called breakthrough technology developed by Abaca didn't use any of those, instead, it detects the spam based on its new, unique, and revolutionary receiver-reputation formula. It works quite awesome according to what the testimonials say on its website.
I have been fighting with Spam for last past 5 years by utilizing various technologies and tools. It's way less than perfect but still manageable, which is why I hope a new revolutionary system like this that dumped all old technologies would win the game overall.
]]>http://www.freesoft.org/CIE/RFC/1123/90.htm
This is kind something new to me as I never had any trouble sending email from this 5-year-old mail server because of invalid value in HELO. Yes, I did use internal domain name in HELO but, according to what the link he referred to me, it shouldn't be the reason why the email was rejected.
5.2.5 HELO Command: RFC-821 Section 3.5
The sender-SMTP MUST ensure that the <domain> parameter in a HELO command is a valid principal host domain name for the client host. As a result, the receiver-SMTP will not have to perform MX resolution on this name in order to validate the HELO parameter.
The HELO receiver MAY verify that the HELO parameter really corresponds to the IP address of the sender. However, the receiver MUST NOT refuse to accept a message, even if the sender's HELO command fails verification.
Anyway, in order to avoid the trouble like this and follow the RFC compliance, I took the advice and changed our HELO to the valid domain name.
]]>
The story talks about a DNS problem that was caused by an un-registered .net domain name used in AD but being registered by their ISP, which changed all DNS records once it's been registered. It took the whole network down for two days to have them discovered and finally fixed the issue. The author concluded that there were two lessons that they had learned from this incident.
First of all, if you're using an ISP and you're having an Internal problem, be sure to communicate with the ISP. Before you start changing your DNS setup, ask the ISP's technical staff whether they've changed anything in their configuration.
Question is why didn't register the domain in the first place. The issue wouldn't happen if being done so. However, even the domain was registered, my suggestion is to remove your domain registration including DNS from your ISP and move it to a dedicated domain hosting company like register.com. By doing that, it eliminates all the potential risk mentioned above and you will have more control to your own domain. Besides, anyone who is able to configure AD should be able to handle the tasks like changing DNS records.
Also, I learned my lesson about using the .net domain. Now I use .local for all internal DNS settings. You can't get trouble with that one because you can't register it.
Yes, it's true that using .local as internal DNS name would be a good idea. I learned that lesson years ago and has been using it ever since then. However, .local is not a recommended TLD names for part of an AD tree name if you want to obtain the digital certificate from 3rd party certificate authority because simply it is not a standard Internet domain name.
]]> We had this traditional event this afternoon. As always, it's fun and full of excitement. It's my fifth time in the event and I has enjoyed them all. Gifts are full of surprise to me and everyone else.
We had this traditional event this afternoon. As always, it's fun and full of excitement. It's my fifth time in the event and I has enjoyed them all. Gifts are full of surprise to me and everyone else. Why we call it Secret then? Basically, about a month before the event, everyone draws a name from the pot and then buy maximum $25 gifts, and put it secretly under the Christmas tree with "Santa" name on it. It's called Secret because you know whom you give to but don't know who gives to you.
And in order to help people to choose the right gift, we even have a "Gift Idea" page on our Intranet where everyone who participates the event can put their own favorite, what they like and what they don't like. It's so helpful that everyone can get exactly what they want from the Santa. My this year's wishlist is an interesting book of any kind or any home decoration stuff for my new home. And here is what I got, a small nice medal photo frame and a book from Uncle John's Triumphant 20th Anniversary Bathroom Reader, exactly what I wanted.
]]>I agree too after having been used Vista on my new laptop for almost over half year. I consider myself as a pretty heavy load user. My desktop constantly has 10 or more windows open and many different of services running in the back, but it is a lot slower than running the same thing on my 4-year-old computer on XP. In addition to that
- Aero Glass is still too new to work with the cool dual-monitor support software, which prevents me from running this type of software to take advantage of using dual-monitor.
- Windows Explorer hangs a lot of time when I browse a new network folder, no matter how many files in it.
- Stupid network settings make me a lot harder when working at my home network. Yes, a lot more secure but I rather have a network that works. And yes, my wireless frequently tells me that I have the problem to get an IP address from DHCP server at home. Thankfully, I do not have the same problem while I am at work with the same laptop.
- No more large font option (don't like enlarge the DPI to 120% or whatever) to enjoy the bigger text on the desktop.
- etc. etc.
My answer to the question when I will be upgrading my Vista to XP is, whenever I have a chunk of time because reload and reconfigure everything is also painful. Stuck with Vista for now and missing my old XP badly everyday.
]]>WriteMaps is a free web-based tool that allows you to create, edit, and share sitemaps online. As a WriteMaps user, you and your team will be able to build and access your sitemaps from anywhere, without having to rely on proprietary desktop apps and static files.
I believe that it would be pretty useful to me who works as a solo web developer quite often. Time to put all my sitemaps on now.

 According to the recent stats (learned from today's Province), digital frames, Wii, and guitar hero III are the most popular gifts for this year's Christmas. And apparently, they are all sold out at any story at the moment. No wonder my friend are going to across the border to see if there is any chance there to get a Wii for his son.
According to the recent stats (learned from today's Province), digital frames, Wii, and guitar hero III are the most popular gifts for this year's Christmas. And apparently, they are all sold out at any story at the moment. No wonder my friend are going to across the border to see if there is any chance there to get a Wii for his son. Interestingly, the report also states that electronic stuff are man's favorites and gift certificates top for woman while jewelry is the least man wants and sports gear is at the bottom of the wish list for woman. Good to know when you are out of the choices for the above three though.
]]>
It works beautifully in my regular Gmail account but I am using email with Google Apps most of the time which doesn't seem to work with RTM. So I emailed RTM asking if there is any way we can implement this into my Google Apps email. Their reply came back in such a surprisingly fast way. And yes, turning on the option "Turn on new application features to my domain before they are rolled out to all Google Apps customers" in Domain Settings in Domain Manager definitely did the trick. I will be enjoying it for sure.
]]> I won't. I will never ever give the lottery ticket to someone I know as the gift. Why? Because this is the stupidest thing to do for numbers of reasons:
I won't. I will never ever give the lottery ticket to someone I know as the gift. Why? Because this is the stupidest thing to do for numbers of reasons:
- What would you feel if the person who got the lottery you gave won the big number? Happy for that person? I don't think so.
- I am using up my limited once a life luck to someone else, which is dumb.
- This simply is not everyone's favor anyway. People who has it from me would think I am not serious about the relationship at all.
- etc. etc.
I was so dumb the other day that I borrowed my lovely little sweetheart's hand to buy last Saturday's 649. Fortunately, I was lucky that I didn't win. Otherwise, I would blame myself so hard because I used up my daughter's once a life luck for my own sake.
A little off the topic...well...because this is holiday season...Merry Christmas, everyone whoever happened to come cross my site...Happy New Year too!!
]]>]]>
Freeware application Secunia Personal Software Inspector is sort of like Windows Update for your installed software, monitoring your installed apps and notifying you of available security updates. When you run your first scan after installing Secunia, you'll be presented with a list of insecure apps that have available updates, "end-of-life" apps that are no longer being supported by the developer, and patched apps that have the latest security updates. Keep in mind that Secunia is not an anti-virus software, but more of a preventative tool for ensuring that your software is secure as it can be.
I downloaded and installed on my computer right after I read its post. The first scan only tool a few minutes and discovered that I have 7 in-secure applications that need to be updated. Simply clicking the download solution icon will either direct you to the website that provides the patch or download the patch right away. Pretty neat.
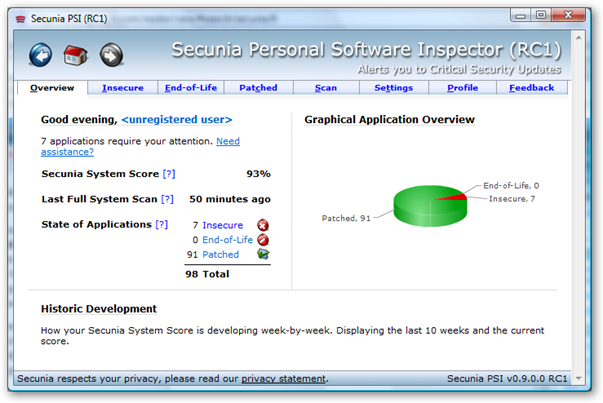
Staying healthy while seeking the chances to make more money.


Studies by the Chronobiology Research Institute show that for those on round-the-clock schedules - sailors, astronauts, gamers - it's more effective to recharge in short stints. For survival, the brain will eventually adapt by entering the REM state much faster. The cumulative result: a higher percentage of the best kind of z's. The most time-efficient strategy calls for a 20-minute nap every 4 hours. Once you start dreaming during naps - a sign you've hit REM - you'll begin to feel better.
Interesting. I sleep averagely 4-5 hours a day but have two naps on both way to work and back home on the transit, 20-minute each. I do feel pretty tired sometime but most of the time I am totally fine. Kind close to the trick. Thanks to the transit and the studies referred by Wired, so I can actually live longer in another way.
By the way, Wired does warn that the long-term side effects of this tip are unknown but you will have plenty of time to worry about it with only two hours of sleep a day.

It's always true that the most threat to the network are from inside the office. While it's hard to technically lock system down it would be more efficient and useful to have a more strict and seriously detailed policy in place. And be sure that the words about the policy get to people's attention.
[updated on Jan 11, 2008] Apparently, people in PCWorld reviewed and realized the potential risk of this original post (note that I included the link here now) as it has been removed off the website but maybe still archived somewhere in their storage.
]]>But in his recent Can Microsoft Save the Zune? he listed a long list of things that Microsoft needs to do to save the Zune in the market, and made the final thoughts as:
Will implementing these suggestions be enough to save the Zune? You know, I'm not honestly sure. I basically switched to the Zune for two months straight but found myself missing more and more features that I just took for granted on the iPod/iTunes side. Yes, Apple's platform has its own issues, believe me--performance being perhaps the most obvious--but at least on the Apple side the pros outweigh the cons. Right now, that's not the case with the Zune.
When it comes to digital media consumption, nothing is written in stone. My music library is largely comprised of DRM-free MP3 tracks. My photo collection consists solely of standard JPEG files. Movies are, sadly, the most complex: I've got a weird mishmash of H.264, WMV, and AVI/DivX/Xvid files, and for now at least, no single device or software solution plays them all. Things can and will change in the future. But unless Microsoft is serious about improving Zune dramatically--and quickly--through 2008, this game is already over. Many consumers--myself included--will simply continue looking elsewhere.
Meantime, Bill Evjen posted his review to the Zune and claimed that Zune 2.0 - the best player on the market!
Ok, seriously, which one should I go with then? Staying with iPod might still be the safe move but I would take my chance to give Zune a try, because simply I like bigger screen to enjoy the movies and the Wi-Fi to enjoy the seamless quiet sync.
]]> Based on Gate's statement at this weeks' Consumer Electronics Show, Windows Vista was aboard 39% of the PC's that shipped in 2007, more than 100 million copies since the OS launched last January. No bad figure at all, a little surprised me, to be honest. However, the real question is how many these Vista computers are actually running Vista.
Based on Gate's statement at this weeks' Consumer Electronics Show, Windows Vista was aboard 39% of the PC's that shipped in 2007, more than 100 million copies since the OS launched last January. No bad figure at all, a little surprised me, to be honest. However, the real question is how many these Vista computers are actually running Vista. I started buying Vista pre-loaded computers a few months back but none of them are running Vista at the moment, they are all running XP instead. But they should be all counted as Vista sale. There are reasons and benefits why I am doing this, which I believe there are many others doing the same way as well. XP still dominates.
Note that any computers running Vista Business or Ultimate are eligible to run XP Pro without extra cost. You just need to find the right media to do so. However, not every vendors in the market offer the downgrade media for free. I don't know why but I believer whoever doing so definitely offers the better service and makes a good decision in the market. At least, I have switched from Acer to HP recently because simply HP offers this service without any cost. By the way, HP's support service is awesome.
]]>For anyone inclined to daydream about a Web business that would all but run itself, two other details may be of interest: Mr. Frind operates the business out of his apartment in Vancouver, British Columbia, and he says he has net profits of about $10 million a year.
Scobleizer apparently knows Markus and realized his work way back in 2006, and revealed what the secret is to make Markus so successful.
What’s the secret to his success? Ugly design. I call it “anti-marketing design.”
Huh?
He says that sites that have ugly designs are well known to pull more revenue, be more sticky, build better brands, and generally be more fun to participate in, than sites with beautiful designs.
Ahh, yet another example of anti-marketing marketing.
Was he joking about it? Not really. The site was designed to be easy to use, fast to load, and uncluttered. I believe these are the keys truly to his success. Look at Google, Craig's List, or even Amazon and eBay. None of them look pretty but all designed in simplicity and fast.
Markus picked ASP.Net because, according to what he says, it's trivial and easy, and gets the job done. His stuck with what he knew and got really really good at it attitude is also saving his a lot of time and using these time to concentrate on things that are more profitable. He did spend a lot of time studying SEO, which is probably another big factor to become the #1 Adsense user in Canada.
Does it ring a bell to you? It does a lot to me!!
]]>So funny, it's claimed as the smallest laptop in the world that can fit in an envelop. Why does a laptop need to sit in an envelop anyway? Though, it looks so impressive when Steve Jobs carried the Air out on stage actually in that way.

 These Vista annoyances apparently has bothered Michael Otey quite badly that he put it public in the latest Windows IT Pro magazine. I agree most of them.
These Vista annoyances apparently has bothered Michael Otey quite badly that he put it public in the latest Windows IT Pro magazine. I agree most of them. 10. Application imcompatibility. - This is quite obviously people complain the most. And yes, most of the cool apps you run on XP have to upgrade to the version that compatible with Vista, usually it costs money.
9. Windows Areo hardware requirements. - This annoys me the most recently because I had dual-monitor over two computers setup recently at work. Because its WDDM video driver is not compatible with most other XDDMs, I ended up having XP box with the primary and Vista as second, which is so inconvenience on daily basis. I am tolerating this annoyance now and am patiently waiting for a work around from MaxiVista, the software I used to set up the dual-monitor. Enjoying the wider space though.
8. Too much UAC - Agree, and this is the first thing I turn off after I had Vista installed on my laptop.
7. Lost wallpapers and themes
6. Losing Windows Explorer settings - I am a two-column Windows Explorer person and Vista version of Windows Explorer seems to be ok for me.
5. Explorer drag-and-drop
4. Anti-virus incompatibility - True but ok for me as I am using the latest free AVG instead of Symantec.
3. VMware virtualization software - This seems ok to me as I use VMware server on other machine to create the image and only use VMware Player on Vista to run the image. I also have Virtual PC loaded on Vista too. Both seem to be working properly so far.
2. Dual-boot difficulties - This was the issue to Michael because of the no. 3 issue. Since I don't have that issue, dual-boot method is still staying in my archived toolbox.
1. All-in-Wonder incompatibility
By the way, I stole the angry baby from Viral Tarpara's Vista Desktop Search Annoyance.
I have to confess that I did say I am extremely happy with Vista in tools on my computer but be honest, the more I use Vista the more I miss XP, especially the performance. I am sure that if I run Vista on my current computer it would be at least 50% faster.
So far, XP wins but XP will be out of the market end of June this year. Should we do something like the petition campaign which is happening on InfoWorld right now to save Windows XP for longer life? I believe so and I signed. Here is the quote from the article which I like the most.
]]>In many respects, Vista is like the Windows Millennium Edition that was meant to replace Windows 98 in 2000 but caused more trouble than it was worth. At that time, Windows 2000 was promising but didn't support a lot of hardware, so users were stuck between two bad choices. Without admitting Millennium's failure, Microsoft quietly put Windows 98 back on the market until the fixed version of Windows 2000 (SP1) was available. Microsoft needs to do something like that again today.
I have been using TaxWiz for last 5 years and was very satisfied what they offered. It might be true that Taxwiz wasn't as good as QuickTax but $19.99 for 4 returns with pretty easy use and accurate software really made it as a serious competitor to QuickTax. So QuickTax mad a quite smart move and bought TaxWiz early 2007 and discontinued TaxWiz right away. Fortunately, due to largely requests from TaxWiz users and the bad acquisition timing, they had no choice but still leave TaxWiz survived for the tax year of 2006, but you had to purchase the copy from retailer store, no online download at all. I, as well as my other 2 friends who also had been TaxWiz users for last past 3 years, managed to have our year 2006 tax filed via TaxWiz, even though we all had no idea what we are going to use for year 2007.
As we are in the new year, it is time now for us to think how we are going to prepare our taxes. Too bad, QuickTax offers a very ridiculous price range to its customer this year, which is a typically bad news for a user who used to be Taxwiz' customer because simply you are not respected. For my case, I have to spend $39.99 to prepare my tax online, meaning that I might not be able to obtain a physical of your own tax file copy. I need to double the price to $79.99 in order to do so, while I used to only spend $20 the most every year. How ridiculous it is!! I have seen a lot of merging cases before but to be honest, I never seen a business model like this after the merge. QuickTax thinks that buying its competitor's company, burying its software into the soil, and offering its customer a much higher price software would simply get much higher profit. Sounds logical, eh??
No, I am not going to let them to get my money. A business model like this simply is not going to deserve my money. I am going to review their other competitors products to see if there is any that suits my feet. But preparing the worst, I rather pay more money to my accountant.
]]>Take a look at this link. I recommend Studiotax. Its FREE and does it all.]]>
The only downside I noticed was that if you've moved recently (and it's your first time filing your taxes at your new address) then they disable the "File Online" option and force you to print out your taxes and mail them in. At least the hard work is done for you. ;)]]>
 InfoWorld informs its users that Microsoft warns businesses of impending autoupdate to IE7. Time to say goodbye to ancient old IE6 now. Microsoft said this move would no longer require users to prove they owned a legitimate copy of XP before they were allowed to download the newer browser, and the move was prompted by security concerns. Nice move and would save XP in some way. However, the more concern should come from the server which we, as IT pros, need to stay caution and keep our eyes on. Blocking it from upgrading on the server would be a good idea to think about.
InfoWorld informs its users that Microsoft warns businesses of impending autoupdate to IE7. Time to say goodbye to ancient old IE6 now. Microsoft said this move would no longer require users to prove they owned a legitimate copy of XP before they were allowed to download the newer browser, and the move was prompted by security concerns. Nice move and would save XP in some way. However, the more concern should come from the server which we, as IT pros, need to stay caution and keep our eyes on. Blocking it from upgrading on the server would be a good idea to think about.
At least, InfoWorld didn't think this is as bad as the Windows XP cut-over which happens end of June this year, so they didn't launch another petition trying to save IE6. I wouldn't if they do because moving to IE7 is a must go, even though FireFox runs way much better.
]]> I was a fan of Lookout and still is. It was a must have add-on that I can't live without when I was still using Outlook 2003 because of the way how fast is to search anything in your Outlook. I stopped using it once we had mail archive system installed because by utilizing both email retention and archive my Outlook doesn't have many emails at all. It is often quite easy to do a search over the archive system too. I stopped using it also because I don't use Outlook for my personal emails anymore. I am using Google Apps.
I was a fan of Lookout and still is. It was a must have add-on that I can't live without when I was still using Outlook 2003 because of the way how fast is to search anything in your Outlook. I stopped using it once we had mail archive system installed because by utilizing both email retention and archive my Outlook doesn't have many emails at all. It is often quite easy to do a search over the archive system too. I stopped using it also because I don't use Outlook for my personal emails anymore. I am using Google Apps. I also heard and was hoping that Microsoft would make the search better in Outlook 2007. But it's obviously not the case. At least, Joel Spolsky has a big complain about it.
The search feature in Microsoft Outlook 2007, frankly, sucks big time.
It's slow. Searches take about 30 seconds for me. (I have about 10 years of email).
The search quality is atrocious. I regularly get 50% garbage results mixed in that have nothing in common with my search terms, and the message I am looking for often doesn't come up.
Joel also missed Lookout very much but he was locked out by Microsoft in Outlook 2007.
The tiny company that made Lookout was bought by Microsoft. It must have been one of those HR acquisitions, because the Lookout technology was thrown away. Mike Belshe only spent a couple of years at Microsoft before moving on.
When Outlook 2007 came out, it disabled Lookout, and allegedly this wasn't supposed to be a big deal because Outlook 2007 has search "built in." But the built-in search is, as mentioned, ghastly.
Luckily, he finally found the original author, Mike Belshe, who has found a way around to make Lookout to work on Outlook 2007, which works like a charm. However, since Microsoft bought Outlook and made it disappear, it might not be easy to find the installation file. I, for example, didn't make a copy of it. I probably will shot either Mike or Joel an email asking for one copy if I find I will need it again one day.
The question also remaining in this case is why Microsoft didn't include this awesome tool in its latest Outlook!!
Update (Jan 24, 2008): Leon has a better solution in his blog, which works more compatible with original Outlook 2007. Thanks Leon. There are also some other folks who mentioned lightening searching in Cache Exchange Mode. I agree!!
]]>I have a better solution. Read my blog for details:
http://www.wirwar.com/blog/2008/01/22/search-e-mail-at-lightspeed-using-lookout-with-outlook-2007/
]]>
I worked with Lookout too but changed too Looken and be more than satisfied with it!]]>
CRA Certified software is definitely a good and trustful place to look at, even though it states in their website that
There is no software or Web application certified for use with the 2008 NETFILE Program (2007 tax return) at this time.
Among these alternatives, my accountant is going to use TaxTron, my assistant is using UFile, and some of others recommend free StudioTax. I might go with Ufile as it offers an important feature that transfers data from your previous year of QuickTax or TaxWiz file. Sounds sweet if it does well. If no, StudioTax will be next in the line. Why? Because it's free, and I am cheaper when I get older. :)
]]>My brother has used UFile for several years and I was too stubborn to look at it. I am glad that QuikcTax gave me a reason to try it. I am sure a lot of people will this year. ]]>
The truth is that Google has become the new Microsoft, and if we want to avoid a repeat of history, we need to allow the formation of a real competitor to keep them honest. Otherwise, all the ills perpetrated on the world by Microsoft in the nineties will likely be repeated again, this time by Google.
Nobody wants to see this happen. Google is all over me know, using their Apps for my email, their Reader to read, their notebook to capture my quick notes, analytics to analyze my websites, toolbar is on every browser, and etc. etc. And thinking about what other online services I am using then, very few, to be honest. Flickr is still my main depository for storing my pictures but hotmail and yahoo mail are long gone even though I am still keeping my hotmail and yahoo addresses but that's all, only keeping. Yes, I like and enjoy what Google offers but sometimes its being too big too dominant bothers me and worries me. That's because, simply, we all know that real competition makes products better, pushes innovation from happening, which in the end all benefits end users, like us.
Zoli passed two great quotes in his blog and there are many all over the place on Internet but I like this one from Microsoft-Yahoo: The deal of the dinos better.
Will this be big enough to beat Google? No, because big won’t win in the end. Open will.
So then, what would happen if the deal comes to real? Duncan Riley from TechCrunch's Microsoft-Yahoo: What Will Stay And What Will Go? is a pretty good to start but not enough because I also agree that "open" matters.
<update date="Feb 8, 2008">
Bex made a really good point that might reveal the real reason why Microsoft wants this deal done, the big portion of the enterprise search pie.
</update>
1. Internal links go to the same page;
2. Internal help info links open in a new window or pop up the modal in the same page with close button in it.
3. External links go to the new window or tab;
I also subscribe the snapshots add-on on my blog for external links so it adds another layer for users to take a quick look before actually clicking through.
However, there are quite a lot debate in David Direy's recent same post, in which a lot of people commented that all link should open in the same window, no matter whether the link is internal or external. They claimed that this is something that should leave for the reader to decide. It makes some sense but why? Why would people like the idea to give their readers chances to leave their site for something else? This quote from one of the commenter might be one of the reasons.
However, for not so tech-savvy people’s sake, it’s best not to open links in a new window. They really get lost with the disabled Back button. I was opening links in a new window for one of my client’s sites, until I started getting calls from her, asking how can she get back to the previous page.
It's true. Small usability issues like this does bother a lot to non-tech-savvy people, and we need to put more weight on them when determining which behavior we should be taking.
By the way, a quick guide of When to Open Web-Based Applications in a New Window is a pretty good reference to check.
<update date="Feb 8, 2008">
It appears that having links to popup via Javascript isn't a smart idea either because 1) it might be blocked by popup blocker; 2) it's not so search friendly; 3) it breaks the common rule to open the link, i.e. no middle-button, and open in new tab disappeared from right-click context. There will be no JavaScript type popup on my site anymore.
</update>
Recently, I upgraded our GFI MailArchiver server to the latest version but encountered an database schema update problem after. So I emailed their support team with a brief information about the problem. I had to email them 3 times to finally get a human to response, and of course, I got 3 templated email response with 3 different ticket numbers. Then I was told to provide a detailed description of my issue again. Obviously, my original message was archived and unreadable for some reason. Then I was told to generate a log file by following their instruction, and then I was told to give them a call to discuss in person, and then I got the following another templated message (not mentioned that they even put my case into the wrong product category) after I called and left the message which was gone mystery again.
My last correspondence with you regarding Support Case xxxxx has gone unanswered for three days. Please respond with the requested information so that we can proceed toward a resolution. If the issue has already been resolved it is not necessary to respond, as we will archive the case after 3 days.
And then I called them again, and got hold of another tech guy who offered me a solution which didn't help to solve the problem. And then my case went quiet for 3 days after I told this guy that your solution didn't work. And yes, because there was no communication for 3 days I got the same templated message again. After I replied with complaining that their support service sucks, he finally seriously took look the log file I provided earlier and quickly pointed a solution which solved the problem immediately.
The whole case took over 20 days to get addressed, and as you can see, was full of miscommunication, in which templated customer service obviously played a very important role, which decreased the human interactive ability and reduced the quality of the service as the result. Sorry, folks in GFI, I can list a full of other examples here but I just want to point it out so somehow to get your attention. Your products rock but the service definitely has a huge room to improve.
]]>I head GFI's support team in the EMEA and I am sorry for the bad support experience you had in this case.
I tend to disagree with you on the fact that email templates are a bad idea when providing a support service. For example, the automated email can be used to ensure that the email has been received by the support team. Apart from that, such emails may also provide links to online resources, which would provide an answer to the most common queries.
I do realize that in this case, our case management software would have been smarter if it realized that you had emailed us recently, and would not have sent out the automatic reply on your second and third email.
I do feel that this blog is mainly instigated by the bad support experience. I would be grateful if you could get in touch with me, so we could discuss his further so we can take appropriate corrective action.
Thanks you,
Nicholas Sciberras
Senior Technical Support Supervisor - GFI Software - www.gfi.com
]]>
I do like GFI's products and have been a happy GFI's customer for over 4 years. My original intention to use GFI as the example is to try get your attention to get your awesome product even better. Your product rocks.
Cheers, Kent]]>
Quote from Merlin Mann's:
Time & Attention are finite.
Scott's quote on Merlin's
No matter how hard you try, there are only 24 hours in a day. There comes a point where regardless of how well organized you are, there are things you cannot fit in.
Tim Ferrs's Quote
Time without attention is worthless, so value attention over time.
Then Lister's Law:
People under time pressure don't think faster.
And the final quote from Scott:
The next time things get really hectic, instead of getting stressed out and trying to squeeze everything in, think about what things you do not really need to do.
Very true, being swamped by so many ideas, and projects recently, I need to find a way out. These will be very helpful.
]]>We're aware of it, but are listening first and foremost to feedback we hear from partners and customers about what makes sense based on their needs. That's what informed our decision to extend the availability of XP initially, and what will continue to guide us.
Good, at least, they are aware of it, and they are listening but obviously, XP will still die, even though it might live a little longer. Thanks to over 75,000 people who signed their names on the petition.
We're aware of it, but are listening first and foremost to feedback we hear from partners and customers about what makes sense based on their needs. That's what informed our decision to extend the availability of XP initially, and what will continue to guide us.
Microsoft seems pretty happy with the fact how overall market goes with Vista but still, there are more vendors that understand the needs of XP and offered the opportunity to downgrade to XP pro, including Dell, Hewlett-Packard, Lenovo, Fujitsu, and more recently, NEC.
So upgrading my laptop to XP doesn't sound a good idea at this moment then.
]]>It's quite obvious why MS would like to make this move, but to a struggling company for years like Yahoo, what are the other options??? The rejection only looks good if Microsoft offers the second or third deal but would be stupid if they choose to wait for another year or just walk away.
The market seems to welcome Yahoo's move though as YHOO is up $0.40 and MSFT is down $0.60 at the moment when I posted.
<update date="Feb 11, 2008">
Microsoft respons to Yahoo's rejection that the offer is fair. I agree, because, how could an offer that raised Yahoo's stock by 60% be claimed as "undervalue"? Where does this $40 per share thoughts come from? Now Yahoo, as Microsoft has kicked ball again, what's your next move? I think I should take "bye-bye" off the title now, and put "hi" in it instead.
</update>

Basically, based on what I was told, all features are existed in all editions. Quickbook just doesn't provide the easy tool to help you find out. For example, all forms for self-employment are also existed in standard edition but you will have to dig it out yourself.
However, no confirmation whether or not it is true. I wasn't willing to take my chance to buy the standard edition to give it a try but my friend generously offered her copy to me for free. So I will update here if it turns out true.
]]>While watching the demo I realized the way I look at the world was about to change. While listening to Wong I noticed a tear running down my face. It’s been a long while since Microsoft did something that had an emotional impact on me like that.
...
Imagine if Microsoft did 10 things a year like what Curtis and Jonathan showed me yesterday? If the innovation engine at Microsoft were working that well there wouldn’t be any pressure to buy Yahoo. Heck, and if there were a constant stream of stuff like what I saw yesterday Yahoo wouldn’t be resisting going to Microsoft. They’d +want+ to go to Microsoft. Yesterday is the first time since leaving that I wish I were back working at Microsoft.
I am damn curious now, seriously too. :0
<update date="Feb 27, 2008">
Ok, as Scobleizer promised, today he revealed what actually made him cry, the WorldWide Telescope. The site doesn't really have anything in it so can't really tell how awesome it is. But according to what Scobleizer described, it sounds very amazing, like magic indeed. Kind a bit of beyond my interest though.
</update>

And I want one of these, to boost my crawling Vista.
]]>When I was at school learning software engineering, I was told that there is no software that is bug-free, meaning that making perfect software is nearly impossible and all you can do is to use whatever techniques and tools you have to test and eliminate as much bugs as possible to make the software as much close to perfect as possible. Testing or QA is so vital, even more nowadays, that any little ignorance would hurt the software to decrease the quality as the result. So how and what should I do, as a solo developer, to make better application next time by providing more efficient testing methodology?
First of all, I would adopt Unit testing mode when actually programing the application because it validates units of the code to make sure that they are working properly, and more importantly it forces me to stop and think about the test. Could be a nice approach. It apparently would discover and catch the bug mentioned above.
Secondly, making more detail testing plan in writing and complete it through before handing over for end user beta test. And if possible, ask other testers who also has programming skills to test my application, mainly to test application's logical, structure, functionality, and usability.
Thirdly, convince and involve more end users who don't have programming skills to test to get more feedbacks and hidden bugs for the front-end interface and usability, or maybe new features.
Lastly, once the application goes public, check error log frequently to catch more bugs that usually are hidden and buried in these error logs.
Is it easy to accomplish? Not really, because it is the way to go to assure the thing I am making is getting the better quality.
]]>So why doesn't borderwidth work? We all know that the DataGrid control will be rendered in <table> eventually when being called up in the client browser. It puts a property rules = "all" in <table> by default in the client page unless you say no to the engine by setting gridlines = "none" in DataGrid. So what does this rules do? According to W3C.org,
rules = none|groups|rows|cols|all [CI]
This attribute specifies which rules will appear between cells within a table. The rendering of rules is user agent dependent. Possible values:* none: No rules. This is the default value.
* groups: Rules will appear between row groups (see THEAD, TFOOT, and TBODY) and column groups (see COLGROUP and COL) only.
* rows: Rules will appear between rows only.
* cols: Rules will appear between columns only.
* all: Rules will appear between all rows and columns.
Aha, it explains why. Apparently, rules will not be used when combining with border style but it rules all in FireFox. Which one is more CSS-complaint then? Sorry, I didn't check.
ASP.Net 2.0 CSS Friendly Control Adapters might works better in server controls like DataGrid because it does help to create CSS friendly website that doesn't have any <table> in any rendered page in any client browser. However, I am not that keen to use it so far as it also seems to effects quite a lot existing styles in my web projects.
]]>"There are two kinds of people in the world: Those who have experienced catastrophic hard drive failure, and those who *will* experience catastrophic hard drive failure."
Someone quoted this in Jeff Atwood's What's your backup strategy, which is so true. Sooner or later, you will be facing the disaster caused by fragile hard drive. Knocking on the wood if you are trying to say you haven't. So if you don't have any backup plan yet, it's time to think about it very seriously. Even though you already have one in place, it's time to review to see if it's still effective. Or unless you are "lucky" like Raelyn Campbell who filed $54m lawsuit against Best Buy for losing laptop, you would be screwed if one day you so rely-on hard drive fails on you.
So what choices out there are available for us as personal use? Well, basically it's all based on what you need and how much data you want to be backed up. Some cost might be necessary needed in some cases.
First of all, buy an external hard drive, pick as much space as you can afford or pick the one like WD Passport that doesn't require power supply if you want to carry it around.

Then, configure your sync tool and either manually run it once a week or so or schedule it to be run regularly if possible. There are many sync choices out there but I am using and quite happy with Microsoft's SyncToy which is free, easy to use. It never failed on me. The con, though, is that it doesn't come with the schedule feature so I have to run it manually.
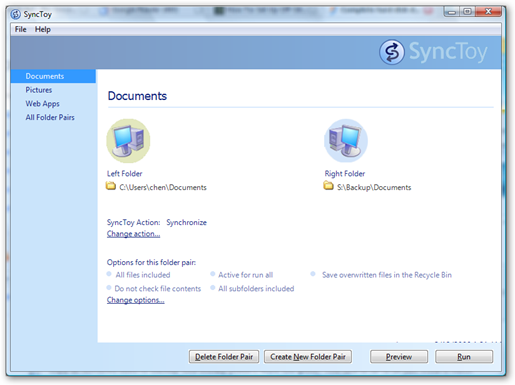
However, if you prefer to use tool that is more like backup, you might end up having to buy a commercial copy as Windows built-in backup tool usually doesn't work too good. The one in XP is ok but Vista is much worse. And I wasn't so lucky to find any good free ones either. Jeff's choice on Acronis True Image looks pretty good, which backs up the system to a bootable mirror image of the hard drive, that can be booted up later on when the primary one fails.
Going one step further, if you want to have a backup stored offsite, rather than at home, MozeHome is definitely the number one choice. It's free for under 2G data which should cover most of the cases, and it lightly runs on your computer and backs up your data without your attention once it's configured.
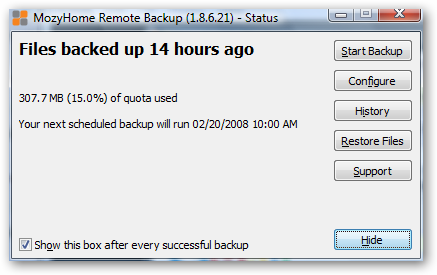
If you have more than 2G data, the chances are you might have a lot of photos included that you also want to back up. If that's the case, then you have to consider Flickr or SmugMug as your plan. Both are really popular photo gallery sites that offers so much rich features for photos but be prepared to pay to get the full services that you can store the full original size of your photos over there.
Right, we have yet covered Video. YouTube or sites that office the similar service seems to be the only choices at the moment. Getting your Videos backed up offsite will be a really time consuming job though.
Overall, MozeHome rules all, it's the best and easiest choice to the backup problem that everyone faces. Oh, how about emails? I will be covering it in my next post...haha...it's too late now.
]]>
1. Terminal Services RemoteApp applications appear no different than local applications, tightly integrated with the task bar and new Windows Vista features like 3-D flip. Terminal Services RemoteApp helps improve the end user experience and reduce training requirements.
2. Terminal Services Gateway provides a highly secure connection between internal applications and data to users outside the firewall. It delivers critical applications and data to mobile employees without additional VPN infrastructure.
3. Terminal Services Web Access helps simplify application deployment by making applications available from a web page or a SharePoint portal without installing them on the local PC. Speed application deployment by quickly connecting users with the applications they need.
4. Terminal Services Session Broker delivers session-based load-balancing to a Terminal Services Farm. Terminal Services Session Broker helps bring better uptime and performance to your Terminal Services environment.
5. Terminal Services Easy Print leverages the client-side print driver (no server side driver needed) to enable fast and reliable printing to a local or network-attached printer. End users can more productively work from remote locations.
Very good improvements for sure! Except the No. 1 which is still a significant improvement when mostly using it internally, the others are definitely dead important, in terms of both security and usability.
]]>As an Oscars night, having the following included in the post was so appropriate and fun.
It costs only $42.27 each, but unfortunately, it charges another $42.27 to ship it to Canada. Errr..


1. Double up on tasks that use different channels, i.e. writing a report while brainstorming designs for a new logo.
2. Think carefully about the requirements of each task, the actual processing needs may not be what you'd expect.
3. Juggle selectively. Minimize unnecessary distractions, when knowing that interruptions will be frequent, focus on routine tasks.
4. Interrupt tasks at natural breaking points whenever possible.
5. Set aside time when you will not do anything at all. Take breaks, eat well, exercise, and be sure to get enough sleep. IMO, this should be on the no. 1.
Sure, multitasking is often requested in almost all work places and is supposed to improve the productivity but it might make you less productivity in reality. So doing it right without losing your mind is something that we all need to focus on as well.
]]>]]>1. Mix two shades. The laws of interior design say you should never mix different shades of the same color - especially not green. Ignore them. Trimming a pastel with a darker tint says confident.
2. Think big. Don't pick small pieces for small spaces; that creates clutter. Instead, stretch the visual space with one or two large items. "Fewer gestures is a great idea, especially in bedrooms".
3. Show some wires. In a clean space, a few exposed wires just make the place look lived in.
4. Work the walls. For example, use strips of adhesive shelf paper on your kitchen walls and cabinets to make a motif that brings the space together.
5. Be crafty. For example, if you are stuck with fluorescents, sheath them in plastic tubing or try leaving half the tube exposed and alternating 6-inch strips of pink and orange over the other half. "It'll look like it's always 5 o'clock in your house."
So far, after doing some quick test, it seems faster than IE 7 but some of my websites don't display normally as they do in Firefox but I haven't dug that far to discover what caused it.
]]>The seminar overall is pretty good, especially the keynote in which three different presenters demonstrated some of the cool features from these three new releases. And both sessions I attended in the afternoon were good too. It talked about the new security features in Windows server 2008 and the virtualization things as well. It looks like there are a lot of new features and ways of doing stuff on the server side with these new releases, and badly it also means that I will have to spend more time to learn these things in order to keep the pace with the industry. :(
Alongside the good part, I was quite disappointed about the manager session that I attended right after the keynote. It was supposed to talk about something that brings the existing infrastructure to the next level but I just heard the voices from three different vendors talking about the stuff that I already knew. I was also quite disappointed the place they picked for the big event like this. Westin Bayshore is nice and it's right beside the beautiful Stanley Park in downtown Vancouver, but considering the convenience and how cozy the seats are, I missed the ones they had in Paramount Theater, in where at least I can enjoy the nap if the presentation is boring.
 And alongside the good and bad part, there are also some fun part. There are booths there where you can get nice light-blinking pens, T-shirts, and watch some the new products brought to you by various vendors. But the most fun part is this. I got a personal drawn portrait from Dell's booth where they have two young girls just sitting there and drawing portraits for anyone interested. Yes, that's the one, a "lofty" version of me. Do I look like a hero in big smile there, by the way? :) Nice work, Tiffany.
And alongside the good and bad part, there are also some fun part. There are booths there where you can get nice light-blinking pens, T-shirts, and watch some the new products brought to you by various vendors. But the most fun part is this. I got a personal drawn portrait from Dell's booth where they have two young girls just sitting there and drawing portraits for anyone interested. Yes, that's the one, a "lofty" version of me. Do I look like a hero in big smile there, by the way? :) Nice work, Tiffany.
And of course, the best part of this launch tour is the software Microsoft gave away. All attendances who filled up the feedback sheet got a package in a paper bag including Vista with SP1, Visual Studio 2008 standard, SQL server 2008 CTP, and Windows Server 2008 Enterprise edition (1 year evaluation). However, what happened to me after I got all these software was totally un-expected. I was just so excited about the copies I got, especially the Visual Studio one, that I can't wait to open the package when I was in the elevator down to the parking lot. The package with 3 DVDs in it was just slipped away from my finger when the door opened and it managed itself to go right through the slot to the darkness where I had no way to get them back. Sad, they didn't just want to stay with me. Both my friend and I just couldn't believe and stop laughing. What an end to the seminar like this!! Fortunately, my friend doesn't need Visual Studio and generously gave hers to me.
]]>----------------------------------------------
Fred Reckling
Microsoft 2008 Joint Launch Team
http://www.microsoft.com/2008jointlaunch/
]]>
I had blue screen happened on my Vista last night when I put my laptop on sleep. When I finally booted it up this morning and got to the desktop, I got this window telling me that "This problem was caused by Windows." Hmm...at least Windows or Vista doesn't lie.
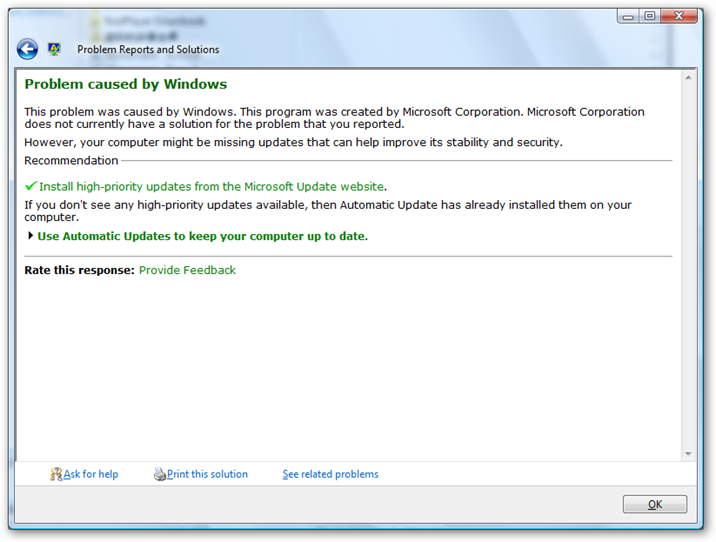
Screen shot #2:
For some reasons, my Firefox doesn't seem to like me recently. It freezes quite often and when it does it eats up my memory like crazy. Hey, come on, if you refuse to work, why can't you just quit?
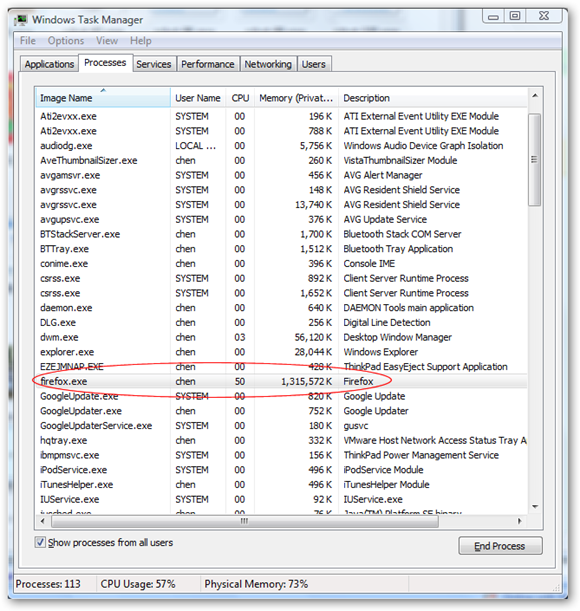
 Vista validates your network connection every time when the computer tries to connect to the network. If your router is not Vista-compatible and you are trying to connect via wireless, it most likely will not get identified the first place and won't be assigned a valid IP address as the result. In order to get work, you will need to go through the diagnose process to manually request for the IP address. Or, if you are tired of doing so, you can either look at your wireless router vendor's website to see if you are lucky to find the latest firmware that works for Vista, or end up buying a brand new one. Check to make sure it's Vista-compatible before pulling out your wallet.
Vista validates your network connection every time when the computer tries to connect to the network. If your router is not Vista-compatible and you are trying to connect via wireless, it most likely will not get identified the first place and won't be assigned a valid IP address as the result. In order to get work, you will need to go through the diagnose process to manually request for the IP address. Or, if you are tired of doing so, you can either look at your wireless router vendor's website to see if you are lucky to find the latest firmware that works for Vista, or end up buying a brand new one. Check to make sure it's Vista-compatible before pulling out your wallet.
For personal user, simply sign up another free email account on Gmail, or Yahoo, or whichever has the huge storage capacity, and set up the forwarding in the current email account to forward all incoming emails to the new signed email account. Make sure to still keep the copy in the current email inbox though. Most of public email service providers all provide this such feature, except hotmail. Hotmail, the first widely-adopted web email service, seems quite out-dated these days, even after a major upgrade to live mail. It lacks so much useful features comparing to its major competitors like GMail and Yahoo Mail. Basically, if you are still a user of hotmail, you are limited to yourself only use Outlook family to back up your emails because hotmail doesn't offer the forwarding feature to its users. Or it's time for hotmail users to switch over.
For corporate users, if you are an IT pro who manages your own corp email server it's time to implement an email archiving solution. With an easy-to-use reliable email archiving system in place, you can have a more efficient light-weighted running email server, implement email retention policy office-wide fairly easily, and educate end users how to organize emails more efficiently without worrying about losing any emails, etc. Besides, it's not an expensive solution anymore.
]]>
For those of you who are aware, Canada will soon (or already does) have an official Do-Not-Call registry, whereby you can register your phone number and telemarketers are not allowed to make unsolicited calls to you anymore. There's a catch with our version of the Do-Not-Call registry, and that's that many companies are exempt from it. Lots of telemarketing companies, charities, etc are all legally allowed to make cold-calls to you even if you register with the Do-Not-Call list, simply because they lobbied hard when the law was up for discussion.
Now we have a solution...
Dr. Michael Geist (yes, THE Michael Geist) has come up with a website (http://ioptout.ca) that allows you to sign up with your name, phone number, and email address and then lets you pick which companies to opt out from. When you're finished, you submit your info and the site generates an email for each company stating your info and the fact that you'd like to be removed from their cold-call list. This is the ultimate Do-Not-Call registry because companies that are exempt from the usual law are still required to remove you from their lists if you specifically ask. Now you don't even have to ask, the website does all the work.
I had my home phone number changed three years ago because of the spam calls. I wish and hope this would work out and finally stop these annoying, sometimes rude, calls. But meanwhile, I a bit doubt if it would. Remember the unsubscribe or remove me from the list link in the spam emails? Did it ever work if you went and asked to get your name off the list? It had welcome more spam if you did it. Will it happen the same if we provide our info to them and beg them for not calling? Always think twice every time when handing out your personal information.
]]>All of them are survived after day 1 which only allows remote pre-auth type attack. MacBook Air was the only one compromised on day 2 because of one vulnerability in Safari browser. Vista was defeated almost the last minute in the last day because of the hole in Adobe Flash. Sony VAIO with Ubuntu smiles in the end.
Not bad, all OS are very good in security. I thought Vista might be the first one being compromised but thank to IE7 team who did a good job to lock down the browser, which kept Vista alive for the first 2 days in the contest. The result should give more people the confident to use computer but also warned that human, not computer self, is the most thread to the computer system. It also sent message to all 3rd party software providers that be careful of designing your products or you will be next one to blame.
]]>Product Features:
- Video Game for Nintendo Wii Provides a Virtual Peeing Experience
- Amazing Realistic Pee Fluid Dynamics
- Imported from Japan
- Comes with game disc and Wiimote belt harness
- Includes cross regional boot disc to allow play on US Wii consoles
- Minimal Japanese text makes game easy to understand if you can't read Japanese
- Over 100 different peeing environments with multiple toilet and urinal styles
- Up to two players can compete with dueling pee streams
And this one, PTeq - USB Pregnancy Test, for sure will get you if the one above doesn't.

However, it becomes not so useful when HackerSafe, an online service that tells people the site with its seal on it is bullet safe, joins in. Because HackerSafe needs to scan your site and do a series of automated security tests every day, it sure generates tons of errors from the website. If the ELMAH logs the error in database, the errors HackerSafe generate eat database space like crazy. Worse, if your database has the quote assigned, it will be shutdown pretty quick and the website that rely on this database will be down the same time too. And more, if you set up to receive the notification when every error is generated, your email box soon will be full and stopped working pretty soon too. It's absolutely nightmare.
And yes, I just had been through this nightmare not so long ago. Because HackerSafe has more value to have on the site at the moment, I have to say good-bye to ELMAH for the time being until I figure it out a way to accommodate these two the same time.
]]>This Top 10 Worst Domain Names and 20 More Unfortunate Domain Names are absolutely a no-no. Take close look at these awful names so next time when we are doing brain storm for the new domain name make sure the name we pick doesn't follow their steps.
Manufacturer of instruments for monitoring temperature, humidity and pressure Dickson didn’t think twice when they choose: www.DicksOnWeb.com
A company selling CAD software and Learning CDs was called ViaGrafix - quite innocent until a blue pill hit the market. The company is now called Learn2 but was www.ViagraFix.com
The small town Winters’ local newspaper is called Winters Express and can be read online at: www.WinterSexExpress.com
An eBay competitor was considering the name Auctions Hit, but found it to be a shitty name: www.AuctionShit.com
And the worst of the worst is Experts Exchange, a knowledge base where programmers can exchange advice and views at www.ExpertSexChange.com. This site always comes in the no. 1 from Google but I never noticed they are actually expert on that.
]]>Dirty job No.7, Legacy systems archaeologist, is always part of my life and so far there is no sign I can get away of it. My assistant is doing the dirty job No. 6, Help desk zombie. Thanks to remote desktop, I am not fully classified as an On-site reboot specialist, the dirty job no. 5, but I am an off-site one most of the time. I am not so much an Interdepartmental peace negotiator, the dirty job no. 4, but am occasionally. And fortunately, that's all. So far, I don't need to worry about these other 3 dirty works, Enterprise espionage engineer, Datacenter migration specialist, and Sludge systems architect.
Oh, by the way, if you are a datacenter migration specialist, the dirty job no.2, you better look at and get one of these datacenter containers which sure will clean up your dirty job.

 Huge...this is my first reaction when I first saw it a few days ago. Yes, I missed the release day so I wasn't able to enroll in to the first 10,000 candidate to get the first hand experience. That's ok, because I have no experience of using Python either.
Huge...this is my first reaction when I first saw it a few days ago. Yes, I missed the release day so I wasn't able to enroll in to the first 10,000 candidate to get the first hand experience. That's ok, because I have no experience of using Python either. Hosting web apps in Google would really hurts those small web hosting companies or whoever doing this type of business. Who wants to run their critical websites on higher downtime percentage while there is a better one out there like Google? Google manages the uptime, backups, and more, it hosts your sites virtually across hundreds of servers so you don't need to care if one of them are down. How often do you see this offered by many other web hosting companies? You either have to share the resources with many others for lower cost or exclusively use one dedicated server but without back-up standby.
However, in order to gain all these benefits you will need to over a few gotchas, as Bex Huff pointed out.
- It only supports apps written in Python. No Java, no C, no .NET. Although, Python rocks...
- The best web application framework option is Django... which is an awesomely elegant framework, similar in philosophy to Ruby On Rails. Existing Django apps can be ported in minutes.
- You cannot write to the file system, you have to use the Google Datastore API
- If your web request takes more than a few seconds to respond, Google will kill the process, and send back an error... so I don't know how they do batch processes...
- Google owns your ass even more.
I am a .Net guy so it would be quite a bit of work to switch around. And first of first, I need to pick up Python if I want to go this direction. It's still in Preview Release right now and I am in the waiting list at the moment but will see how it goes later.
]]>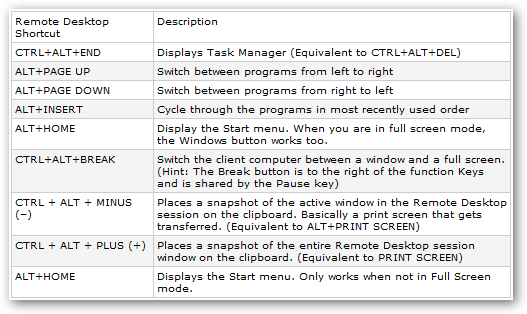
<system.net>
<mailSettings>
<smtp deliveryMethod="Network">
<network host="mailserver" port="25" defaultCredentials="true" />
</smtp>
</mailSettings>
</system.net>
Besides, you might also need to set up security authentication impersonate to true as well in web.config file in order to pass the proper authenticated credential to the mail server.
<authentication mode="Windows" />
<identity impersonate="true" />
<authorization>
<deny users="?" />
</authorization>
For people who don't know how to determine if the email address is set to only receive emails from authenticated users, if you are Microsoft Exchange user, you can easily find out from the following property window.
<update>
please see updated post for more updated information.
</update>
First, pick up one or two rock solid SNTP time server. Here is a list that you can look at.
Second, log in to the primary domain controller and synchronize the time server for the domain controller with an external source. In short,
w32time /monitor - to check what has been set up?
w32time /config /manualpeerlist: /syncfromflags:MANUAL - to configure.
w32time /update - to update the time services on the server.
w32time /resync - to re-synchronize with the external time server that was set up earlier.
All other computers in the domain then will get their time synchronized in a timely manner or after the reboot. Or, you can also set up the group policy in AD to force all computers to do so.
]]>The Internet Connectivity Evaluation Tool only can be run in IE, as expected. You will have to download and install a special ActiveX before actually running it. I ran and tested my home router to see if it can find out Why can't get my wireless identified in Vista? Unfortunately, it passed all the tests, which at least should have failed in one or two. However, Microsoft provides you a list of Vista-compatible routers you can find on the market after the test was done.
WirelessKeyView is a free tool from NirSoft, that reveals all the WEP/WPA keys stored on the computer and save them to text/html/xml file. It should be quite handy for people like me who often brings my laptop to various places.
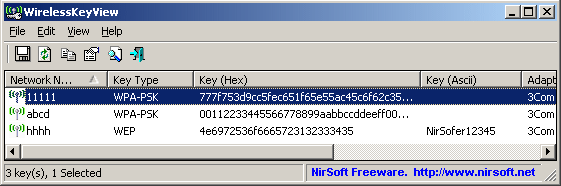
To recap what I need, I have a simple impersonate set to true web form that collects information and email them into a distribution group that receives email from Authenticated User Only in Exchange. It might be easy when impersonate is set to false because then you can simply set up the user info and get authenticated in Exchange when sending the email. I had it work without any problem in ASP.Net 1.1 but not so easy in 2.0.
It turned out the only way of doing so is:
1. hosting the form on the same server as Exchange,
2. set the deliveryMethod to "PickupDirectoryFromIis" in web.config file.
And then, the permission to do the PickupDirectoryFromIis started confusing me as I have no idea what permission should be granted. For now, I just put whoever needs to use the form to local administrator group, which appears working fine. But that can't be permanent, only temporarily.
Mission still has yet accomplished.
]]>Since ESX is based on Red Hat Linux, I had to run the diagnose tool right on the server and used WinSCP to download the result file to my laptop and uploaded it to their FTP server. While I was waiting for the news from VMware, I noticed that there were some warning messages popping up during the boot process telling me something about the BIOS, "machine type mismatched" more accurate. I thought it might be the reason causing the "purple screen", so I just went ahead and updated the BIOS for the server, and the server was running fine the rest of day without any further "purple screen". Next day, I got the answer from VMware that proved my thought as the log file I collected specifically pointed that there were hardware incompatible issue on the server.
It turns out, the purple screen shouldn't happen at all if the hardware are all compatible with ESX. Since the ESX server is heavily relied on the hardware layer, it would be good and healthy 1) make sure all hardware are compatible; 2) firmware for the hardware needs to be up-to-date.
Another lesson has to be learned and remembered.
]]> AVG released a new version of their flag-ship security products and will discontinue the current 7.5 version by end of May 2008. Starting next month, computer that still has 7.5 version installed will not get updated anymore including the virus definition. So it's vital to get this one upgraded. Fortunately, AVG still offers the free edition for private use only, though it isn't that obvious to find out on its website. Here is the shortcut.
AVG released a new version of their flag-ship security products and will discontinue the current 7.5 version by end of May 2008. Starting next month, computer that still has 7.5 version installed will not get updated anymore including the virus definition. So it's vital to get this one upgraded. Fortunately, AVG still offers the free edition for private use only, though it isn't that obvious to find out on its website. Here is the shortcut. http://free.grisoft.com/ww.download?prd=afe
One nice feature in this new version is LinkScanner that scans all links on search engine results page and indicates which links are good and which are dangerous. A very nice way to protect your computer. It works with all major search engine providers on both IE and Firefox.
And yes, of course, this feature eats your bandwidth quite a bit. So to disable if you want to, you can simply check off the option "Enable AVG Search-Shield" on Advanced AVG Settings under LinkScanner tab.
Time to say good-bye to my first iPod Mini, which I got as a gift 3 years ago. I got my new iPod Touch also as a gift almost a month ago, right before my trip to Shanghai, from one of our vendors though. That's why I don't get my name engraved in the back of the touch this time.
I had to say, it's awesome, has almost everything I wanted. I can surf the web, do the email, listen to the music, watch movies, look pictures, check maps, etc. etc. And now, after I unlock it I have a whole bunch 3rd party applications running on it too, like games, eBooks, view PDFs, etc.
The built-in apps on original Touch already covered most of the areas. If you are not comfortable with your touch being hacked, you still can enjoy a lot of the entertainment from it. But I highly recommend doing so because it simply opens another big door for you and allows you to have a lot more loaded on your toy. If I can't convince a people to buy an iTouch by just the embedded application, I certainly can with all the new cool 3rd party applications. Now, my apps icons are filled up almost two screens. I can hardly be getting bored anymore.
To unlock your iPhone or Touch, simply go to ZiPhone and download the ZiPhone application which unlocks your device and installs the installer package on it. The installer package has tons of applications included, from utilities to games, and from productivities to eBook. And the nice thing is, it checks and gets updated everyday so any new released applications arrives on your thing automatically.
Viewing web on Touch is also a very good. It works especially good, almost near perfect, for Google or any website that has the mobile version. It's just extremely comfortable reading my feeds on Google Reader, checking my email on Gmail, and even viewing the documents or spreadsheet on Google Docs.
iTouch perfectly fits almost all my needs and I don't see the needs to upgrade it to iPhone near in the future. Yes, I can't make the call, I can't be online at all time, I can't text messaging, but all these come with the price. The only thing I miss from iPhone is probably the camera.
]]> I recently purchased an APC Environment Management Unit due to the temperature issue I am having in our server room. The device looks awesome but I was having the problem finding its IP address. It was mentioned on the quick installation guide that it uses DHCP to get the IP address automatically if there is an available DHCP server on the network but I saw no records related to this new device on the DHCP server assigned addresses pool at all. I was stuck because I only know its MAC address and there is no way for me to find it out without a proper tool handy.
I recently purchased an APC Environment Management Unit due to the temperature issue I am having in our server room. The device looks awesome but I was having the problem finding its IP address. It was mentioned on the quick installation guide that it uses DHCP to get the IP address automatically if there is an available DHCP server on the network but I saw no records related to this new device on the DHCP server assigned addresses pool at all. I was stuck because I only know its MAC address and there is no way for me to find it out without a proper tool handy.
Then my assistant came over and mentioned a shareware tool called CC Get Mac Address which is designed to find MAC address and computer name from IP address. So I downloaded and installed on my Vista. And did a quick scan and magically found out the IP address associated with the MAC address that matches the APC unit. Hula...it turned out that the APC unit has its default IP address 192.168.0.100 assigned by manufactory. And this IP address falls into my DHCP IP address pool.
I believe there are probably a lot tools like this CC Get Mac Address out there on Internet and some of them even comes free. So it would be handy to at least know where to look when situation like this happens.
]]> The new released firmware Version 2.0 offers so much good features that finally lured me enough to go ahead and give it a try, which is where the hassle started.
The new released firmware Version 2.0 offers so much good features that finally lured me enough to go ahead and give it a try, which is where the hassle started.
Apple offers the new firmware 2.0 for free for all iPhone users but charges $9.99 for iPod Touch owners which pissed off most of the owners including myself. I didn't have the intention to do so to get my Touch upgraded so I followed iPod Touch 2.0 Upgrade Download Link and downloaded the restore pack. Once I have the file ready, I fired up iTune, connected my Touch, held down the Shift key and clicked the Update button. So far so good, I got the window pop up asking me where the update pack located. I selected the file and the upgrade progress started, but it failed in the end with the error code "1603". I then ran through a couple of cycles that restored the iPod to 1.1.4 and tried to upgrade again, and still without any luck. I thought maybe Apple did something in their end that eventually prevented owners from upgrading without paying them. So I decided not to waste any time and went and paid the $10 to Apple, wished I can have this installed. And not surprisingly, it still came no luck. I felt I was stupid and wasted my $10.
It turned out I was stupid. There are solutions to this error code, one suggesting recharging the device directly by the charger for 10+ hours, and other suggesting reinstall iTune. But I took the solution suggesting giving a try on another computer. So I tried on my another computer that never had iTune installed. And yes, everything runs perfectly. I finally got my iPod Touch up running in version 2.0.
I am still in the process of resnyc but so far so good. I guess I had to pay Apple something because simply I didn't pay for my Touch.
And for any iPod Touch owners who want to give a try on version 2.0, you can simply download the package either from the link above or better, here. You don't have to pay to get it.
]]>So I downloaded a System Arial font for Windows which fixed the problem perfectly after I manually installed it back into Windows Fonts fold.
It's still interesting though what exactly Firefox 3 did to make it happen and I am also surprised that there were number of people having the same issue.
]]>This fixed my firefox problem.]]>
All the best.]]>
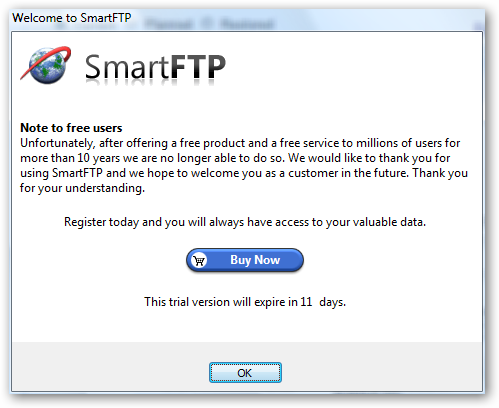
Well, after being "cute" (CuteFTP) , and "smart" (SmartFTP) for many years, it's time to move on to something neither "cute" nor "smart". It turns out, being "zilla" (FileZilla) is not bad at all. After all, life is not just being Cute or Smart. :)
]]> The blackout that happened in Vancouver downtown on Monday morning July 14 lasted 3 days to have everything back in order. Unfortunately, our office is among those who had no power for more than two days. It's totally a disaster. Imagining how damage could be to a business like us that heavily depends on the deadlines. We are fortunate that we got over it by renting two 3000w Honda Gas Generator, having them sitting on the patio providing the enough juice to our servers for one and half days. We are lucky because 1) we have a patio that leads to the open air close to our server room so we can have this giant machine sitting there and running in the open air; 2) the blackout didn't interrupt the telephone line so we still have our ADSL on, or there would be no point to have the generator powering on all the servers.
The blackout that happened in Vancouver downtown on Monday morning July 14 lasted 3 days to have everything back in order. Unfortunately, our office is among those who had no power for more than two days. It's totally a disaster. Imagining how damage could be to a business like us that heavily depends on the deadlines. We are fortunate that we got over it by renting two 3000w Honda Gas Generator, having them sitting on the patio providing the enough juice to our servers for one and half days. We are lucky because 1) we have a patio that leads to the open air close to our server room so we can have this giant machine sitting there and running in the open air; 2) the blackout didn't interrupt the telephone line so we still have our ADSL on, or there would be no point to have the generator powering on all the servers. Looking at the bright side though, we learned and saw what the disaster or emergency situation looks like when it happens. It's such a valuable experience that we need to benefit from it, do more planning, so to be ready or at least not being panic when next one comes, even though it most likely will be something different.
The crisis is over, but the business contingency plan just begins.
]]> This lifehacker's definitive comparison did a pretty good job comparing the most two popular email tools, in a business aspect. The conclusion that Gmail wins though shouldn't be the key point when choosing the email platform.
This lifehacker's definitive comparison did a pretty good job comparing the most two popular email tools, in a business aspect. The conclusion that Gmail wins though shouldn't be the key point when choosing the email platform. My point, simply is, for a company with less than 20 users go for a Gmail solution. For any company with more than that, going with Outlook with Exchange is a no brain.
Home user? Always go for Gmail. Or if you really like Outlook, use it with Gmail IMAP configured.
]]> Finally, I tried and finalized to use telligent's new released Graffiti cms system as my IT document library. Its simplicity and flexibility totally meets almost all my needs. I can easily customize the layout and move content to or from wherever I want. It also works seamlessly with my favorite blogging publish tool, Windows Live Writer. Whenever I want to document something, I can simply fire up my live writer, write something down, pick up which category should belong to, and publish it right after I finish it. Yes, comparing to Wiki, it lacks of the version tracking but this is not what I am concerned the most. However, if the revision control weights pretty well in your list, you should be considering Wiki instead.
Finally, I tried and finalized to use telligent's new released Graffiti cms system as my IT document library. Its simplicity and flexibility totally meets almost all my needs. I can easily customize the layout and move content to or from wherever I want. It also works seamlessly with my favorite blogging publish tool, Windows Live Writer. Whenever I want to document something, I can simply fire up my live writer, write something down, pick up which category should belong to, and publish it right after I finish it. Yes, comparing to Wiki, it lacks of the version tracking but this is not what I am concerned the most. However, if the revision control weights pretty well in your list, you should be considering Wiki instead.
]]>Features in GFI MailArchiver 6 BETA 1 build 20080717:
- NEW: Microsoft Outlook Connector – Users can view archived email from Microsoft Outlook.
- NEW: During installation, the setup will ask to customise the language analyser to be used during email indexing.
- NEW: Download archive emails in Microsoft Outlook format (.msg)
- NEW: Users can access archived emails from web UI folder structure.
- NEW: Indexing processes can be paused and resumed at will.

 Time for the 2008 Beijing Summer Olympics. The opening ceremony will start tomorrow morning but some of the games has already started, like man and woman soccer. The team man China tied the game with New Zealand, the weakest team in the same group. However, they scored the first goal ever in team China's soccer history. So I really wanted to see how they did it. But unfortunately, even with the Wired's Watch the Olympics Online, I wasn't able to watch it. After trying for over 1 hour, I gave up.
Time for the 2008 Beijing Summer Olympics. The opening ceremony will start tomorrow morning but some of the games has already started, like man and woman soccer. The team man China tied the game with New Zealand, the weakest team in the same group. However, they scored the first goal ever in team China's soccer history. So I really wanted to see how they did it. But unfortunately, even with the Wired's Watch the Olympics Online, I wasn't able to watch it. After trying for over 1 hour, I gave up. Apparently, every country only has one major television company granted for distribute the news for Olympics. I used to just watch all sports games on Sina Sports. But due to the agreement signed with Olympics' committee, it only opens to local users, not the users overseas like me. NBC is awesome too. It has tons of Videos on the site free to watch but again, only restricted to US residents. CBC is the one for Canadian, but sadly, I couldn't locate a piece of Video on the site for me to watch. Really sucks. All they have are the stuff that I can easily read or find from other places. Too bad, I never missed a free fast Proxy service that much, and the first time ever I even want to be in the states.
Hopefully, as the games start, everything will be turning better and better on CBC.
<update>
Another thing CBC didn't do it right and on time is the lack of mobile version on their website for the mobiles while NBC has one that fits my iPhone smoothly.
</update>
lol took me long enough to find this out
I can't believe that you had this since 2004 wow
oh and yes i totally agree about the CBC Olympics
you know what just get this thing called TV Ant
you can watch all the Olympic games you want if you have really good quality internet connection speed.
]]>
]]>ididwork is an online tool that allows employees to keep track of the work they do over time. Employee logs can then be shared with other employees, and submitted to superiors for review. ididwork can be used by an individual to keep track of work completed, and by the enterprise to increase awareness of employee activity.
Anyway, enjoy the rest of the Olympic weekend. Can't wait to watch the basketball game tomorrow morning. Yes, Yao Min versus US.
]]>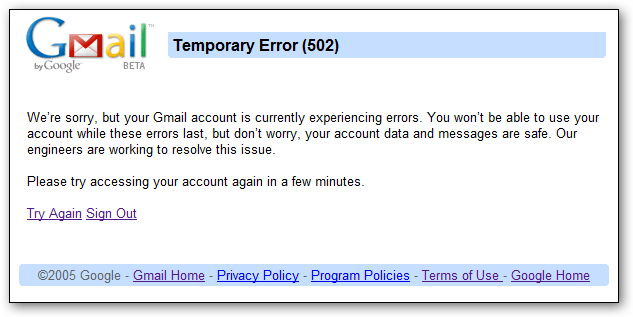
It was down for more than an hours and all my Gmail accounts including the Google App one were all inaccessible during the time. It wasn't a big deal for me but I am deadly sure it matters for a lot of others. I can't just believe it happened on Gmail, a solid-stable system that never failed on me.
Just don't know if we should ever trust the cloud computing. Is moving all data online especially your business critical data still a really good approach?
]]>One nice thing about the new iPhone 3G and iPhone 2.0 software is the native support for Microsoft Exchange because Apple finally licensed Microsoft ActiveSync from Microsoft. It delivers pushing email, calendar, and contacts. The first thing I tried after I had my iPhone 3G is to try to connect it to the office Exchange server but no success. It passed the authentication part but sync'd null after.
I left there for a week or two until my assistant Lee passed around this Microsoft KB which obviously related to the issue we were having. I didn't follow all of them but changed some obvious ones and all of sudden it started working, email flows in while events shows in my calendar on iPhone. Here is things I thought is necessary to get it work.
- Port 80 and 443 need to be opened on firewall.
- The site that has OWA and OMA has to have both 80 and 443 opened.
- OWA (domain/exchange) has to be put on SSL as required to secure the communication.
- Follow the Microsoft KB 817379 to make an alternative exchange-oma for Microsoft ActiveSync Server with SSL not required.
And last, if the Exchange email account you created on iPhone isn't working, you have to delete it and recreate it as new to test. I still have the following error message showing up on Exchange server event log but it doesn't seem to matter anymore as emails still flow.
Unexpected Exchange mailbox Server error: Server: [xxx] User: [xxx] HTTP status code: [400]. Verify that the Exchange mailbox Server is working correctly.
Exchange server 2007 offers a better tools and ways to manage mobile users and devices but not so many on 2003. So next step, I will have to find a way how to secure the system tightly.
]]> I was shocked, astonished, and a little disappointed when I heard the news that Liu Xiang has quitted the 110-m hurdle game in Bei Jing Olympics. But he's still the man and he's still a hero that looks even more like a human than before. It required more courage deciding to quit than continuing in the situation like this and even more, Liu has been dreaming of winning a gold medal in the national stadium in the Olympics for 7 years.
I was shocked, astonished, and a little disappointed when I heard the news that Liu Xiang has quitted the 110-m hurdle game in Bei Jing Olympics. But he's still the man and he's still a hero that looks even more like a human than before. It required more courage deciding to quit than continuing in the situation like this and even more, Liu has been dreaming of winning a gold medal in the national stadium in the Olympics for 7 years. Some of the people said that he could walk to the end, and yes, I agree, I would do the same if I were him. But hell no, that's why we can't be at his level and we can't never be at the top. The warrior can not be beaten in the battle field, and Liu is definitely a warrior who is never afraid of battling. His quit is telling all his opponents that he hasn't be beaten in the Olympics and he will come back.
Stand up, China Liu, you are always the hero to us...no matter what!
]]>- Gmail Notifier - A notifier for Gmail accounts. That's the one I used every day to manage three my Gmail accounts.
- Google Toolbar for Firefox. I have no idea why there are still people who doesn't want it on their browser.
- IE Tab - enables you to use the embedded IE engine within Firefox.
- Web Developer - nonetheless to say, it's a must have being a web developer.
- Remember the Milk for Gmail - it's sweet having task manager right in the Gmail.
What's yours then?
]]> A lot of eBayer are furious about the new eBay's feedback system that took place a few months back. I am ok with most of the changes but couldn't stand the fact that neutral feedbacks were counted just the same as the negative ones and I had no idea why they are doing this way.
A lot of eBayer are furious about the new eBay's feedback system that took place a few months back. I am ok with most of the changes but couldn't stand the fact that neutral feedbacks were counted just the same as the negative ones and I had no idea why they are doing this way. Gladly, eBay finally realized it and changed the formula probably just a few hours ago. Now, I have 100% positive feedbacks, which tells all potential customers that I am a very honest, trustful seller who treats customer's satisfaction very seriously.
]]> MochaSoft, the provider of VNC app on iPhone, released the Remote Desktop app for iPhone, a long waiting iPhone app for me since the first day I had my iPod Touch. As always, the lite version is free. According to the description of the app:
MochaSoft, the provider of VNC app on iPhone, released the Remote Desktop app for iPhone, a long waiting iPhone app for me since the first day I had my iPod Touch. As always, the lite version is free. According to the description of the app:
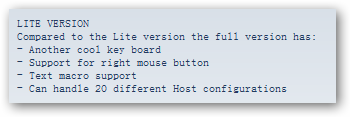
None of these features I need on my iPhone, so the free lite version fits me perfectly. Besides, I am using it only in emergency. RDP on a 3.5" screen isn't actually very enjoyable. The limitations say it only support for Windows XP pro but I have no problem RDP in Windows 2003 server.
Now, with a paid app NetShare from nullriver through which you can get your laptop on Internet by tethering you iPhone's 3G network while you are on the road, every piece of application I had been dreaming for on a mobile device are there. Dream finally comes true...well wait, NetShare has been took off the Apple Store again at the moment.
By the way, MochaSoft's other little app Telnet Lite should be added too.
<update date=”Nov 3, 2008”>
The RDP app was pulled from the Apple App Store for some reason and was just put back on again. Hurry up to get it installed on your iPhone and back it up on your desktop in case it gets disappeared again.
</update>
I have already been on half of them, specially AVG for protecting my computer, Mozy for backing up my data, and Google Docs, alternative to Zoho, for documenting. Right now, I am loading reQall over on my iPhone, and will be remembering Gparted next time when I need to repartition my hard drive.
]]> Another big day in web browser history, the day Google finally announced the release of their long waiting and already forgot web browser, Chrome, shortly after they renewed their sponsorship to Firefox for another 3 years. I couldn't wait for a second once I heard the release, rushed to their website and had it running on my Vista one minute later. The first impression, blazing fast; the second, deadly simple; the third, just amazing. To be honest, never had the same feeling when firstly touching the IE.
Another big day in web browser history, the day Google finally announced the release of their long waiting and already forgot web browser, Chrome, shortly after they renewed their sponsorship to Firefox for another 3 years. I couldn't wait for a second once I heard the release, rushed to their website and had it running on my Vista one minute later. The first impression, blazing fast; the second, deadly simple; the third, just amazing. To be honest, never had the same feeling when firstly touching the IE.
What's good? Google's legendary simplicity, and the renovated home page layout. The Chromer team even thought about completely getting rid of the bookmarks but I am glad they didn't.
What's cool? The performance. It's fast, deadly fast. Thanks to the awesome Webkit, the fastest rendering engine that powers Apple's Safari. And their own developed JavaScript Virture Machine that really speeds up most of JScript-rich web 2.0 websites.
Speed may be Chrome's most significant advance. When you improve things by an order of magnitude, you haven't made something better — you've made something new. "As soon as developers get the taste for this kind of speed, they'll start doing more amazing new Web applications and be more creative in doing them," Bak says. Google hopes to kick-start a new generation of Web-based applications that will truly make Microsoft's worst nightmare a reality: The browser will become the equivalent of an operating system.
What's best? The multiprocess architecture that allowed each opened tab run as a separate program. One tab crash won't affect other opened tabs, a huge benefit against all other current browsers in the market, which is also the reason that makes drag the tab to a new Window thing in real. Thanks to their acquisition of Green Border Technologies, a software security firm that developed the "sandboxes" for Chrome.
What's the killer? Open source. The source code will be released to public shortly after the release.
But all of these nice killer feature would make me to a switch, not really, at least not now. Why? Because I am so Firefoxed, can't leave without the add-on extensions. That's the fundamental different between these two browsers. The add-on extensions used to be the most innovated feature in Firefox, but not any more in Chromers' eyes, who can't stand on the fact that any innovation made in browser will be broken without all the updates to the extensions.
]]>The conclusion was obvious: Only by building its own software could Google bring the browser into the cloud age and potentially trigger a spiral of innovation not seen since Microsoft and Netscape one-upped each other almost monthly.
]]>
 There was a discussion today on the forum I participate regarding the spam whitelisting. The forum is specifically aimed in legal industry so we are all talking about how the technology works in the legal field. The question was whether or not whitelisting the client email address, quite common one but I was surprised about some of the answers that mentioned lawyers are responsible for their own emails, meaning that they should spend their time going through the quarantine to find their own false positive. And the more reality that shocked me even more is that this is quite common in many of the firms.
There was a discussion today on the forum I participate regarding the spam whitelisting. The forum is specifically aimed in legal industry so we are all talking about how the technology works in the legal field. The question was whether or not whitelisting the client email address, quite common one but I was surprised about some of the answers that mentioned lawyers are responsible for their own emails, meaning that they should spend their time going through the quarantine to find their own false positive. And the more reality that shocked me even more is that this is quite common in many of the firms. I just don't get it. Isn't lawyer's time worth more spent on something that generates more revenue? Asking lawyers to go through their own quarantine is just like receiving emails without anti-spam protection at all. Yes, the job going through the spam is probably one of the dirtiest job in the world but that doesn't mean no one is willing to do so. We have one in our office, part of whose job is going through the nasty spams. She averagely checks 4000-5000 spams a day and does a wonderful job catching the false positives. I just can't imagine how many time she had saved for lawyers just by doing this.
IMHO, whoever said or suggested the idea that lawyers should check their own spams needs to learn a bit of more business lessons.
]]>But I worn you that having all of them on your computer would not help. Windows just can’t handle that many cleaners the same time. :)
]]>NetShare, banned from the AppStore
Looks like Apple has decided they will not be allowing any tethering applications in the AppStore. As such, NetShare will not be available in the iTunes AppStore. We are seeing a lot of similar reports from various developers who's applications were abruptly removed and banned from the AppStore without any violations of the terms of service. This is all unfortunate news for the iPhone platform end-users.
So what’s next? Go for the JailBreak?
]]> Why the heck did I want to spend my $3.99 on this? Simply because,
Why the heck did I want to spend my $3.99 on this? Simply because,
1. I love music.
2. I like guitar.
3. I wish I can play guitar.
4. I wish I can sing while I play guitar.
5. I wish I can play Hotel California, which is called Motel California in the app, like Eagles.
6. Many other more wishes…
It’s overall a deadly easy-to-use app and fun to play but I need to find the charts for the songs to play with. It’s going to choke a quite bit of my time on it…but that’s iPhone.
Check it out, http://www.frontierdesign.com/Guitar/
]]>ps. the MS essay 10 law entry I think you missed entered the laws twice :)]]>
Law #1: If a bad guy can persuade you to run his program on your computer, it's not your computer anymore
Law #2: If a bad guy can alter the operating system on your computer, it's not your computer anymore Law #2: If a bad guy can alter the operating system on your computer, it's not your computer anymore
Law #3: If a bad guy has unrestricted physical access to your computer, it's not your computer anymore Law #3: If a bad guy has unrestricted physical access to your computer, it's not your computer anymore
Law #4: If you allow a bad guy to upload programs to your website, it's not your website any more Law #4: If you allow a bad guy to upload programs to your website, it's not your website any more
Law #5: Weak passwords trump strong security Law #5: Weak passwords trump strong security
Law #6: A computer is only as secure as the administrator is trustworthy Law #6: A computer is only as secure as the administrator is trustworthy
Law #7: Encrypted data is only as secure as the decryption key Law #7: Encrypted data is only as secure as the decryption key
Law #8: An out of date virus scanner is only marginally better than no virus scanner at all Law #8: An out of date virus scanner is only marginally better than no virus scanner at all
Law #9: Absolute anonymity isn't practical, in real life or on the Web Law #9: Absolute anonymity isn't practical, in real life or on the Web
Law #10: Technology is not a panacea
Check the full essay here: http://technet.microsoft.com/en-us/magazine/cc895640.aspx
]]>Tools that require to finish the work:
- At least 1G USB flash drive
- Virtual CD mounting tool, i.e. Daemont Tools
- WinImage to build the image to USB storage.
Steps to make the bootable ESX Server 3i USB flash drive:
- Download ESX Server 3i Installable ISO
- Extract INSTALL.TGZ from the root directory of the ISO image using the Virtual CD mounting tool.
- Extract /usr/lib/vmware/installer/VMware-VMvisor-big-3.5.0-xxxxx.i386.dd.bz2 from INSTALL.TGZ
- Extract VMware-VMvisor-big-3.5.0-xxxxx.i386.dd from VMware-VMvisor-big-3.5.0-xxxxx.i386.dd.bz2
- Attach the USB flash drive and make sure you no longer need the data on it
- Use WinImage to transfer VMware-VMvisor-big-3.5.0-xxxxx.i386.dd to the USB flash drive
- Disk->Restore Virtual Hard Disk image on physical drive…
- Select the USB flash drive (Warning: If you select the wrong disk you will lose data!)
- Select the image file VMware-VMvisor-big-3.5.0-xxxxx.i386.dd
- Confirm the warning message
- Wait for the transfer to complete
- Unplug the USB flash drive (Warning: If you forget to unplug the flash drive from the PC you might lose the data on your hard drives the next time you boot!)
- Attach the USB flash drive to the machine you want to boot (Warning: If ESX Server 3i recognizes local drives, you might lose the data on it, so make sure you don´t need it anymore or unplug all hard drives!)
- Turn the machine on and make sure the USB flash drive is selected as boot device
- Enjoy.
Notes:
I failed to so on my Vista machine but had no problem on XP. And the machine you want to boot from must have the option to make the USB flash drive as the boot device.
You can also watch the video to see how to do it in action.
]]>Sarah
http://laptopseries.net
]]>
 People in Remember the milk finally made a step forward to give this awesome online service more accessible through over the mobile, iPhone in specific. However, you will have to pay $25/year to be able to use it. The app is free but the service isn’t.
People in Remember the milk finally made a step forward to give this awesome online service more accessible through over the mobile, iPhone in specific. However, you will have to pay $25/year to be able to use it. The app is free but the service isn’t.
Remember The Milk [iTunes App Store via RTM Blog]
]]>1. Standardize on desktops and cell phones to reduce support differences.
2. Perform off-site backups.
3. Use hardware to secure the internet connection.
4. Use a VPN. 5. Run personal firewalls, especially on Windows PCs.
6. Rely on VoIP PBX for the phone system.
7. Have a solid test plan for adding new technology.
Interesting, there are a few online applications available online providing such services, such as Openvpn.org and Hamachi, will check it out.
]]>http://www.backupreview.info/2008/01/11/mozy/]]>
DSBL is GONE and highly unlikely to return. Please remove it from your mail server configuration.
DSBL was a blocklist specialized in listing open relays and open proxies. To put it simply, DSBL listed IP addresses of computers that could be tricked into sending spam by anybody. This was a very successful strategy. Nowadays open relays and open proxies are rare, spammers hardly ever use them any more and no software seems to come with an open-by-default policy any more.
Hardly believe that it’s now gone after utilizing it for years but I guess they were right about the fact that the spammers now totally beat this old trick, even though it still helps to block a few every day.
]]>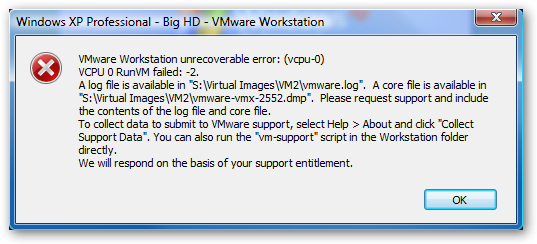
Yesterday morning, I noticed that the first error message popped up right after I fired up Microsoft Virtual PC while I still had a VMware virtual machine running, which told me that it was actually Virtual PC that kept VMware down. I then looked up both settings and tried various combinations to get both alone with each other. And finally, the only way that makes Virtual PC and VMware to run simultaneously is to disable the “hardware virtualization” on Virtual PC and allow VMware to take the hardware resources.
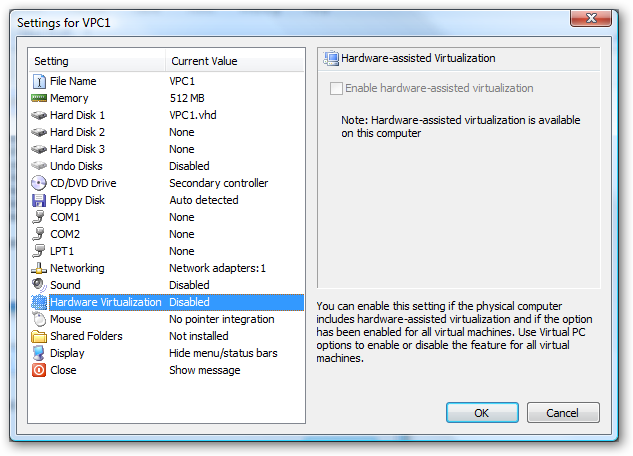
I goggled many times re this issue but came up almost nothing, so I hope this will help you if you are running into the same mystery. By the way, I am running both on Lenovo T60 laptop with 4G RAM installed, and on Vista. Both run perfectly.
]]>Much appreciated.]]>
Not very good, I was actually off the track quite often. It looks like I am wasting my time on too much thinking and am putting too little to action. Seriously, I need to make changes, changes that will make me to focus more on doing things that are more profitable.
More thinks will follow when they come…
]]>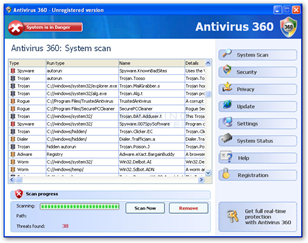 I had one colleague whose computer unfortunately got caught by this malware recently. It looks legitimate enough to foul people to have it installed and scanned your computer. But in fact,
I had one colleague whose computer unfortunately got caught by this malware recently. It looks legitimate enough to foul people to have it installed and scanned your computer. But in fact, Antivirus 360 is a rogue anti-spyware program that uses false scan results and aggressive advertising in order to promote itself. This rogue is advertised by the Vundo Trojan and is replacing the Antivirus 2009 rogue program that Vundo has been aggressively advertising. If you are infected with the Vundo Trojan you will see a large amount of pop-ups stating that your computer is infected and that you should install Antivirus 360 in order to protect yourself. If you click on the ad, Antivirus 360 will be downloaded to your computer and you will be prompted to install it.
I found this uninstall instructions online which describes in detail what it does and how to remove it. I followed the instruction and tried to use the recommended tool, malwarebyte's anti-malware, to clean it up but didn’t work out. Fortunately, the instruction has the enough information about this malware so that I could do a manual clean up to remove it completely out of the computer.
1. Kill AV360.exe from Task Manager.
2. Remove all associated Antivirus 360 files from the following location:
c:\Program Files\A360
c:\Program Files\A360\av360.exe
%UserProfile%\Application Data\Microsoft\Internet Explorer\Quick Launch\Antivirus 360.lnk
%UserProfile%\Desktop\Antivirus 360.lnk
%UserProfile%\Start Menu\Antivirus 360
%UserProfile%\Start Menu\Antivirus 360\Antivirus 360.lnk
%UserProfile%\Start Menu\Antivirus 360\Help.lnk
%UserProfile%\Start Menu\Antivirus 360\Registration.lnk
3. Remove the Windows Registry created by AntiVirus 360:
Note that the numbers in these registry keys are random:
HKEY_CURRENT_USER\Software\13376694984709702142491016734454
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "13376694984709702142491016734454"
4. Reboot and you shouldn’t see this program popping up on your desktop after.
Hopefully, it helps.
]]>A Japanese company (Toyota) and an American company (Ford Motors) decided to have a canoe race on the Missouri River. Both teams practised long and hard to reach their peak performance before the race.
On the big day, the Japanese won by a mile.
The Americans, very discouraged and depressed, decided to investigate the reason for the crushing defeat. A management team made up of senior management was formed to investigate and recommend appropriate action.
Their conclusion was the Japanese had 8 people rowing and 1 person steering, while the American team had 7 people steering and 2 people rowing.
Feeling a deeper study was in order; American management hired a consulting company and paid them a large amount of money for a second opinion.
They advised, of course, that too many people were steering the boat, while not enough people were rowing.
Not sure of how to utilize that information, but wanting to prevent another loss to the Japanese, the rowing team's management structure was totally reorganized to 4 steering supervisors, 2 area steering superintendents, and 1 assistant superintendent steering manager.
They also implemented a new performance system that would give the 2 people rowing the boat greater incentive to work harder. It was called the 'Rowing Team Quality First Program,' with meetings, dinners and free pens for the rowers. There was discussion of getting new paddles, canoes and other equipment, extra vacation days for practices and bonuses. The pension program was trimmed to 'equal the competition' and some of the resultant savings were channelled into morale boosting programs and teamwork posters.
The next year the Japanese won by two miles.
Humiliated, the American management laid off one rower, halted development of a new canoe, sold all the paddles, and cancelled all capital investments for new equipment. The money saved was distributed to the Senior Executives as bonuses.
The next year, try as he might, the lone designated rower was unable to even finish the race (having no paddles), so he was laid off for unacceptable performance, all canoe equipment was sold and the next year's racing team was out-sourced to India.
Sadly, the End.
Here's something else to think about: Ford has spent the last thirty years moving all its factories out of the US , claiming they can't make money paying American wages.
TOYOTA has spent the last thirty years building more than a dozen plants inside the US The last quarter's results:
TOYOTA makes 4 billion in profits while Ford racked up 9 billion in losses.
Ford folks are still scratching their heads, and collecting bonuses ...
IF THIS WEREN'T SO TRUE IT MIGHT BE FUNNY.
I thought the bureaucratic is a serious problem in China, a still developing country, but didn’t know it actually happens and may be even worse in a developed country like US. Maybe that’s another reason to the economic collapse happening globally right now.
 Image from CartoonStock.com
Image from CartoonStock.com
#1 – Tasks
 This nature built-in to-do list right in the Gmail self completes the last piece it was missing from the beginning. With new Tasks available in my Gmail and Zenbe List app over on my iPhone, I am retiring Remember the Mike almost completely.
This nature built-in to-do list right in the Gmail self completes the last piece it was missing from the beginning. With new Tasks available in my Gmail and Zenbe List app over on my iPhone, I am retiring Remember the Mike almost completely.
#2 – Create a Document
 This new added feature put Gmail and Google Docs all together and work so seamlessly. Now if I want to save an email as a word document in my Google docs account I don’t have to go through the multiple steps to do so. All I need is just clicking the create a document link right next to the email self, and it opens up in Google Docs in word format right away. Awesome.
This new added feature put Gmail and Google Docs all together and work so seamlessly. Now if I want to save an email as a word document in my Google docs account I don’t have to go through the multiple steps to do so. All I need is just clicking the create a document link right next to the email self, and it opens up in Google Docs in word format right away. Awesome.
#3 – Signature tweaks
 Have scratched my head hardly and can’t figure out why the “—“ line always appears before the signature block I put in Gmail settings. Now, this tweak fixed this and makes my signature, see the one at the left, much better and consistent look in every email I send.
Have scratched my head hardly and can’t figure out why the “—“ line always appears before the signature block I put in Gmail settings. Now, this tweak fixed this and makes my signature, see the one at the left, much better and consistent look in every email I send.
I don’t really make a lot of resolutions for the new year for myself but I am really looking forward to it as I do have a lot projects and ideas that needs to be put in action rather than staying in my mind and waiting. Hopefully, by the end of year 2009 I will be happy with my effort and out through the year and won’t make any excuses about not doing so.
Happy New Year to all of you who by any chance come and visit my little cyber home.
]]> Finally, I squeezed out a couple of hours over the weekend to re-design this blog’s layout to give its a new face that looks more 2.0, and hope to bring me the good luck in the new year too. It’s been on my to-do list for very long time and eventually I had it crossed off. Another mission accomplished so I can move on to the next project.
Finally, I squeezed out a couple of hours over the weekend to re-design this blog’s layout to give its a new face that looks more 2.0, and hope to bring me the good luck in the new year too. It’s been on my to-do list for very long time and eventually I had it crossed off. Another mission accomplished so I can move on to the next project. As you can see, there are quite few changes as the the result but in reality, I am still using the same CSS style sheet with a few changes in templates and color theme. I am running this blog on subText engine, one of the few blog engines from the old days. It’s not as modern and fancy as the most popular engines currently in the market, but since it still works for me I have no intension changing it at this point…I didn’t even bother upgrading it since I upgraded it form its predecessor .Text in June 2007. However, if I have another need to create a new blog type of website, I would be choosing the most popular WordPress instead, which will be much easier to set up and will have a lot more add-ins and templates to choose from too.
By the way, the new layout doesn’t seem to look perfectly from my iPhone, which tells me there are still some work left to do.
]]>didn't know that you have a twitter account ! I guess I shall get one too.
haha nice I'm thinking to create my own blog too lol and maybe try out and use the WordPress since its so popular these days
]]>
Asp.net for the most part is irrelevant when it comes to scaling, because it uses so little resources. I use StringBuilder, Response.Write and access the DB. C# is the last thing I think about when it comes to scaling issues, its 99% the DB.
Right, it makes right to the point what really matters when it comes to scaling. It’s not the type of web server that hosts the website, not the engine that powers the website, not the language that codes the website. It’s the DB that matters the most. Having a very good design of database, fine-tuning the DB server, and optimizing all queries being called to the DB are definitely the top things you need to take close look.
When a guy who runs a website that has the following stats, you better believe it. Besides, Markus was an IT Pro before diving into the web developing , so he knows what he’s doing.
I'm still doing everything myself except for customer service.
Current numbers are.
60-65 Million Pageviews per day, 4.4 million per hour peak.
72 million visitors a month
3 load balanced Windows Server 2003 x64 web servers with 2 Quad Core CPU sits at about 20% cpu at peak, 2 Quads... Makes it easy for me to take servers up and down without worrying about crashing.Sites running on 5 DB's now, between 64 and 128 GB of ram, Got a huge 30% increase in traffic coming on Dec 26th same as every year. Every page on the site has a bar on images on it... To create that bar a radius search is done along that uses your history as well as preferences. Its not possible to cache anything as its true personalization and each query depends on the previous one. Same with all the searches.
Over 130,000 Concurrent users at peak.
500M images per day.
So it’s time to quiet down all the debates about the pros and cons of which type of language are the best for developing the website. If you really want to build a website, just pick up one that comes to your mind the first and get all your hands working on it, now.
]]>Cannot open user default database. Login failed.
Login failed for user ‘UserName’. (Microsoft SQL Server, Error: 4064)
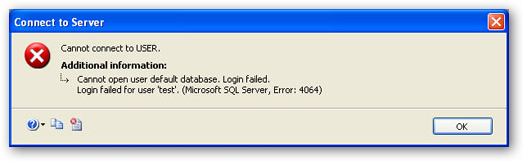
My first thought is where my default database gone. I used to have two DB associated in my account with the one that powers this blog as default. But recently the hosting company, Webhost4Life, decided to bump the space to 100G while reducing the number of MS DB allowed in my package to one per account. For that reason, I guess they may have massed up with user’s default database setting while making these changes. So I filed a support ticket asking why it happened and they responded promptly but instead of simply reset the default database for me they pointed me to this post over on sqlauthority.com, which helped me to solve this issue. Credit goes to Pinal Dave though.
Here is the fix in short:
First of all, you need to change the connect to database to something other than <default>, like master. You need to click Option button on the login window to get the Connection Properties tab to show up.
Then, once you log in, open a new query and run the following script to reset the default database to your account. Make sure to fill up the [test] and master with the right value.
ALTER LOGIN [test] WITH DEFAULT_DATABASE = master
GO
That’s it. Mystery was solved.
]]>It took almost 4 hours downloading the OS image file, which is 2.5G big, not too bad. Comparing to a lot of other people who were trying to get the copy the first day after it was released, I was quite luck as I didn’t have to go through the painful long waiting time.
First impression, installation process is so easy and has no pain to most of people who wants to try. I fired up VMware Workstation on my laptop and started creating a new VM with pointing to the Windows 7 Beta image file as the booting device. About an hour later, I have a fully functional Windows 7 system running on VM, the installation was done successfully and automatically with very minimum interactions involved. The system runs no problem as a virtual machine on VMware Workstation. The VMware tool was loaded without any issue. So my second impression is it works really well with the virtualization technology. The blue-red fish looks so happy swimming on my Windows 7 desktop.
Third impression, the badly accused UAC (User Access Control) is improved quite a bit in Windows 7. It’s totally customizable to meet your needs. If you are the person like me who hates it, you can slide the bar all the way to the bottom, which means no control at all. If you totally agree with Microsoft’s approach about this whole UAC idea, you can move the bar all the way to the top, which works just like Vista. For now, I found leaving it as default worked for me. It has yet annoyed me.
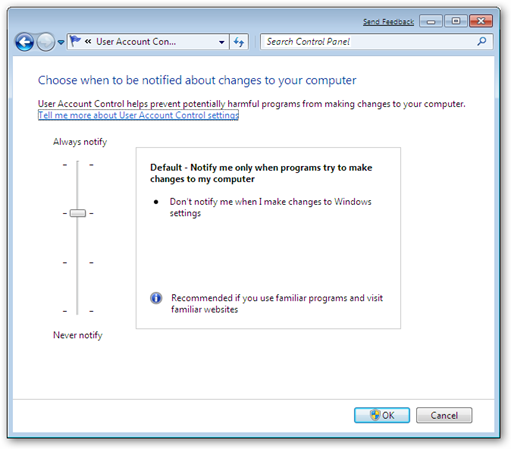
Forth impression, some never changed built-in tools finally have the new life. For example, the new calculator is such a powerful tool that you don’t need other tools to fill the need. It runs 4 mode (Standard, Scientific, Programmer, and Statistics) with 4 options (Basic, Unit Conversion, Date Calculation, and Templates) that cover pretty much all your needs for a calculator.
Fifth impression, Windows 7 includes numbers of new built-in tools that work totally cool. Snipping Tool is one of them, a very nice screenshot tool that works way better just using PrtSc key or Alt-PrtSc key. So I may eventually get WinSnap retired. It offers a feature that allows you to do a free-style snapshot, so cool. The happily swimming blue-red fish is now being caught.
There were also a few annoyances. I have it running on VMware on my laptop without any issues but it crashed a few times on VNC on my assistant’s computer. Quite ironically. I am also panic in the activation process. I entered the key-code I got from the download Window but was rejected after I punched them in.
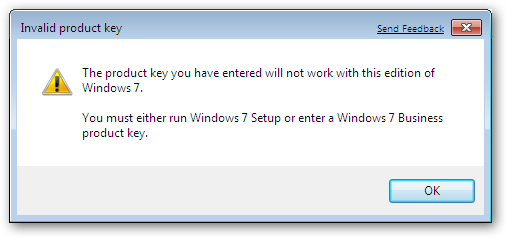
But overall, I am totally hooked. I will be poking around more later to dig out what’s cool in Windows 7. If you are interested, check out the following talk from Mark Russinovich, the author of Windows Sysinternals.
]]>lol maybe I will try to do that on my desktop!
Awesome post! looking forward.]]>
 It’s a two-day training conference in six cities across Canada. Vancouver is the last stop for this training camp tour. Today is the fist day. It’s not free. I registered a few months back when I first heard of it, so I got 50% early bird discount.
It’s a two-day training conference in six cities across Canada. Vancouver is the last stop for this training camp tour. Today is the fist day. It’s not free. I registered a few months back when I first heard of it, so I got 50% early bird discount. I was quite excited about the conference, one of the reason was, according to the website says, the learning kit comes with an approximate value of $1,000 plus bonus offers. And yes, I got full version of Visio Studio 2008 Professional Edition and Expression Web 2, along with a bunch of evaluation software and toolkit, including a full getVIRTUALnow toolset, in a big Techie Crunch box. They also provide you a black hat with Tech Days 2008 logo on it (I guess that’s because of Winter), and a spoon pen but no paper notepad. I was lucky that I have one in my backpack, otherwise I would be trying hard to memorize or type the info on my iPhone.
The conference has many sessions covering both develop and IT areas. I followed my original agenda and attended 2 virtualization sessions and 2 infrastructure sessions. I was quite happy about the 2 virtualization ones but was very disappointed about the PowerShell one which I had a quite high expectation earlier.
The virtualization sessions covered quite a bit information from the essential of Hyper-V to the higher management tool System Center Virtual Machine Manager 2008. It’s quite interesting seeing Microsoft trying hard to catch up the game in the very hot virtualization World. And from what they offered thus far, they were doing very good lately and did caught a lot of people’s attention about their new approach. I will be digging more later and will be posting more in this topic too. The new System Center Virtual Machine Manager 2008 looks pretty cool, it manages VMware ESX servers too.
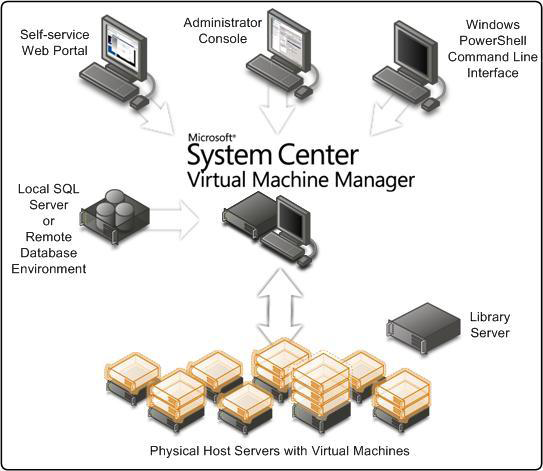
PowerShell is another mission I want to accomplish this year. I saw its value from the first day it was released but just don’t have time to dig deeper. I even bought a book, Essential PowerShell, and I am willing to invest quite bit time on it and I feel it’s worth it because I see how it will benefit me for my day-to-day work dramatically. So I really had a high expectation on the PowerShell session and was really looking forward to it. But honestly, it was quite disappointed. It’s hard to tell what actually was missing but I just felt that it was kind wasting my time sitting there.
Anyway, I will be attending two Infrastructure sessions, one Virtualization and one SQL 2008 session tomorrow. Hopefully, I will get more out of it.
]]>The first session I attended was about Exchange 2007. Rick Claus did an awesome job that delivers tons of useful information to his audients with his hat still on. I sure the time was very worth it spending there. I wasn’t bored at all. The presentation well covered the area for migrating to Exchange Server 2007 and is very informative. Here are a few of his statement he made during the session that I found are very useful.
1. Once the last Exchange Server 2000/2003 is removed, you can not bring it in anymore. So think twice before you plan to remove the last “legacy” Exchange server.
2. Outlook 2003 requires Exchange server 2003 to load up. So if you still have Outlook 2003 client around in your network, don’t take the last Exchange 2003 server down.
3. 5000 items performance limit in Outlook 2003/2007 and Exchange 2007. That number applies to per folder, meaning the best practice is to limit that number to each folder. So set up the folder structure or introducing the mail archive solution (my own quote). A side note, Rick revealed that the largest mailbox ever reported to Microsoft as he spoke was 110G big. OMG!
4. When doing the migration, one PowerShell command per Exchange 2007.
5. etc.
Then I went to the next session talking about Windows Deployment, which was good too. It introduced Microsoft Deployment Toolkit to build and customize the image files. It sounds interesting. Desktop deployment is one of the areas I extremely want to get more hands on because currently, it really takes lot of my time to install the workstation. Preparing the user profile for each user on each workstation is so painful, but there will be a lot of time spent on preparing a nice deployment system.
The third session talked about Virtual Machine Security, a topic that is still quite new and hardly see people talk in depth. The presenter is actually a local user who is very specialized on Virtualization. Missed his name during the session but he will be presenting the similar topic and will be doing more real demo in VANTUG later on. I am the member of this user group so I will be looking forward to it. He mentioned System Center Data Protection Manager 2007 during the session for backup and disaster recovery purpose. Very interesting…I sure will be checking it out.
Overall, it’s fantastic. I will be there next time. The money and time are well worth spent.
]]> The one of the first and most well-known IT credential isn’t just becoming legacy, but indeed dead. There is no more upgrade path to MCSE, period, according to Bill Chapman’s post on Born to Learn.
The one of the first and most well-known IT credential isn’t just becoming legacy, but indeed dead. There is no more upgrade path to MCSE, period, according to Bill Chapman’s post on Born to Learn. Sad? Of course, especially this credential has been with me since 1998 and helped me to land the first IT job in Canada.
Move on? already did. I upgraded it to MCSE 2000 but didn’t bother to look at what the path is to upgrade to MCSE 2003. I moved on because I felt it doesn’t seem to matter as it used to be. The whole IT area isn’t just for Microsoft but a lot of other new technologies too.
Still recommend it? Yes, no question about it, especially to the person who wants to step into this industry. I still believe the best path for a new comer to step into this area is to earn one of the industry well-known credentials, start with A+ or Network+ and followed by MCSE track. It not only helps to understand the basic fundamental knowledge how the system works but also provides the actual hands-on experiences.
A good move to Microsoft? I don’t think so. I agree with Under the Stairs completely.
This was disappointing a couple of years ago, and is disappointing now. Microsoft has taken a hugely popular and well understand brand and replaced it with, well what? Replacing a credential with “Engineer” in the title with “Administrator”??? How is that an improvement?. Does MSL really expect anyone to get excited about “upgrading” an Engineer credential with an Administrator credential?
I was one of the first MCSEs in the world, and am still quite proud of that credential. I’m not sure if I could ever get 1% as excited about being an Enterprise Administrator. It just sounds a step down and backwards. As a result, I’m just not chasing the new credentials any where near as fast as I used to. I know I am not alone.
He’s definitely not alone, at least me included. Speaking of “I am a MCSE” sounds much better than “I am a MCITPro EA”. People even in IT will think what the heck is that? Besides, Bill explains one of the reasons as below in his blog:
We’ve earned our new MCITP Enterprise Administrator, and the more we proclaim it, the more recognition it will receive. You should be proud of attaining that certification. This is another case of history repeating, when the MCSE first came out few knew what that was all about either, but we talked about it and those outside our IT circles came to know what we knew, that the MCSE was the person who made the magic of IT happen. The MCITP Enterprise Administrator is the new certification to show who is the one who has the magic of IT, but that does not change the fact that there is no MCSE for Windows Server 2008 and there never will be.
That’s another mistake they are making. Will this really be another case of history repeating? Not a chance. Take look how many players in the industry 10 years ago comparing to how many in today? And how many new technologies have been invented in the past 10 years? Thinking of speaking loudly and widely will get your words and points delivered and hoping the history to repeat is just another sample of arrogant. IMO, there is just no way for MCITP EA becoming as popular as its predecessor, may not even close.
Anyway, I know it won’t change. So, I wish all the best to anyone with this new industry credential.
]]>I have been forced to work stuff with Oracle since a content management system vendor was acquired by Oracle back in 2007 maybe. While their technologies are pretty cool, their support portal is the worst I have ever experienced. It's so pathetic that a company like Oracle developed a service portal that's based on Flash.]]>
 I follow most of the tweets on my iPhone using TwitterFon. It suits me very well except I wasn’t able to twitter anything that I find useful on the Safari on the iPhone. So until I found this useful little free app, I usually send tweets with shortened url on Firefox using TwitterBar addon, which is also super easy to use and automatically uses http://tinyurl.com to shorten the link. But now I can do all that on my iPhone.
I follow most of the tweets on my iPhone using TwitterFon. It suits me very well except I wasn’t able to twitter anything that I find useful on the Safari on the iPhone. So until I found this useful little free app, I usually send tweets with shortened url on Firefox using TwitterBar addon, which is also super easy to use and automatically uses http://tinyurl.com to shorten the link. But now I can do all that on my iPhone. The app is called twitterlink. You can click the link to open the app directly in your iTune App Store. Configuring it is a little trick but the instruction explains pretty so well that I found no problem to have it set up within 5 minutes. Basically, all you need to configure is
1) adding a JavaScript link to the Safari bookmark, and
2) adding your twitter user info in Twitterlink app.
And here is an example of how I used it to send a “2500+ free icon" tweet the other day.
1) I browsed through my feeds in Google Reader on Safari, and I found this “2500+ free icon” post interesting, so I scrolled it down to the end of the post and tapped “see orginal” link which opened another window displaying the original post with original URL.

2) Then I tapped the “Tweet with Twitterlink” bookmark which launched the Twitterlink app.

3) Once the Twitterlink app was launched, it automatically requireed a shorted url using http://is.gd web service. Then I started tapping in all the words, and tapped “Send” button after I finished. The tweet then was on its way to the twitter land.
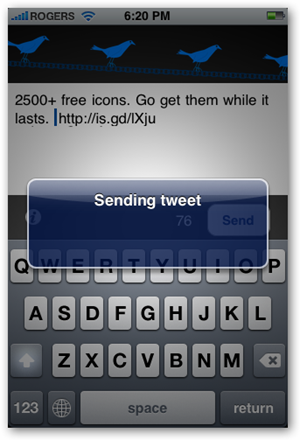
Hopefully it helps because it certainly does help me a lot.
Update [May 9, 2009]: with Twitterrific version 2, you probably don’t need this anymore as Twitterrific has the URL shortening feature naturally built in.
]]>]]>
Update your Twitter randomly according to your intrest Or, from Rss Feed Or, from your own tweet message list Or, Any combination of the above three http://feedmytwitter.com]]>
Here is how I used it to drive to a place to pick up my friend’s son this afternoon in Richmond without any difficulty find the place.
First of all, after opening the Google Map, I tapped the search tab and typed in the address in the textbox. And then I tapped the blue Search button at the bottom of the keyboard to start searching the place. Google Map returned the result and showed the exact location on the map.
And then, I tapped the Direction tab at the bottom of the page, made sure “Current Location” shown as Start point, and tapped “Route” button which calculated all the possibilities and showed the recommended route in Purple.
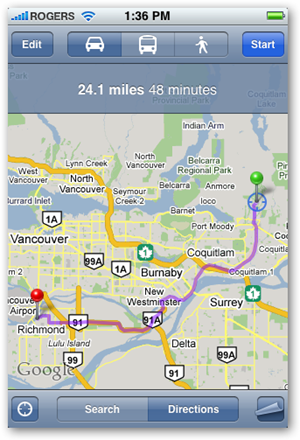
Finally, once I got ready to start driving, I tapped the location button at the bottom left of the page. The iPhone pretty precisely located where I was, and all I had to do was just enjoying my driving by following the purple route on the iPhone from where I was to the destination. About an hour later, I found the place without any trouble.
Please remember do not tap the Start button at the top of the page, doing so will probably mess up the GPS locating and calculated route and you may end up doing it all over again.
That’s it, pretty easy actually. Hopefully it helps to maximize the use of your precious toy. Enjoy your driving and driving safely!!
]]>I wanna buy one iGPS 360 module to install it on my iPod, but it casts $75 bux
]]>
Look the top menu bar:
- Home page link becomes the word family.
- RSS Feed link becomes the RSS food for animals.
Then take look the right side menu bar:
- Recent Posts title now becomes recent job position.
- Twitter Updates now becomes the panic update. This is the funniest one and I have no idea where the heck this panic comes from to Twitter.
And finally take look at the real content, I am totally speechless. I have no idea what I was talking about.
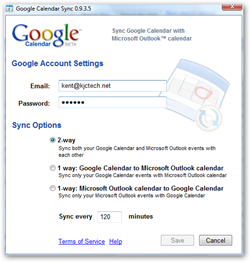 If you are like me using Gmail and Outlook for different purposes on daily basis, this little tool definitely will make your life a lot easier. I am not sure when this neat tool was released but if it’s not new how come no one ever mentioned it?
If you are like me using Gmail and Outlook for different purposes on daily basis, this little tool definitely will make your life a lot easier. I am not sure when this neat tool was released but if it’s not new how come no one ever mentioned it? I wasn’t a huge fun of using Calendar to keep tracking my daily activity but slowly started using it more and more lately. It’s not easy keeping two calendars in different places and is even harder following them without missing it. That’s why I got so excited when I finally discovered it from the Sync link on the top of my Google Calendar page, and wasted no time to give it a try. And I couldn’t happier with the result. Kinda feeling can’t live without it now.
Currently, it syncs with three type of applications, Microsoft Outlook, Apple iCal or Mozila Sunbird, and Mobile Devices, and offers three types of sync methods that should cover all your need. Currently, I am using Outlook option with 2-way sync method so whenever I have an event need to add, I only need to add it once in either application.
Now, with following Gmail labs feature enabled, my Gmail on Google Apps truly acts like my main working desktop that keeps tracking so well on my daily work.
- Offline
- Tasks
- Multiple inboxes
- Google Calendar gadget
- Google Docs gadget
- Right-side chat for sending the log entries to ididwork.
Interesting. Scobleizer also wrote a post today explaining why Facebook has never listened and why it definitely won’t start. He clearly states the recent move from Facebook was brilliant and would be remembered for decades.
Zuckerberg is a real leader because he doesn’t care what anyone thinks. He’s going to do what he thinks is best for his business. I wish Silicon Valley had more like him.
Zuckerberg is not listening to you because you don’t get how Facebook is going to make billions.
Zuckerberg is right. He shouldn’t start listening to his users now.
Will Doug’s move makes Google to re-think its design decision strategy? They maybe should, and learn it from Facebook. If listening too much your hard collected data is going to kill your innovation, don’t listen to it.
]]>I have all my servers and workstations patched before the day kicked in in 2007. And they all work great. However, I noticed several new installed Windows 2003 servers that didn’t turn their clock 1 hour ahead when the spring time started about two weeks ago. These servers all have service pack 2 installed as well as the latest patches. As far as I know, the new DST patch should be all included in this version of service pack. So why these servers ran one hour slower?
I scratched my head for a bit and decided to go to Microsoft’s DST help and support center to check out if there are anything I missed. It actually does have quite a bit new updated information with newer patches released end of 2008 available for all its OS platforms. I followed the wizard and downloaded the 2003 standard x86 version. Bingo, that was it. It solved the problem without booting the server. The clock was forced to move one hour forward. These servers finally were caught up.
So if somehow you happen to get to the same trap, go to the site mentioned above and download the latest patch that I am sure will fix the time issue for you.
]]>
But obviously, SO doesn’t have a Chinese edition, and Jeff (@codinghorror) wasn’t quite happy about that and called it uncool. It was made by a group of Chinese programmers who are very inspired about the idea of SO, stated on their project page on Google Code. And they do admire what Jeff and Joe did on SO, deeply from their heart. They expressed the whole reasons why they developed CNProg and why they’re inspired by SO on their blog, and they expressed quite well. It’s all in Chinese and quite long so I only translated the last paragraph here.
SO is a community that puts forum, wiki, blog, and digg all together. It’s got a very good point and has implemented in a proper way that gets all users involved in the community. Frankly speaking, SO represents a democracy, equalization, open, and justice social relations. It completely rewrites the traditional concept of forum administrator. Instead, everyone participated in the community can vote to determine any promotion or demotions. And from users feedbacks, SO is on the path to the success.
We aren’t intelligent, and we never sparked any idea or thought like that. Now, we can only follow the processor’s step, make a community like SO, that’s how CNProg was born. Being a person who helps others and being grateful.
Well, we can’t really say they are pirates. They respect SO and who made it. They did steal the idea but coded it in total different language, in Django and Python. But why didn’t they change the UI the same time? It’s obviously much easier. Maybe they thought that is another way of showing their respect to the original creator, but that’s obviously not the case in others eyes. Jeff is quite open-minded that he actually wasn’t mind the idea being cloned. He even emailed CNProg that
inspiration is fine but they have to LOOK different; can't have confusion about who is who.
Generous enough, but Jeff, if you ever have chance come across, do you think if it would be a very good idea having CNProg group to be the Chinese sub-sector of SO. Wouldn’t the original idea of having SO be the helpful resources to the programmers all over the world? China has one of the largest developer populations in the world. Extending SO to China will definitely make the SO brand shiner.
Also see,
]]>well so far I haven't see the clone of twitter, guess sooner or later it will come out too ]]>
I would assume that they would be happy to have a Chinese (and French, Japanese, Spanish etc) edition of stackoverflow, so why not instead propose that to them? Just helping out with localizing SO would have saved the cnprog.com crew a lot of coding and time...
I like the way infoq is localized - popular articles are carefully (manually) cross-translated to other languages. Imagine the same thing with SO, volunteers could translate popular questions (and their answers) to cn/jp/es/pt/fr etc to make all that knowledge available to the millions of developers who aren't fluent in English...
JMHO]]>
]]>
I didn’t understand at all why Jeff would turn down such a good thing until I saw his latest post the ugly American programmer, in which he simply believes the fact that “shouldn’t every software developer understand English”. It’s true in general. If it wasn’t this clone thing, I would completely agree with him because speaking for myself, I know how painful it is when coding without understanding English. However, the timing of his post really got me to think it’s something to do with this clone and that led me to believe that the reason why he said “No” to CNProg is because he doesn’t believe why such a thing even worth existed. Localization isn’t a term in his vocabulary. But Jeff, it’s not about learning, and is not about doing the coding work. It’s about building a community, a place where in this case local programmers can ask, answer, share the knowledge, a place that requires full communication in written to interact. Writing in English isn’t like reading in English, and that is a lot of local programmers are lack of. They have no problem learning and reading in English and then writing good codes but asking them to participate in an English-driven community like SO is nearly impossible. When things come down to communication, native language that builds right into your body always wins. Without a place where they can freely express thoughts in their own language, it’s hard to ask them to contribute and participate. That, by all being said, localization has and will always have its own market, a big market. I could go on and on but this post by Jon Hancock, a white guy living in Shanghai since 2000, explains so well on this topic.
When Chinese use their native tongue, the knowledge exchange goes faster and in more depth. It encourages greater participation by a wider audience.
You may think these experiences only apply to offline, in person interaction. It turns out it does not. A site like StackOverflow ends up being more than just discrete programmer question and answer. The discussion grows into rational behind the answers, agreement, disagreement, and derivative topics. It grows into meeting people, online and off, and developing relationships. An English-only website will not be adopted by the majority programmer community in China simply because they are not comfortable enough participating in English. Will this change? Maybe, but its changing very slowly. My money is on Mandarin staying the language of choice for Chinese programmer communities even though their English skills continue to improve.
And the last paragraph from his post wrapped it up all right.
StackOverflow is a great site. I hope it continues to see success. If the folks at StackOverflow wanted to address the China market, the only way they could have successfully done so is to have cloned their own product and run it on a server inside China. They would have to fragment their own start-up.
Jeff and Joe, it’s up to you now if you want to seek the success in China.
Also see:
]]>There is a CC-AS license badge at the bottom of every SO pages, which clearly sends a message to the public that the site is CC-AS-compliant. So, let’s take close look of what CC-AS says. CC-AS, stands for Creative Commons Attribution Share, clearly states:
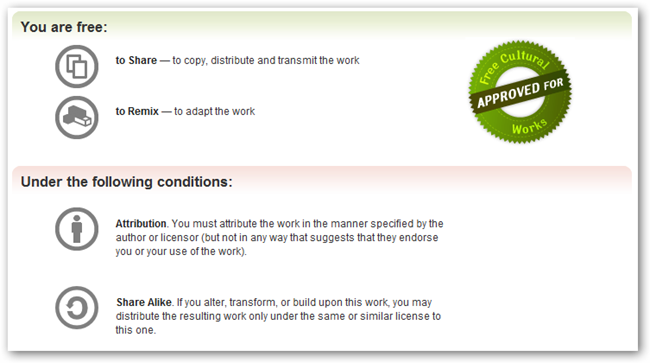
So what did CNProg violate? They are free to share and have adapted the work in Django and Python. They attributed the work on their blog (http://blog.cnprog.com/2009/01/why-create-cnprog/) and Google Code page. And they gave the credit of their work to SO in any possible way, and they do respect SO right from their heart. With the fact that SO turned the idea of localization down in the first place, it seems to me now that they didn’t do it wrong at all, only if they made the UI different it would make the whole case perfect. And that, is all Jeff is asking for right now.
Don’t take me wrong that I encourage the whole infringement. I don’t indeed, it’s completely un-cool that copying everything over. But I do encourage the open-source, mind-sharing, localization and all that can help to make things better. I don’t typically agree some of the saying in why does China copy designs but I do agree that
the West’s tendency of focusing on this copying issue is really looking at the trees instead of the forest, as China will quickly move past this stage and start to create their own innovations very quickly. As it is companies such as Lenovo and Haier are already in the forefront of this new design movement. So I do suggest that companies get over the copying issue quickly, and look ahead and focus on their market positioning, branding, and strategic thinking.
So, Jeff & Joe, here is another call to extend your awesome brand to China?
Anyway, I am taking too much time on this topic so this will be the last one and by then I am moving on. But hey, it’s a pretty good case study that would definitely help me to clear out some of the concerns when building my next project.
Also see:
]]>"site design and logo is © 2009 stackoverflow.com LLC; all user contributed content is licensed under cc-wiki"
Only the user-contributed content is under the cc license. The site design is copyrighted at stackoverflow.com LLC
Apparent, now the cc-wiki license cannot justify the clone done by CNProg. Anyways, I just simply think copying the features including the tiniest details is just totally uncool!]]>
And I still think Jeff and Joe should have worked with CNProg team to have their Chinese subnet open to chinese programmers.
We all say and believe that Sports, or Music doesn't have the board across countries but each of country still uses their own language communicates and develops these two different arts. That should be the same to programming. Programming should have no board across countries too, in which all programmers should be free choosing whatever language to use, no matter it's a computer language or human language.
by the way Ryan, sorry for not approving your comment in time. Blaming on all spams on that one. :)
Cheers, Kent]]>
Today, Microsoft announced that it will buy VMware for $2.5 Billion in a combined stock and cash transaction. This news really came as a shock to me. I was here when EMC bought us and was shocked then. Over time it grew on me and now I really love our parent company. Now though I’m not so sure I’m happy. It’s Microsoft after all. Look at my previous employers - Inktomi (competed on the search side of the house), Novell (enough said), VMware (enough said). I’m also an avid Apple fan. I guess I’ll have to give that up. This really has me going nuts at the moment.
It shocked me to death too and I almost dropped my lunch box when I saw the post. Fair enough, only it’s posted today, April 1. Quite busy today and this one totally made me laugh in the end. However, somehow I wish it’s true so at least I don’t have another line of products waiting there for me to learn. By that being said, sorry Mike, I welcome Microsoft to buy VMware, sooner than later.
Happy April Fools Day!!
]]> What’s bad? Internet interruption.
What’s bad? Internet interruption. What’s worse? No internet.
What’s the worst? No internet for more than 8 hours.
And since the down time in office is still counting as I type, we are suffering the situation that is more than the worst.
Luckily, we have a backup line that stands by all the time prepared just for this. So we actually don’t get much impacted. Most of our users didn’t even notice it. Only the remote users do, as they need to switch to the different IP to connect. But what if we didn’t have the second line? Frankly, it would be disaster. How can a business that relies on so much Internet run without Internet for that long?
What’s even funnier? They tried to send emails out to their customers alerting them the network outage. How possible were their customers able to receive those alerts? Only the customers like us who have the second line would be able to but how many are they?
Still don’t know what is exactly happening there. Hope they don’t go to the dead pool and out of the business just because of this. But fair enough, whatever the uptime they promised in the contract they won’t be able to keep it up.
I will be digging my contract and see what compensation we can pursuit in this case.
]]>It’s got branded as BlacX from Thermaltake but if you are in Canada you can find it here. It’s not expensive and is perfect in the situation where you need to frequently change the external hard drive. In my case, I use disk-based backup in office. Having this little guy in place makes the whole thing a lot easier. Changing a hard drive just likes old days changing the tape. Eject the old one, and pop in the new one. That’s it. How nice.
The box came in well wrapped.

Let’s unwrap it up.


Now, let’s put it in action.

It’s connected to the white box right next to it in the picture. Once it’s powered on, it’s got recognized immediately.
]]>The privacy of our visitors to kjctech.net is important to us.
At kjctech.net, we recognize that privacy of your personal information is important. Here is information on what types of personal information we receive and collect when you use and visit kjctech.net, and how we safeguard your information. We never sell your personal information to third parties.
Log Files
As with most other websites, we collect and use the data contained in log files. The information in the log files include your IP (internet protocol) address, your ISP (internet service provider, such as AOL or Shaw Cable), the browser you used to visit our site (such as Internet Explorer or Firefox), the time you visited our site and which pages you visited throughout our site.
Cookies and Web Beacons
We do use cookies to store information, such as your personal preferences when you visit our site. This could include only showing you a popup once in your visit, or the ability to login to some of our features, such as forums.
We also use third party advertisements on kjctech.net to support our site. Some of these advertisers may use technology such as cookies and web beacons when they advertise on our site, which will also send these advertisers (such as Google through the Google AdSense program) information including your IP address, your ISP , the browser you used to visit our site, and in some cases, whether you have Flash installed. This is generally used for geotargeting purposes (showing New York real estate ads to someone in New York, for example) or showing certain ads based on specific sites visited (such as showing cooking ads to someone who frequents cooking sites).
You can chose to disable or selectively turn off our cookies or third-party cookies in your browser settings, or by managing preferences in programs such as Norton Internet Security. However, this can affect how you are able to interact with our site as well as other websites. This could include the inability to login to services or programs, such as logging into forums or accounts.]]>
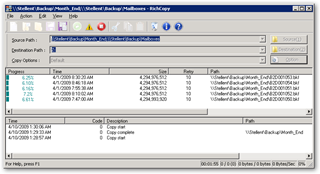 I am an old school guy who simply uses Ctrl+C/Ctrl+V to perform a copy task almost for entire my life. I was tempted to use RoboCopy utility for many times but never felt that need until recently in a case in which I need to move hundreds of thousands files off to an external storage. I was just so frustrated that I finally wanted to give RoboCopy a taste. But somehow this RichCopy tool came to me instead. It was awesome.
I am an old school guy who simply uses Ctrl+C/Ctrl+V to perform a copy task almost for entire my life. I was tempted to use RoboCopy utility for many times but never felt that need until recently in a case in which I need to move hundreds of thousands files off to an external storage. I was just so frustrated that I finally wanted to give RoboCopy a taste. But somehow this RichCopy tool came to me instead. It was awesome. The tool was developed in 2001 and has been updated regularly to keep the pace with evolving needs. It was kept for internal use inside Microsoft for the longest time and was just released to public no long ago. The tool was very simple and only does one thing, copying files, and does it very well. It solves the most common file copying problems as well as all kinds of needs that are required from a copy task. For example,
- Copying thousands of files across a slow connection isn’t an issue anymore.
- No need to worry any glitches that would interrupt a copy process. If it happens, fine, RichCopy will try and pick up wherever it was left off. No more darn evil “copy error” popups.
- Preserve the particular file attributes, such as Modified date, security settings, etc.
- Filtering the files based on the filename or extension, meaning I can copy *.doc files from all folder locations I picked to wherever I want in just one shot.
And you can have all these options set up in one Window.
The most striking thing I found from my first run is.
What you'll find most striking the first time you take RichCopy out for a spin is that it's a multithreaded copying tool. That means that rather than copying one file at a time in serial order, RichCopy can open multiple threads simultaneously, allowing many files to be copied in parallel and cutting the total time required to complete the operation several times over.
Note that RichCopy tool is provided as-is, and you will not get support from Microsoft. But that shouldn’t stop you from using it extensively. It’s an ultimate file copying tool I highly recommended.
]]> This blog is hosted on a Windows-based web server, aka IIS, because it’s based on ASP.net, a Microsoft product that mostly runs on IIS. However, the hosting company is nice enough to have loaded the PHP component on it as well so that I am able to start running my other sites based on WordPress. Because some of the web app are quite relied on the version it would be nice to have an easy way finding it out. That’s why this Quick Only Tips’ tip comes in handy. Tip my hat to them.
This blog is hosted on a Windows-based web server, aka IIS, because it’s based on ASP.net, a Microsoft product that mostly runs on IIS. However, the hosting company is nice enough to have loaded the PHP component on it as well so that I am able to start running my other sites based on WordPress. Because some of the web app are quite relied on the version it would be nice to have an easy way finding it out. That’s why this Quick Only Tips’ tip comes in handy. Tip my hat to them. 1. Create a new document in Notepad or any other text editor
2. Type following with no spaces or lines above or below
<?
phpinfo();
?>
3. Save the file as checkversion.php or any other name you like, but should end with .php
4. Upload using an FTP client to the root of your domain name where wordpress is hosted.
5. Run http://yourdomain.com/checkversion.php in your browser
It doesn’t only show the version of PHP installed on the server, but also does show a lot of other details as well. Ooops, my hosting server still runs on PHP 4.4.4. It’s time to give them a ring alerting that it’s time for an upgrade.
]]>After using it for a while, I already found myself like it quite a bit. The layout is pretty much the same as the previous version, including the logo, but they added a few nice neat features on it that I found quite useful and user-friendly.
Address Bar
The suggested site has built in by default but you can turn it off if you don’t like it. It also grades out the sub-domains and folders in the url so the domain name stands a little bit out. Google Chrome already has this feature built in but FF hasn’t yet.
Add favorites right to the favorites toolbar
It’s quite useful having this little thing right next to the Favorites Star button so that I can add bookmarks right to the toolbar, instead having to go through a couple of more steps in the previous version.
Tabs are now grouped nicely in colors
That’s extremely helpful when you have a lot of tabs opened in your browser because then you can easily identify them where they come from and what they are related to. Nice thought and done, IE team.
![]()
The compatibility view helps
It helps reverse the browser back to the previous engine so 1) it helps when visiting the sites that aren’t compatible with the new version; and 2) it helps web developers to test their sites on two versions of browsers from one computer. It’s the button next to refresh button.
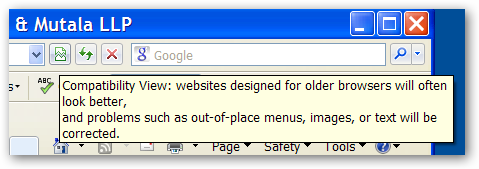
Accelerators do accelerate the browsing performance
When you select any text in the web page, a little blue arrow box pops up from which you can select numbers of choices to do a quick preview. It’s called accelerator, a little neat new feature added in this version that should be quite helpful in some cases.
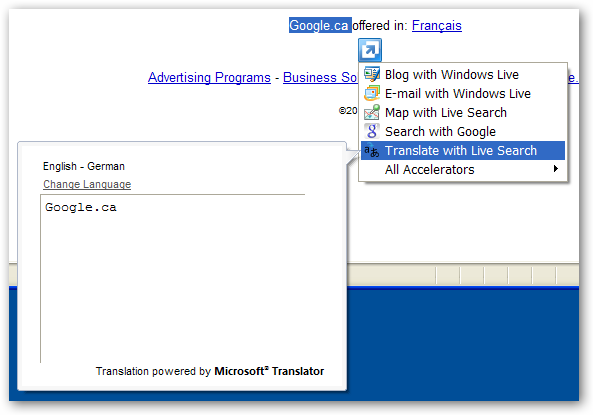
Those are the quite obvious ones I discovered on this new version of IE. Digging deeper, the performance and the speed are quite impressively improved as well, compare to the previous version. In my own case, it’s definitely faster than Firefox, and pretty the same as Google Chrome, but that could be because I have quite a bit add-ons installed on Firefox that slows it down. It’s also quite industry standard compliant. Most of the sites I tested show the exact same result as from both Firefox and Google Chrome.
Overall, it’s a good and must-have upgrade. I will certainly use it more often than before. Nice work, IE team.
]]>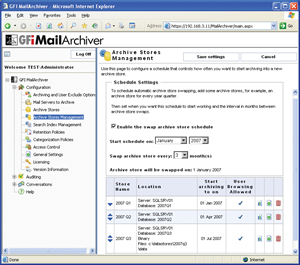 Even though it’s still in beta, I’ve already seen a number of new features and fixes that would make me to update ours as soon as the final version gets released.
Even though it’s still in beta, I’ve already seen a number of new features and fixes that would make me to update ours as soon as the final version gets released. GFI MailArchiver 6.1 BETA1 (build 20090414) now available
Among the numbers of nice new features, here are the particular useful ones I am looking for.
- All new features related to Outlook Connector
- Bulk Export - Emails can be exported to PST file
- Bulk Export - User is now able to download a whole mailbox
- Summary Page in Configuration sub-tree to show the current GFI MailArchiver configuration at a glance
- Global user labels - a user can label an email and all email owners will be able to view/edit it
- A tool, BulkSchemaUpgrader, to upgrade all Archive Stores and Auditing schemas from a single interface
A related note as we are in this topic. I am a big fan of email archiving. It makes a lot easier to manager emails for both end users and network administrators. So if you are in SMB range and haven’t thought of archiving your email storage I highly recommend you doing so now. Once you won’t get regretted at all and will be grateful once you’re done so.
]]> If you are a fan of Virtualization you will find having one of Visio stencil like this handy. I just can’t remember how many times and how hard it was finding a good set of Virtualization icons like this when preparing a network diagram that consists full of virtual servers in it.
If you are a fan of Virtualization you will find having one of Visio stencil like this handy. I just can’t remember how many times and how hard it was finding a good set of Virtualization icons like this when preparing a network diagram that consists full of virtual servers in it. The folks at VESI (Virtualization EcoShell Initiative) have shared the stencil they are using for Visio reporting (the same stencil is also used in PowerGUI’s VMware PowerPack). Just go to the VESI downloads page, scroll to the bottom of the page and download the stencil!
Thanks to Dmitry who dig this out for us, and tip to the folks at VESI for the great sharing.
]]>
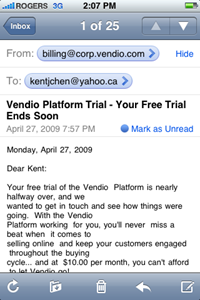
Poking around through the phone settings, noticed that I have Date & Time set to automatically. And once it’s on, emails received today all have the timestamp like the one above.
So I just turned it off, and manually set the time zone to Vancouver, where I live, and the date time. And everything goes normal again.
Hope this little trick helps you if you run into the same kind issue. However, the reason why it all of sudden happened starting early this morning is still unknown at the moment.
]]>I hope Apple or Rogers will fix this.
]]>
Attempted your fix, but then the main time setting on the phone switched!]]>

Welcome to my personal blog, a place where most of the time I talk geek stuff.
My name is Kent Chen. I am a I.T. professional working at a legal firm specialized in Intellectual Property law in beautiful downtown Vancouver. Aside my expertise in I.T., I am also a pretty good web developer and a not bad web designer who has developed numbers of websites and web applications. I like cool tech geek stuff, and am a huge fan of iPhone, Google Apps, now Windows 7, and truly believe in Virtualization in IT world.
The stuff I am writing in this space mostly are the geek stuff that happens in my day to day tech life, the random thought that pops up in my mind from time to time, and some fun stuff I discovered in anywhere. While I am a typical tech geek, I am also very interested in online business, and have a blog that talks my geek’s adventure of doing business online blog. So check it out if you are interested.
I am not a big fan of all hyped social network sites but quite like how the way twitter works. I am a moderate twitter user who has over 250 friends with over 1,000 tweets at the moment. I twitter from multiple sources in various topics, so feel free to follow me there as well and hope you will find them interesting and helpful.
I am also a proud father of one lovely daughter and soon three. Yes, you hear me right, the twins on their way.
That’s it about a quick glimpse of myself. Enjoy, and leave comments whether you like it or disagree what I wrote, or email me if you want to have a private conversation. Response is guaranteed.
Cheers, Kent
kjctech.net/blog
]]> Lifehacker recently conducted a survey in its famous Hive Five asking their readers what their favorite malware removal tools are. And here is what the results are. Just another set of tools that are good adding into your and my toolbox. You just don’t know how useful it would be when you need it in urgent.
Lifehacker recently conducted a survey in its famous Hive Five asking their readers what their favorite malware removal tools are. And here is what the results are. Just another set of tools that are good adding into your and my toolbox. You just don’t know how useful it would be when you need it in urgent. - Spybot Search & Destroy (Windows, Freeware)
- SUPERAntiSpyware (Windows, $30)
- ComboFix (Windows, Freeware)
- Malwarebytes' Anti-Malware (Windows, $25)
- HijackThis (Windows, Freeware)
And what if none of these works? here is your last choice:
This week's honorable mention goes to "Reformat" (as in your hard drive) as a last-ditch, foolproof solution to your malware problems. Apparently sometimes when you find a mouse in the kitchen the only way to be sure there aren't any more of them in the walls is to burn the whole house down.
That’s why it’s so important having a good backup plan in place.
]]> I was going through my feeds on my iPhone during the lunch at my favorite cafeteria downstairs. As soon as I read Why The iPhone Is Revolutionary: Leaf Trombone Edition (AAPL) and watched this YouTube, I couldn’t help but headed over to App Store and coughed up $0.99 for it. And I am hooked and addicted, even though I never played Trombone or any kind of this instrument before.
I was going through my feeds on my iPhone during the lunch at my favorite cafeteria downstairs. As soon as I read Why The iPhone Is Revolutionary: Leaf Trombone Edition (AAPL) and watched this YouTube, I couldn’t help but headed over to App Store and coughed up $0.99 for it. And I am hooked and addicted, even though I never played Trombone or any kind of this instrument before. As the world’s first massively-multiplyer musical game, it’s so cool that you can
BLOW into your iPhone and slide your finger to create beautiful melodies. Or use TOUCH mode on your iPod Touch to play without wind. It's that easy!
Always have someone to back you up on your favorite songs with Leaf Trombone's Musicbox. From thumping bass to gentle arpeggios, the Musicbox can handle it all.
Be the judge on the world stage sharing your joy or pain in real-time as you join two of your Leaf Trombone peers judging performance across the globe.
and many more…
Enjoy and happy tromboning over on your cool iPhone.
]]> This blog is powered by subText, an open source of ASP.net based blog engine. And because I am an ASP.net web developer I ought to use a blog engine that is powered by ASP.net. And because of that, this blog is hosted on windows based IIS web server at Webhost4life who once is a very good hosting provider for ASP.net based website. They also generously add PHP support on their IIS server as well, which is why when I started my other two new blogs I went ahead and used self-hosted WordPress as the new blog engine.
This blog is powered by subText, an open source of ASP.net based blog engine. And because I am an ASP.net web developer I ought to use a blog engine that is powered by ASP.net. And because of that, this blog is hosted on windows based IIS web server at Webhost4life who once is a very good hosting provider for ASP.net based website. They also generously add PHP support on their IIS server as well, which is why when I started my other two new blogs I went ahead and used self-hosted WordPress as the new blog engine. Everything went extremely smooth, except one thing. Loading the website is quite slow, painfully slow when you first access it, especially when the site is new and only have certain numbers of visitors a day. It’s a major problem that I need to address, as I have another WordPress powered website launching soon.
The problem is, web applications hosted on IIS are all session-based. When the site is staying in idle long enough, all launched, cached session will be all shut down and the state related to that session will be cleaned up accordingly at the same time. So when next visitor comes to the site, the web server needs to launch the same process again, which takes time and slow. I am not an Apache expert, so I am not so sure if that applies the same to the sites hosted on Apache.
The solution is, either configuring the web server to extend the timeout, or setting up some tools that constantly check the website, like once per minute. I don’t own or have control on this web server, so I went for the second option.
I could write a simple app that does the work, but instead of doing that, I installed a free network monitor app PRTG Network Monitor on one of my computers that pretty much run 24 hours, and set it up so it uses http/get to check out all my new launched website once per minute.
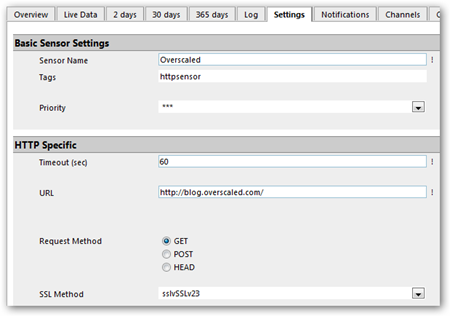
The results? Awesome. Accessing these new launched websites that only have a few visitors a day is blazingly fast now.
]]>Went up twitter status, yes, it’s true that
We’re planning a significant database upgrade that will greatly increase system performance. To do this, we will require two planned maintenance windows: Friday, May 8th from 2p-3p Pacific and again on Monday, May 11th from Noon-1p Pacific.
We’re taking these maintenance windows earlier in the day because of the extent of the changes involved. We want to make sure that we are able to respond quickly and efficiently to any issues that may arise from the work being performed.
Yes, the goal is good but why on earth a very popular hot online website can plan to do a maintenance which will take the service down for 1 hour at least during the day while most of the twitters are online, whether wasting their time or communicating with their customers? Why?
Twitter certainly doesn’t think people are using their service serious enough for business, which is ok to shut you down for 1 hour.
]]>
Twitterrific, the twitter iPhone app, finally becomes terrific in its recently released new version 2.0. In deed, it becomes an ultimate twitter tool you will ever need on iPhone, at least to me. So why did I get so excited about it today that I even twittered a few times after I had it installed on my iPhone? Here is my 5 reasons.
Reason 1, the UI design is awesome. It looks cool and easy to use. And it even makes switching between applications on iPhone back and forth much easier. Get hands on it, you will feel the coolness.
Reason 2, support multiple accounts. Man, even better than TweetDeck.
Reason 3, built-in powerful two kinds of searches, including utilizing the location service for Nearby search so you can find what happens in the twitter world around you.
Reason 4, unified timeline for replies, DMs, favorites, and more.
Reason 5, powerful tweet actions such as RT, URL shortening, email, text compression, pictures to Yfrog, etc. Note that it doesn’t use the usual RT @ when retweeting but putting via @ in the end of the tweet, which makes more sense.
It also has wide range of advanced settings, which is hard to list them all here. You will have to spend a bit of time poking around to discover the settings that fit you.
Two words, Awe-some! Time to delete all other twitter apps from you iPhone, because ultimately this is the only one you will ever need. :)
And if you are interested, you can check a little bit secret behind the design from Choices on furbo.org, one of the author’s blog.
Get Twitterrific for iPhone and iPod touch [Iconfactory]
]]> If you haven’t used Gmail yet, don’t wait because you are so behind. If you are using Gmail but only for emails, you are missing so much other cool features. Gmail is not just a simple email program anymore. You can make it your ultimate a all-in-one productivity center and use it to organize your daily work. Thanks to zenhabits for having a complete checklist to make Gmail your ultimate productivity center.
If you haven’t used Gmail yet, don’t wait because you are so behind. If you are using Gmail but only for emails, you are missing so much other cool features. Gmail is not just a simple email program anymore. You can make it your ultimate a all-in-one productivity center and use it to organize your daily work. Thanks to zenhabits for having a complete checklist to make Gmail your ultimate productivity center. It’s already pretty clear that Gmail is the best tool for email, and integrations with calendar and chat have made it the go-to place for much of our information. But Gmail Gadgets have allowed us to bring the rest of the pieces of the puzzle together. Now we can do just about everying in one place - Gmail.
Here is my list:
1. Email: of course, it’s where Gmail is good for.
2. To-do: a recent added Tasks feature that can be used just as a simplest to-do list.
3. Calendar: integrate Google’s Calendar in Gmail’s sidebar so you can see your events at a glance while in email, and you can add tasks quickly right in that little box too in a format like “12:00pm Tuesday meeting with boss”. And if you want blend your personal calendar with your working calendar, Google Calendar Sync may be useful.
4. Twitter: I am half hooked on Twitter. So thanks to Zen for sharing this tips that integrating Twitter in Gmail by entering Twitter Gadget.
5. RSS feeds: it’s not exactly in Gmail but a trick also I learned is add Google Reader to my Firefox sidebar. Nice, it’s like reading iPhone-type feeds format on desktop.
And here is the most important tips of all from Zen, and believe me, that IS very important.
Finally, now that you’ve set up Gmail to do everything you need it to, here’s the most important tip for staying productive: don’t keep it open all the time.
Ideally, schedule certain times to use Gmail and the other gadgets you have set up — maybe 2-3 times during the day. Or close it when you’re ready to work on an important task, and then open it when you’re done with the task, but only for 10 minutes. Find what works for you, but set your limits and stick to them!
How to Make Gmail Your Ultimate Productivity Center [zenhabits]
]]>
I love Gmail, and as a geek, I love gadgets too. So when the Gmail team came up gadget support in Gmail Labs, I was thrilled and started wondering how many cool gadgets would be out and integrated in Gmail. This is just a small collection of the gadgets I collected, which I hope you will find useful.
Before I started, in case you don’t know how to enable and use the gadget in Gmail, here is a 2-steps to start.
Step 1: In Gmail, go to settings then Labs tab. Find “Add any gadget by URL” pretty much at bottom of the list and make sure it’s enabled, and then press Save Changes.
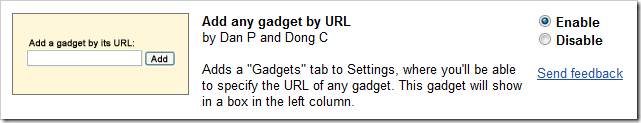
Step 2: Still in Settings in Gmail, go to the Gadgets tab. Copy and paste the gadget URL into the “Add a gadget by its URL” field. Press Add.
And now let’s get the fun part started. All you need to do with these links is to add them into the URL described above in Step 2 if you like them.
Delicious: http://www.labpixies.com/campaigns/delicious/delicious.xml
Digg: http://digg.com/goog/ig.xml
Facebook: http://www.brianngo.net/ig/facebook.xml
FriendFeed: http://friendfeed.com/embed/googlegadget/spec
Remember the milk: http://www.rememberthemilk.com/services/modules/gmail/rtm.xml
Twitter: http://www.twittergadget.com/gadget_gmail.xml
YouTube: http://scrapur.com/apps/gtube.xml
Zoho: http://gadgets.zoho.com/zc/index.do (note that Zoho offers a list of gadgets for its different services, click the OpenSocialXML to get the proper URLs)
Enjoy, and happy Gadgetting.
]]> Ok, you may ask first why would we want to do that, especially in the most of the time we always feel the lack of real state we have on the screen? Well, there are number of times during the week when I am preparing the post, in which I constantly switch web pages back and force finding the information, copying/pasting links, and comparing the contents. And I was always wondering if there are any better way for me to manage them. So this may be an option, splitting the browser. However, it may not help you too much if you are already on a dual-monitor or triple-monitor union. If that’s the case, you can just ignore this post.
Ok, you may ask first why would we want to do that, especially in the most of the time we always feel the lack of real state we have on the screen? Well, there are number of times during the week when I am preparing the post, in which I constantly switch web pages back and force finding the information, copying/pasting links, and comparing the contents. And I was always wondering if there are any better way for me to manage them. So this may be an option, splitting the browser. However, it may not help you too much if you are already on a dual-monitor or triple-monitor union. If that’s the case, you can just ignore this post. Google Chrome
Thanks to Chrome Plugins for sharing this tip in Google Chrome Dual View. The trick is they provide a bookmarklet that you can place on your Chrome toolbar. That’s just another good example of the beauty of bookmarklet.
To use simply drag and drop the following in your bookmarks…
When clicked, a pop-up box asks for the first URL which will be the left panel and the URL you are currently on will be entered by default however this can be changed so in my dual search i entered Google.com for this one. Once you ok it, it will ask for the second URL which is the right panel and i entered Yahoo.com for my search comparison.
Simple, Google Chrome split down the middle with a double panel all in one tab.
Firefox
Thanks to Lifehacker for the download of the day: Split Browser (Firefox)
Once installed, you simply right-click, select "Split Browser to" from the context menu, and then choose a direction: above, below, left or right. Each new window is like a mini browser, complete with its own address bar and navigation controls. You can drag links into any of the windows and even move windows around. However, there's one rather annoying glitch: When you load a favorite, it appears only in the original window, not the window that last had focus.
So, how about searches?
Thanks to @JonathanHu for twittering the ultimate search from Twoogle, a very nice well done search tool that combines both Twitter search and Google search in one window.
And hope this helps, and happy splitting your browsers.
]]>The good thing is there are number of 3rd party apps available on Apple store for that purpose. However, the bad thing is only few of them are free. And unfortunately, you won’t be able to find one that suits you all the needs.
So, what do I want to track over on iPhone while I am on the road? Here are 4 things I would like to be able to track:
- Google Analytics stats
- Google Adsense earnings (mostly quite disappoint though :))
- FeedBurner subscribers
- Twitter followers
So here are what I use:
![]() It costs you $1.99 but totally worth it. I recently just purchased it and only feel I should have bought it sooner. Why?
It costs you $1.99 but totally worth it. I recently just purchased it and only feel I should have bought it sooner. Why?
Ego gives you one central—and lovely—location to check web statistics that matter to you. With support for Feedburner, Google Analytics, Mint, Squarespace and Twitter, you can quickly view the number of visits to your website (including daily, hourly and monthly numbers), feed subscription totals and changes, and how many people are following you on Twitter.
More nicely, it uses widget module, which means you can add as many as widget you want, and each widget can be one type of track associated to your account. For example, you can track 2 feeds, 3 analytics, and 5 twitter account all in one window on one App. Isn’t it nice?
This app is probably the best app for tracking Google Analytics. Well, the data is very limited but hey, it’s in real time, which is even better the web version, in which you will have to manually change the date range to find the current states.
And this is probably the only app on iPhone that tracks your FeedBurner subscribers. The downside is you will have to sacrifice a bit of privacy of enabling Awareness API under Publicize to allow external to access your data.
This app covers 3/4 part of my needs, which leaves only Google Adsense that I should cover. Two apps currently on my iPhone for that task.
I got it free back then but now it charges $1.99 for it. It’s a very simply app that only does one thing, check the Google Adsense earnings in near real time currency conversion. You can check your earnings as the day goes by, in one tap (after initially logging into your AdSense account). However, it won’t be that excited if you are like me, disappointed most of the time.
Another paid app that costs you $3.99. However, I got it for $0.99 when it’s on sale. Another little app that just does one thing. It does offer more data than iSense, for example day-to-day comparison chart. However, I still like iSense a little more because of its simplicity.
![]()
![]()
That’s it. That’s how I track my things while I am on the road. If you have any other tips and tricks about how you did it, or if you have any other good apps that do the same thing, feel free to share in the comments.
Enjoy, and happy tracking.
]]>iAdSense is an horrible app can't believe they are charging $ for this kind app ]]>
 Ever since I had my first glimpse on Windows 7, I have been hooked. The more stuff I learn from Windows 7, the more I like this new Windows Operation System Microsoft about to release later this year. It’s very much nice done in many way and corrected many issues existed in Vista. By claimed as “Vista Done Right”, I truly believe that it will be another well-done OS that maybe dominate for the next few years. Hard to beat how long XP dominates, but should be close too.
Ever since I had my first glimpse on Windows 7, I have been hooked. The more stuff I learn from Windows 7, the more I like this new Windows Operation System Microsoft about to release later this year. It’s very much nice done in many way and corrected many issues existed in Vista. By claimed as “Vista Done Right”, I truly believe that it will be another well-done OS that maybe dominate for the next few years. Hard to beat how long XP dominates, but should be close too. My friend Jonathan seems to believe that too. When the idea having a blog-based website dedicated to Windows 7 came up, we both agree that would be a nice approach that will not only make us learn more and in depth about Windows 7 but also benefits people who are seeking the answer to some questions we may already have covered on the site. The website name is inspired by lifehacker, a site both Jonathan and I and many other people enjoy learning. However, because hacker has its reputation on doing things most of people are sacred of, we should claim that:
we are not the hackers who want to hack the Windows 7. Instead, we are the geeks who want to share the hacks we discovered.
After I successfully got this domain registered, I went ahead and registered the same name on twitter, which already gained over 130 followers, thank you all followers, by the way. So follow us on Twitter for more frequent updates if you are also like us, twitter hocked.
Come by there, and enjoy. Oh, and don’t forget to leave any comments you may have on any topics you are interested. And if you are the geek like us who also likes Windows 7, and have something want to share, feel free to contact me. We are open for guest posting.
]]>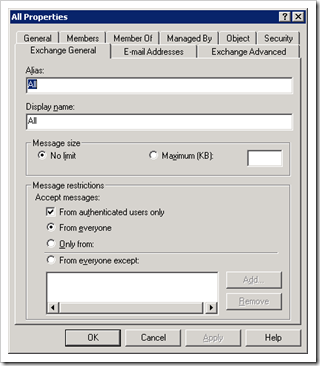 The info from my two previous posts, here and here about the same topic wasn’t quite complete and doesn’t seem to work in ASP.net 3.5. So here is another update on this topic, in cause someone is running into the same issue as I had.
The info from my two previous posts, here and here about the same topic wasn’t quite complete and doesn’t seem to work in ASP.net 3.5. So here is another update on this topic, in cause someone is running into the same issue as I had. So, what is the authenticated email?
It’s a method used in Microsoft Exchange mail server that prevents an account from receiving emails from outside the network, typically for spam emails. It’s especially useful when used in distribution groups that are only used internally. To enable it, you can simply go to mailbox’s Exchange General properties and tick the option From authenticated users only under Message restrictions section, see picture at right.
In order to send emails to the email account that has this option enabled from a web form in ASP.net,
First, set up the security authentication impersonate in web.config file to pass the proper authenticated credential to the mail server. However, you may skip this step if you just use one central email address as the sender.
<system.web>
<authentication mode="Windows"/>
<identity impersonate="true"/>
<authorization>
<allow users="*"/>
<deny users="?"/>
</authorization>
</system.web>
Also, check the authentication methods in IIS to make sure it’s set to Integrated Windows authentication, see below.
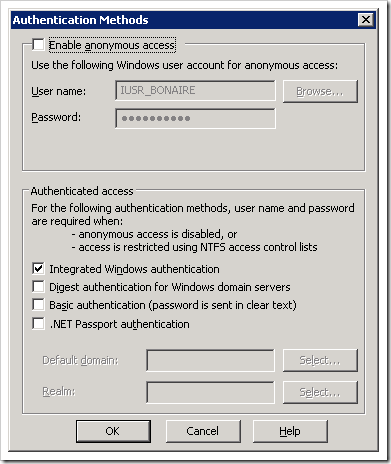
Then, set up the mail server settings in the same web.config file.
<system.net>
<mailSettings>
<smtp>
<network host="mailserver" defaultCredentials="true" />
</smtp>
</mailSettings>
</system.net>
You may add userName and password in network tag to pass the authentication info if you passed the first step.
Last, this is very important and tricky one. You will have to make sure whatever email address you use as a sender has to be a real and associated with an actual user. Or, the following message will be bounced back to the sender and the email will not be delivered.
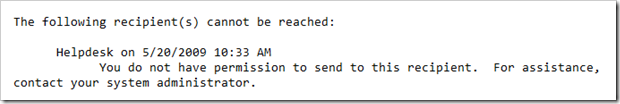
I think that’s it. It may also work in ASP.net 2.0 as well.
]]> I have a small web application written in ASP.net 2.0 (works on 3.5 as well) with Ajax enabled. What it does is to search information on a online database and downloads as PDF. I use <asp:UpdatePanel></asp:UpdatePanel> to wrap up the web form content, and use <asp:UpdateProgress> to show a modal popup type of progress icon during the actual download.
I have a small web application written in ASP.net 2.0 (works on 3.5 as well) with Ajax enabled. What it does is to search information on a online database and downloads as PDF. I use <asp:UpdatePanel></asp:UpdatePanel> to wrap up the web form content, and use <asp:UpdateProgress> to show a modal popup type of progress icon during the actual download. It works great except when the PDF is bigger than a few megabyte this nice Ajax type of progress modal disappears without any results returning to the content in the UpdatePanel. I scratched my head many times without any luck finding it why, until I fired up Firebug in my Firefox and tried again the same process. Bingo. the following error was thrown out in Firebug console.
Sys.WebForms.PageRequestManagerTimeoutException: The server request timed out
Searching for Sys.WebForms.PageRequestManagerTimeoutException brought me to this page on ASP.net forum, in which a poster explained very well what it is and how to solve it.
For Sys.WebForms.PageRequestManagerTimeoutException, check here and here for what it is.
To solve this problem we can increase the timeout. You can change the timeout time by adding a new property to the script manager control. This property is called AsyncPostBackTimeOut and it can help us to define the number of seconds before the request will throw a request timeout exception*.
For example if you want that the timeout will take maximum 10 minutes your code should be look like this:
<asp:ScriptManager ID="ScriptManager1" runat="server"
AsyncPostBackTimeOut="600" >
</asp:ScriptManager>
The default value of the AsyncPostBackTimeOut property is 90 seconds.
Sure enough, adding the AsyncPostBackTimeout property and setting it to 3600 seconds solved my problem nicely.
]]> My first hands on experience about Windows 7 is on a virtual machine on VMware. It runs great but unfortunately no Aero theme due to the limitation on virtual environment. I wanted to install it on my laptop but for the time being I haven yet ready getting rid of my Vista. And I am not a huge fan of multi-boot at all, because I don’t want to mess up my hard drive partitions. Besides, I don’t have much physical space for a separate partition anyway. So that’s why I got so excited and waited no time to give it a try when I first heard this Native VHD Boot supported in Windows 7.
My first hands on experience about Windows 7 is on a virtual machine on VMware. It runs great but unfortunately no Aero theme due to the limitation on virtual environment. I wanted to install it on my laptop but for the time being I haven yet ready getting rid of my Vista. And I am not a huge fan of multi-boot at all, because I don’t want to mess up my hard drive partitions. Besides, I don’t have much physical space for a separate partition anyway. So that’s why I got so excited and waited no time to give it a try when I first heard this Native VHD Boot supported in Windows 7. The test came out with the good result. I successfully made it work both in Windows 7 and Vista. And now I have a nicely organized dual-boot on my laptop, one to the pre-installed Vista, and the other to the Windows 7 installed VHD file. No more hassle playing around the boot partition. How nice is that!
You can follow this post on Windows7hacker to native boot VHD on Windows 7 hosted computer, or if you are the same like me who still wants to keep Vista for a while, follow this post to native boot VHD on Windows Vista hosted computer. Haven’t had chance try on a XP computer so can’t really tell if it’s going to work.
Here are also 5 things you need to know about this native VHD support feature in Windows 7.
1. The word “native” in the term really means what it suppose to mean. It supports and utilizes almost full hardware devices connected to the physical system when you boot in VHD. No more hardware limitations that usually happen on a virtual machine. However, the downside is you lose hardware-independent at some point. For that reason, it really doesn’t make any sense to me native booting to a Windows Server installed VHD. This feature is very nice and built for desktop computers.
2. Native VHD boot only works for VHDs that contains Windows 7 or Windows Server 2008 R2. The earlier versions of Windows are not supported. Here is the explanation from Windows Virtualization Team.
When Windows boots from a VHD file, all the ‘disk I/O’ to load the kernel device drivers, start system services, and run applications is translated to I/O to the VHD file initially, and then to I/O to the NTFS volume and the physical disk. On shutdown, all outstanding write operations flush to the VHD file and underlying physical partition in the proper order before the storage stack shuts down the disk device. Because of these enhancements to core parts of the system, native VHD boot only works for VHDs containing Windows 7 or Windows Server 2008 R2 and not earlier versions of Windows.
3. Because of the same reason, BitLock is not supported. And you can’t hibernate it either, though you can still put it on sleep. At least, these two are not supported in RC.
4. The size of VHD can easily be extended. However, you will need to do that in the host environment. That’s the one of the beauties in virtualization.
5. Native VHD boot supports all three types of VHD files: fixed, dynamic, and differencing disks. Whichever you use to native VHD boot, you need to make sure you have enough space on your physical system. Or the blue screen will come visit you.
That’s it. And again, you can follow the 2 posts below to set up VHD boot on either Windows 7 host or Vista host.
Native VHD Boot to Windows 7 [Windows7hacer]
Native Boot to Windows 7 in VHD from Windows Vista [Windows7hacer]
Enjoy and happy virtualizing.
]]>
I have two NetGear GS748TS 48-port switches stacked together acting just like one at work, mainly for all workstations and no servers connect to either of them. It seemed to work fine, except, one of the units kept rebooting itself for no obvious reason once a while, mostly during the day while people are still at work.
After checking out the log file without any luck, I went and submitted a support ticket to NetGear. They replied back and suggested that I upgrade both switches to the latest firmware, which I did a few weeks back. The problem of randomly rebooting itself seemed to have gone away. However, more serious problem emerged as some people started complaining some network slowness issue. On the first couple of cases we fixed them by simply switching to the different port on the switch. But I was getting more suspicious that there must be something else we were missing, as I received more and more same cases with no obvious pattern in it I can look at.
Then both my assistant and I started doing some research and looking around the settings on the switches that would cause issue. One of the possible solution come up yesterday was disabling the STP (span tree protocol) because there were quite a few entries mentioning it in the log file. So we planed to turn this feature off last night. Guess what, the whole network was shut down right after I selected “disable STP” and applied the change. Big ooops.
Went into office really early this morning and tried hard to figure out what exactly went wrong. Luckily, I was able to hunt the monster down within a short period of time. Yes, I was lucky. After I rebooted a couple of times without any luck, I tried to un-stack them but still no luck. Then I disconnected one of them from the main backbone, and all of sudden everything backed to normal. Ok, that’s good. So then I connected to my laptop to the disconnected switch and was surprised find out I was still connected to the whole network. What the heck was going on? I was on a disconnected switch which shouldn’t link me to anywhere on the server but it did. The only possible reason was there was connection between these two switches. Sure enough, if that’s the case, everything started making more sense. It was the network looping that caused all these issues. Damn, I should have realized this way back, and I should have been more careful when installing it in the first place.
To recap, there was a connection that connects both switches together in the first place maybe before they were being stacked together. And because the STP is default on and keeps the network from lopping the loop, we were survived not being shutdown completely but were suffering the rebooting issue as one of the switches sometimes was tired of this looping and decided to take break. And when new firmware was applied, the system got improved that it doesn’t need the break anymore but was thinking too much to decide which way to re-route the looping, which was why the network slowness was randomly reported from various people. And then in the end, when we decided to turn the STP off everything was broken down. But the bright side was we got the issue solved completely.
So what’s the lesson learnt from this exciting experience? NEVER LOOPING.
]]>If your switches are looping... MAKE THEM STOP! Hahaha.]]>
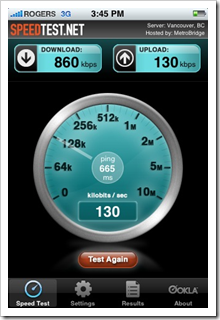
Speedtest.net came up as no 1 when Googling “speed test'”, which I use quite often testing the internet speed performance. It comes quite handy. What I just discovered last week was they also have a free iPhone App that does the same thing.
It’s interesting and useful when having such a tool on my iPhone so I can test my 3G or random picked WIFI connection. However, I have to warn you that running it too often on 3G connection may cause you quite a bit bandwidth in result.
Here is what I tested on my 3G connection, 860kbps down and 130kbs up, to be honest, it’s quite decent.
Get the Speedtest.net iPhone App [opens in iTune]
Related posts:
]]> Microsoft just released its new search engine lately which they hope they can compete with Google in some way. I started seeing some traffics that came from it, a little bit more than before. Not sure if it continues but I hope so. For that matter, I actually welcome this new service and hope it will be doing good.
Microsoft just released its new search engine lately which they hope they can compete with Google in some way. I started seeing some traffics that came from it, a little bit more than before. Not sure if it continues but I hope so. For that matter, I actually welcome this new service and hope it will be doing good. The home page, see the screenshot at right, looks not bad, certainly not decent but can’t really say ugly or bad either.
The search result page, however, is certainly very poor designed. Whoever designed that page is no way a designer and should not be doing job like this at all. Even in-creative I can do the design much better than this. Why the heck did they put this ugly blended image in the background at the top the page?
Not only that, the logo, is crappy which looks more like something you’d use for a yogurt brand than a search engine, which I agree.
Related Posts:
]]>
A few years back when I was still the only IT guy in the office, during a review after I worked there for half year, I was asked to fulfill a project that is simply just documenting everything in IT. The reason behind that is simply, because the firm needs to be prepared 1) if I got hit by a bus one day; and 2) during the time I am on vacation.
Exactly, it’s just that simple and clear. The business needs to move on no matter what, even if you got hit unfortunately one day. Someone needs to pick things up where you left when bad thing happens. We all work hard designing a system equipped fully redundancy that can hardly fail, but without a good documentation system in place we are putting ourselves in a position where we become a single-failure-point to the system. So if you haven’t started, you better start it soon. Just don’t put yourself in that position. And if you already started, well, you will have to keep doing it to no end.
So, are there any good guidelines out there?
There was a exact question asked on Server Fault yesterday, which got a very nice answer that lists some of the principles that should be kept in mind when doing documentation.
Principle #1: It’s never done!
Principle #2: The only thing worse that no documentation is WRONG documentation.
Principle #3: You are writing documentation for your successor, not for yourself.
Principle #4: “Why” is often more important than “how”
Principle #5: It has to be easy or you won’t do it.
Very precise and practical. A very good summery.
And what should be documented?
My take is everything. Or at least try your best documenting as much as you can. The more you document, the better. The only thing you don’t document is the thing you are not certain, because the principle #2 says the only thing worse than no doing is doing it wrong.
Any good tools out there to easy this endless work?
Well, I would say you should be using whatever works for you, no matter it’s just plain text file saved in your file system, or more advanced system like wiki. However, apparently, wiki is most popular choice in IT world. It fits just so well. You can just pick some of the good wiki open source and working on it.
I thought about that too back then but found it wasn’t quite fit at least for my requirements. At least, posting stuff on wiki wasn’t that easy to me, which seems to violate principle #5 :). Instead, I set up a blog type system using Graffiti CMS, and use Windows Live Write to post. So far, it works great.
I also posted the same question on Server Fault, which already got some good responses. So if you are interested, you can definitely go and check it out.
Enjoy, and happy documenting what you do at work. :)
Related Posts:
]]> There are news all over the place today as Apple’s WWDC (World Wide Developers Conference) went by, so no need to repeat them here again. Just go and look at Apple’s iPhone page to find out all the buzzes happening there.
There are news all over the place today as Apple’s WWDC (World Wide Developers Conference) went by, so no need to repeat them here again. Just go and look at Apple’s iPhone page to find out all the buzzes happening there. I am a huge fan of iPhone, and guess won’t be changing it any time soon. From my point of view, there are just no other alternatives come close, heck, I should say they are way behind the game. No matter how hard these venders push the market trying to catch up, it’s just not happening. The much anticipated Palm Pre was just released not long ago but feel too bad for them as Apple seems to have beaten them again in every category, even the price is cheaper than what it offers at $199. It got sold 50,000 items in the first launch weekend, but sorry, the number is not even close to how many the first generation iPhone sold in the first launch weekend, not mentioning the 1M items sold when 3G launched.
With the new iPhone 3G(S) released on June 19 and much anticipated iPhone OS 3.0 released 2 days earlier, it’s actually leaving almost no room for others to play in this game. Just look at these new features included on both device and OS, there is finally a phone that comes out and beats iPhone.
- MMS
- Video Recording
- Cut, Copy, Paste is finally here! (Yay)
- Undo support
- Landscape keyboard works in email, notes, and messages.
- Search. You can search calendars, music, notes and email.
- Spotlight
- iTunes to allow rental and purchase of movies from the iPhone.
- Enhanced Parental Controls with control over movies, TV shows and apps.
- Tethering. Allows you to share you iPhone internet connection with a PC.
- Update to Safari:
- Faster than ever before!
- Support for HTTP streaming audio and video. Bitrate and data quality adjust to connection speed.
- Autofill allows you to optionally remember usernames and passwords.
- HTML 5 support.
- Find My iPhone Service.
- iPhone OS 3.0 will fully support 30 languages.
- 1000 new APIs in iPhone 3.0 SDK.
- Push Notifications
- Books for the App Store.
- 3.2 Megapixel camera (with autofocus, low light and macro modes)
- Voice Control
- Digital compass
- New Accessibility Settings with VoiceOver.
- Built-in support for Nike+
- 32GB Storage
While I won’t be able to get my hands on the new iPhone 3G(S) anytime soon, probably will have to wait until my current one’s contract gets expired, I will definitely try out the 3.0 OS as soon as it releases on June 17. Can’t wait.
Related Posts:
]]>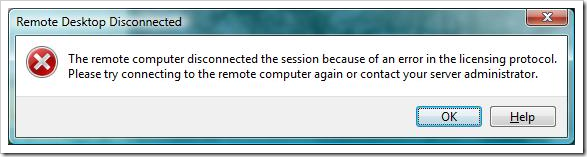
One remote user from work called me the other day saying her remote desktop client stopped working because of “there are no terminal server client access licenses available for this computer”. Well, that’s easy, I walked her through and successfully deleted the MSLicensing registry key on her Windows Vista computer, and happily told her you can try it again now. But surprisingly, she replied a few seconds later saying no, still didn’t work. But this time the error message was different:
The remote computer disconnected the session because of an error in the licensing protocol
It’s surprising because having been using remote desktop client for ages this is the first time I saw the error message like this. Out of luck after a few checking here and there, I went to Google for help. Nothing had worked until I was landed to this Microsoft KB, Removing Terminal Server licenses from an RDP client. At the very bottom of this KB, it mentions:
If you delete the HKEY_LOCAL_MACHINE\Software\Microsoft\MSLicensing subkey on a client that is running Windows Vista or a later version, later attempts to connect to a Terminal Server may fail. Also, you receive the following error message:
An Error occured in the licensing protocol.
And suggests that to resolve this problem, right-click the Remote Desktop Connection icon, and then click Run as Administrator.
Bingo!! That was it. Did I mention that this problem was actually occurred on a Vista computer above? And it only happens on Vista or later OSs because:
By default, the remote desktop connection runs as a user with the lowest user permissions. By default, a restricted user does not have permission to write registry entries to HKEY_LOCAL_MACHINE. Therefore, attempts to rewrite the MSLicensing key fail. Starting Remote Desktop Connection with administrative credentials provides the permissions that are necessary to write the needed registry keys.
Related Posts:
]]>Thanks for the fix! :)]]>
As a iPhone fan, I never felt enough hunting down the good apps that can help me perform my work better, and . as a IT pro the same time, I found having a great list of cool apps on iPhone for various tasks related to my work is extremely useful and handy. Some of them had saved me a few time when I got an emergency call while I was on the road having no access to my laptop.
Let’s start with my own collection first:
- Remote Desktop (RDP) on iPhone
- Tracking Web Stats on the Road on iPhone
- Speed Testing the Bandwidth right from iPhone
- Air Sharing – share the documents with your computers via WiFi and view them on the go.
- My 5 Reasons why Twitterrific is Terrific – yes, IT guy also twitters.
And another list of 12 great iPhone applications for sysadmin and webmasters from guys at pingdom. The list contains tools mostly for web stuff such as whois lookup, domain checkup, speed test, etc., and some other tools for remote control.
And a few others I discovered lately.
- Citrix Receiver from Citrix – a must have app if you are using citrix.
- Skype – too bad, not available in Canada yet.
- myLite – small but useful tool when you have no light in the server room.
- Snap – it stands for Simple Network Area Prober
Last but certainly not least, can’t wait to get the long waited copy-paste and tethering on the OS 3.0 which will be releasing tomorrow on June 17.
]]>
One thing I am struggling on blogging is my writing skills. It seems that grammar errors, typos are inevitable, even though with the help from the spelling check inside the Windows Live Writer. So that’s why this cool well designed web app, After the Deadline comes in handy. I will be using it a lot.
After the Deadline has a very nice domain, polishmywriting.com, which indicates exactly what the website does. What it does is to check spellings, detect misused words, check styles, grammars, and explain errors. The results are quite good because it use artificial intelligence and natural language processing technology to find your writing errors and offer smart suggestions. It’s free for personal use but offers various service plans for commercial use, start from 5 writers all the way up to 500 writers, and suggests a self-host plan for more than 50,000 requests per month.
Overall it’s a very useful web application for people like me who have the bad habit leaving grammar errors and typos all over the place in blog. It’s definitely going to help improve my overall writing skills.
Related Posts:
]]>
When I saw the number of my RSS subscribers jumped to double I was thrilled, more excited actually. However, I know things like that won’t happen overnight. There must be reasons behind. So I log into my feedburner account and dig into “see more about your subscribers” to see what actually made the boost. Sure enough, there are 80 more subscribers came from one source named friendfeedagg, from FriendFeed. Then their latest blog, subscribers count, confirms the change made last night on FriendFeed aggregator that shares their subscriber counts with your favorite FeedBurner subscriber count.
We're happy to announce that we've recently started sharing FriendFeed subscriber counts when we crawl for the latest version of your blog's feed.
So if you have 200 people subscribed to you on FriendFeed, and you've added your blog as a service on FriendFeed, now you can see those subscribers right alongside the subscriber counts from Google Reader, Bloglines, My Yahoo, and anyone else subscribed to your blog's feed.
Is this a good move, from an end user point of view? I am not sure. Some people concerned that it may look too artificial but I am ok with that. As long as that’s the number of people seeing my RSS feeds, I am fine with that. It’s It’s always good seeing more people subscribe and read your hard-worked posts. Besides,
Keep in mind though, that even though this is the number of people who are subscribed to you, the number of people who actually see your posts within FriendFeed can be substantially higher, because whenever one of your subscribers 'likes' or comments on one of your items, that item gets shared with their friends as well!
However, how is this move going to affect the Adsense for Feeds in FriendFeed? I don’t think it works that way.
Related posts (either from here or outside):
]]>
The new iPhone OS 3.0 is out now with one of the most anticipated feature “Internet Tethering” in it. Excited? But wait, are we allowed to use it in Canada? will there be any extra hidden cost on top of the data plan to use the tethering? Well, the good news is:
Tethering Policy
Tethering is the use of your phone as a wireless modem to connect to the Internet from your computer. For a limited time, if you subscribe to a data plan which includes at least 1GB of data transmission between June 8, 2009 and December 31, 2009, and if you have a compatible device, you may use tethering as part of the volume of data included in your plan at no additional charge. Tethering cannot be used with data plans of less than 1 GB.- from Rogers Smart Phone Data Plans: http://www.rogers.com/web/content/wireless-plans/iphone_smartphone_plans
And this guy even went ahead and asked the Rogers’ social media guy Keith McArthur whether tethering would be free for the life of the contract. He confirmed that over on twitter:
What we've said is that tethering will be included at no extra charge until at least the end of the year.
If you are still confused where you are in the plan, this post from iPhone in Canada may help you clear it up. At least, it cleared up my situation,
As for all those people that already have data plans of all different sizes prior to June 8, 2009, you seem unaffected. That presumably means you can tether all you want using the amount of data you have in your data option, even beyond December 31, 2009, and have no worries about extra charges.
Great, now let’s get the fun part started. To enable it, go to Settings –> General –> Network –> Internet Tethering, slide the switch to on, but wait, the error message pops up asking me to contact Fido to enable tethering. What? Why is that? Fortunately, guys at iPhone in Canada seems to have figured it out already.
So it would seem that this is the method in which Rogers/Fido will control this new tethering policy.
The way they do this is through iTunes. Rogers/Fido have what are called IPCC files or “iPhone Carrier Configuration” files. These files are loaded onto Rogers/Fido iPhone’s and give you MMS, Tethering, etc.
In this case, in order to enable tethering, you must call in to Rogers/Fido, have them place an “internet tethering promotional SOC code” (pronounced “sock”) on your account and then tethering will be enabled. The only catch is this is where Rogers/Fido get you because remember, if you have a data plan less than 1GB, Rogers/Fido will not activate tethering.
And they even posted in detail in the same post how you can get around it. However, here is a simply link that you can access from your iPhone to simply replace the tethering configuration file on your iPhone to remove that promotional SOC code. It works like a charm on mine.
Fido Configuration – visit it on your iPhone.
And if you are with the providers other than Fido, check here for a complete list.
The rest of the stuff is easy enough, once it’s enabled, you can tether you iPhone via either Bluetooth or USB. If through USB, make sure the computer that your iPhone connects to has the latest iTune installed because it requires the proper driver to have the Apple network adapter properly installed.
Now, with my iPhone and laptop, I am unbeatable.
Related Posts:
]]>
Long Zheng at istartedsomething revealed some of the best Windows Mobile concepts from Microsoft ATC Studios in Beijing that are never gone public and wondered where actually went wrong for Windows Mobile. By looking at those awesome design concepts of Windows Mobile from Robin Zhu, a very popular and respected UX designer in China who used to work at the ATC (Microsoft Advanced Technology Center), I actually wondered the same.
I had wanted a smart phone for a very long time and during my watching waiting period the ones that are based on Windows Mobile had been pretty much at the top of my wish list. However, I never jumped the gun and acquired one until the release of iPhone 3G in Canada last Summer. So Why had I waited so long and went for an iPhone instead of a Windows Mobile powered device? Simply put, the awesome UI and more UX design from Apple and the seamless Apple Store integration that makes an huge extensive use of device supported by many of awesome 3rd party apps.
It looks like Microsoft already has piles of good concepts in place. What they really should focus on is how to better utilize them and add more innovate user experience design into it, and more, building a better marketplace that attracts more designers and developers to come up more appealing apps for Windows Mobiles. They also need more innovative ideas on top of that to make it successful, because simply following Apple’s step won’t get them further enough to defeat the iPhone.
Keep up all your good work, my fellow Chinese Designers.
Related Posts:
]]>iPhone 3GS
Needless to say, as a big fan of iPhone, it’s always nice to have the latest gadget in hand.
Helium Boombuds Headphone HD-440
My Sony in-ear headphone is getting old and doesn’t have the mic built-in that makes me look so weird while I was on the phone with the headphone. This one comes completely compatible with all versions of iPhone, and with extra bass and inline controller.
Link: http://www.heliumdigital.com/shopping/shopexd.asp?id=79
Cost: $24.99CA

X2 Football
As a long time soccer fan and EA FIFA game player, I had been waiting so long for a soccer game like this on my iPhone. I had hoped EA would come up something like this earlier but this Europe-based game company has beaten EA this time. Right now, I am only playing the lite version which only has training and penalty shootout mode to play with but I am still deeply hooked.
Link: http://www.x2football.com
Cost: $6.99US
]]>iPhone 3GS
Needless to say, as a big fan of iPhone, it’s always nice to have the latest gadget in hand.

Helium Boombuds Headphone HD-440
My Sony in-ear headphone is getting old and doesn’t have the mic built-in that makes me look so weird while I was on the phone with the headphone. This one comes completely compatible with all versions of iPhone, and with extra bass and inline controller.
Link: http://www.heliumdigital.com/shopping/shopexd.asp?id=79
Cost: $24.99CA
Status: owned and enjoying it.

X2 Football
As a long time soccer fan and EA FIFA game player, I had been waiting so long for a soccer game like this on my iPhone. I had hoped EA would come up something like this earlier but this Europe-based game company has beaten EA this time. Right now, I am only playing the lite version which only has training and penalty shootout mode to play with but I am still deeply hooked.
Link: http://www.x2football.com
Cost: $6.99US
Assassin’s Creed on iPhone
Needless to say, if you are a fan of the game Prince, you will love this game. The trailer of this game on iPhone/iPod Touch speaks very well itself.
Cost: $4.99US (has a free version that only last pretty much 5 minutes)
Modern Combat: Sandstorm on iPhone
Another awesome game for Gameloft came on iPhone. It’s another great shooting game that takes place in mid-east Asia. I usually don’t like the shooting games but having play with the free version already got me deeply hooked. I don’t mind shoving out $6.99 for the game. It’s just a matter that if I can find the time to play it.
Cost: $6.99US
FIFA 10 by EA Sports on iPhone
Being a soccer fan for as long as my whole life, I have been playing this FIFA game from EA for over 10 years. So this recently released version of game on iPhone certain worth a spot here as one of items in my wishlist. Too bad, it doesn’t have a lite free version for me to have the first hands-on experience but with the price tag at $9.99, it can’t disappoint me.
Cost: $9.99US
]]>
How many times did you see answers from this membership-based forum popping up on the very top of Google search result? Many, many times to me. I hate this forum so much that I turned myself away every time I see it. I believe it should have been “dead pool” long time ago, especially when a lot of other much better similar sites emerged lately, for example, Server Fault, and soon released Super User.
However, the same feeling has gone once I discovered a few ways of bypassing their sign-up requirement and viewing the answer for free. And I am sharing them now here in order to others can ease the same pain I had. After all, they may have the answer you are looking for down the road.
The official way
Becoming an Expert on Exchange-Expert to view all answers free. You can go to this page first and read all the information about an Expert on EE before signing up as an expert at the bottom of the same page. It’s possible but not that easy to get.
As an Expert, you may earn your Premium Service Membership by answering questions and receiving 10,000 points initially and 3,000 Expert points on a monthly basis to maintain your status.
Another words, if you don’t contribute you won’t earn Premium Membership. And if you don’t earn Premium Membership you won’t get see all the answers.
The dirty way
Spoofing your browser’s user agent string to pretend as a Googlebot. Because all answers on EE are well indexed on Google they must provide the necessary info to grant the access to Googlebot crawl their entire website without signing in a user. Credit goes to here who describe it how in very detail on his blog. In short:
- Download and install this Firefox add-on
- Download this xml file
- Tools>User Agent Switcher > Options>Options>User Agents and Import the file downloaded on step 2.
- In the same window, select “GoogleBot”, go to Edit, enter “GoogleBot” on first line and “Googlebot/2.1 (http://www.googlebot.com/bot.html)” on second line. Leave the rest empty.
- Close everything. Go to Tools, Options, privacy tab, “expections” and block www.experts-exchange.com and experts-exchange.com from giving you cookies.
However, as you can see, it’s not that straightforward and use to use. Quite dirty to me.
The easiest, clean way
Experts Exchange always displays the accepted solution on the page itself if the answer is referred from Google. So all you need to do is scrolling to the bottom of the page or pressing shortcut key Ctrl+E to view the solution, without signing in as a registered user. Credit goes to here. It only works if you are visiting the site from Google Search, which is not a problem to me at all.
you can only view the answers if you are visiting the site from Google Search, if you do not see the answer using the above method, copy the URL or title of the EE forum and search for it in Google, click on the EE link to view the answer using the above method, this should work 99.9% of the time.
One thing I have to admit is that they did a very good job on SEO. Without that, they wouldn’t get ranked so high on most of their answers. And without that, we won’t get see these answers for free. :) Tip my hat to Experts-Exchange’s SEO team.
]]>
The sitemap I am talking about here in this post is mainly used for Google that helps your site got index quickly, properly in Google’s index. It’s in XML format, usually called Sitemaps, with a capital S in it. Google adheres to Sitemap Protocol as defined by sitemaps.org, which is a dialect of XML for summarizing information that is relevant to web bots. It’s extremely helpful if
- Your site has dynamic content.
- Your site has pages that aren't easily discovered by Googlebot during the crawl process - for example, pages featuring rich AJAX or Flash.
- Your site is new and has few links to it. (Googlebot crawls the web by following links from one page to another, so if your site isn't well linked, it may be hard for us to discover it.)
- Your site has a large archive of content pages that are not well linked to each other, or are not linked at all.
So how can I do it?
First of all, you need to generate them. Different blog platform has different way of generating them. You can certainly do so manually by adding the info to the XML file but you can also certainly use the tool or plugin to help you do that on the fly.
If you are using subText which is the one I am using on this blog, you are lucky because it’s already built in the platform. You can just simply submit the proper url like http://yourblog.com/sitemap.ashx to Google Webmaster Tools, and you are all set. Thanks to Phil Haack, the author of subText, for pointing it out.
If you are using WordPress, this Google XML Sitemaps plug in will be very useful and handy. Simply download the plugin from their website, upload it to your WordPress plugin folder, and enable it in Plugins on admin panel. After making a few settings in its setup page, you are good to go.
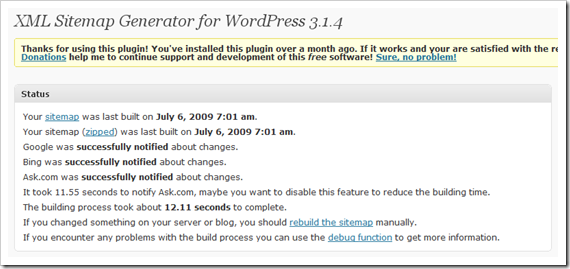
Once you have these set up, now you can log in to your Google Webmaster Tools account and submit them into the Sitemaps under Site configuration. Note that you can actually submit multiple sitemaps for different purposes.
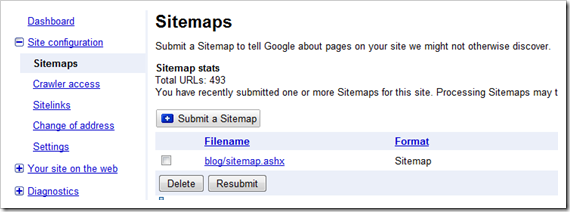
See more detail information about Google Sitemaps here.
Related Posts:
]]>
Overall, it’s a feature-rich and pretty solid backup product for a home user. You can back up files, folders, registry settings, emails and user settings to many types of destinations, including local folder, local network, removable disks, DVD, and remote location via FTP. You can also schedule the task to let it backs up your computers automatically on a scheduled basis. And if you have several computers at home, you can even set up the sync feature to synchronize your files or folders across these computers either manually or on a scheduled task.
You can also either choose replace the backup set or stack them with version numbers so when you do the restore you can actually have a choice to restore the file back to the certain point, not only from the last backup. The backup set also can be compressed using ZIP compression and be encrypted by either Zip password protection or AES encryption.
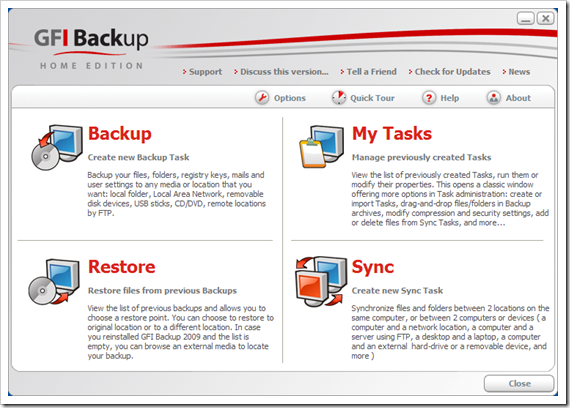
So as you can see, it’s a pretty feature-rich and solid backup product that you can rely on to your home computers. And best of all, it’s FREE, absolutely no charge and no time and feature limitation. Not so sure why they come up a awesome product without charging the customers. Maybe they are also developing an enterprise product on top of it so starting with a free edition to gain more confidence from the end users.
Note that it’s a backup product that backs up your files and folders but not systems. So if you are looking for a product that can also image your computers you may have to Google more to find a more suitable product that does that for you.
Related Posts:
]]>It also could be the page indexed in search engine has the different url, if you come from the search engine. Please refine a search term right in the search box in this page and I am sure you will find the stuff you were looking for.
Otherwise, please just poke around my site as you may find something interesting and useful.
Cheers, Kent
]]> Here is the scenario:
Here is the scenario: I have one Exchange Server 2003 running in the office and have enough Exchange CALs purchased to cover the number of clients accessing the server. I also have Outlook 2003 installed on all clients but now I want to upgrade them to Outlook 2007.
I know that with the Exchange CALs for 2003 I have the rights of using Outlook 2003 for free. However, I wasn’t sure if the same rule applies to Outlook 2007 with the Exchange Server 2003.
I went to my license advisor from Microsoft for clarification, and he quoted me the following statement with the words highlighted in caution as reply:
Outlook 2007 grant for Exchange Server 2003 CAL customers
Unlike prior versions, Exchange Server 2007 Standard or Enterprise does not include the right to install Outlook on devices for which CALs are obtained. However, for each Exchange Server CAL, Core CAL Suite or Enterprise CAL Suite with active Software Assurance coverage as of November 30, 2006, customers will be granted one Office Outlook 2007 license. The right to use Outlook under that license expires upon expiration of the corresponding CAL. Use of Outlook under this offering is subject to the customers’ license agreement and the product use rights for that product. If Software Assurance coverage on the corresponding CAL is maintained continuously (i.e., renewed with no lapse in coverage), and one later version of Office Outlook (i.e., N+1, where N=Office Outlook 2007) is made available prior to the expiration of that coverage, customers’ license will be for that version instead. Alternatively, customers are eligible to acquire Software Assurance coverage for that Office Outlook license, provided that coverage is acquired by February 28, 2007. Customers who wish to acquire Software Assurance coverage for Office Outlook after that date must first acquire a new license for the version of Office Outlook that is current at the time coverage is acquired.
In short, unless you were on Microsoft Exchange 2003 with Software Assurance by November 30th, 2006 you will not be getting a copy of Outlook 2007 when you upgrade to Microsoft Exchange 2007. But what if I don’t want to upgrade to Exchange 2007 and just want to stay with 2003 for a little while? The statement above doesn’t clarify this clearly for me. So I went on and questioned again. And the advisor came back with the words in below:
The Exchange 2003 How to Buy website confirms that each Exchange 2003 CAL does include an Outlook 2003 license (not Outlook 2007), however if the customer is no longer using Exchange Server 2003/CALs they are not permitted to use the Outlook license that is included with the CALs (please note, this has been confirmed by Microsoft as a result a prior escalation)
Even though I couldn’t find the same words on any Microsoft website, because these are the words from Microsoft employee I will be treating this as an official statement. So in this case, it seems unlikely that I can be using Outlook 2007 for free under the license agreement I have right now. He also went on and shared some more info that I think are also worth sharing here.
If a customer licensed Exchange Server 2003 and acquired Exchange 2007 CALs for additional seats, then they have right to install Outlook 2003. If, on the other hand, they licensed Exchange Server 2007 and downgraded the server to Exchange 2003, they would not have the right to install Outlook. This is because the use rights are determined by the version of the software that was licensed, not the version that is being run.
I hope this investigation can actually help you if you are running into the same problem that I have. However, I would still highly recommend you consult your license advisor first before jumping into any decision. And don’t make any assumptions when it comes to license, doing so may cause you more trouble down the road.
If you want to see more info whether or not it’s a good thing from Microsoft you can check here, here, here, and here.
]]>We do that by looking at the "From" header, and when it says "ebay.com" for example, it means it really did come from ebay.com. Anything else is rejected; it won't even appear in your spam folder because Gmail won't accept it.
That’s extremely important and useful to people like me who is heavily involved on eBay and Paypal pretty much everyday. Gmail’s anti-spam technology has already done a very nice job filtering out those phishing emails but this new lab feature definitely adds another “super-trustworthy” layer of protection that keeps the spammers far far away from the end users like us.
"Super-trustworthy" is a technical term I just invented that means: (1) the sender, usually a financial institution, is a target of phishers, (2) all of the sender's email is authenticated with DKIM, and (3) Gmail rejects any fake messages that claim to come from this sender, but actually don't.
It's a bit of work for senders to make their email super-trustworthy, which is why this feature is limited to just eBay and PayPal right now. We hope to add more senders in the future, and when we do, you'll know because you'll see the super-trustworthy key icon magically appear by those senders too.
Nice work!
Related Posts:
]]>- PatchGuard
- Hyper-V support
- Kernel transaction manager
- I/O priorities
- SuperFetch
- ReadyBoot & ReadyBoost
- BitLocker
- UAC
- Windows Integrity Mechanism
- And much more…
The book was written by a group of three fellows lead by Mark Russinovich, a legendary to a lot of people like me who have been spoiled by his famous Sysinternals. If you are a windows guy, especially have used his tools before, this book is highly recommended for deeply understanding how the new operation system works. You can also watch Mark and David Solomon’s interview on the new book on Channel 9.
Windows® Internals, Fifth Edition: Covering Windows Server 2008 and Windows Vista
]]>
Then, I remembered gHacker mentioned one tool a few weeks back that can actually show how many other websites share the same shared hosting. Curious enough, I went to the site, and punched in the IP address of my domain. Guess what? There were total over 160 other websites linked to that IP address. Another words, I am sharing with other 160+ websites on the same shared server box. If one of the users were doing bad thing, e.g. scribing the info off other website which often uses quite a lot server resources and network bandwidth, the other 160+ users would be all suffering the same pain at the same time. Errr…
Moreover, let’s see how much money they can make off that shared server. My shared plan costs me $11.99 a month. Assuming that averagely each user hosts 2 sites, that’s total about 80 users. Times $11.99 per user cost, that’s about $960 they make off just from one server. Most of the users pay annually, that’s $11,500 off one server annually. Man, no wonder some of the ISPs can offer very lower price, especially the cost of the hardware is so cheap nowadays.
You can find out how many other websites share the same shared hosting via myIPneighbors.com.
Updated on July 27, 2009: The numbers of websites that are sharing my hosting is increased to 254 as of today. You calculate the rest. :). However, the performance and reliability seem to be way better than before.
]]>Most probably your ISP has more than one box serving for you (mail? Files? Dns?). They may be making backups. They may have a separate data base server. And even if it is indeed 80 customers per server, they will need to provide support (E-mail/Phone?) for those customers. They need to pay the bandwidth too.
My ISP is significantly cheaper than 12$/month. In fact, they offer colocation from approx. 45$/month. I do not think I could do a much better job for their price.
]]>
Yes, I am aware of the overhead. It's just the number of users on the one same shared server that shocked me. I never took serious look from that angle.
The reason why my package is higher is because it's a windows server w/ one MS-SQL database and 50 MySQL databases. The overall package sounds a pretty good deal. It's just the quality of the service was quite poor lately.
The $45/month for a colo option is quite good indeed.]]>
lol looks like my free server aren't that bad at this category :)]]>
My iPhone has been acting weird lately for a couple of week. It vibrates itself whenever its top part gets pressed. It’s so annoying that it gets to the point where I thought of the warranty. Luckily, when I check it out through Apple’s online service assistant, it shows that it’s still covered but so barely that it expires next week.
Since I got my iPhone through our company account in Fido, I called them and asked for the warranty replacement. They agreed but also suggested I go to the Apple Store to do it myself. Even though I still asked them to ship me the new one, I decided to go to the store myself because according to what I was told by the Fido rep:
Your iPhone will need to be verified with Apple to ensure there was no abuse or water damage or we will be responsible for the full cost of the phone.
And because of that, I highly recommend you go to the Apple store by yourself too so you can be sure your device is fully covered by the warranty and you won’t be responsible for the full cost later on.
However, you will need to book a time to reserve time before you go there, and it looks like the seats are so limited that you may need to wait a bit longer. I squeezed a time in on Monday so I will see how it goes. But based on the issue I have, according to what the tech guy in Apple Care told me, it requires a replacement for my iPhone. If nothing is new to surprise me, I am getting a new iPhone with another full year warranty covered.
So all in all, if you are the early owners of the iPhone 3G and you have some issues on the device, don’t wait, check your warranty status before it gets expired and bring the iPhone to go to the store, and the same time call the service provide in your area to file the claim first to have the records recorded in their system to avoid the surprise later on. I thought to post the whole story when everything’s done but since the time is quite sensitive here, I just post it now and will update later on with the latest status. And hope it helps you if you have the similar situation as mine.
You can go check the warranty online on Apple’s website, and find the physical apple store close to you by googling “apple store” with your location.
Related posts:
]]>Not very enjoyed, but I managed to finish it up within the extended deadline and sent it off. No surprise, SAM team replied back with number of questions that need to be clarified. And then, I communicated with them back and force a few time, and finally finished the review only a few weeks back in a manner that both of the sides are satisfied. And I just received a nice Thank-You card with Tim Horton gift card from Canadian SAM team today. Pretty nice.

The overall experience is quite valuable. I was kind worried in the beginning but felt quite comfortable working with these guys later on. They are fair and understand the importance of having a right software asset management in place in a corporate environment. The most important, I have a better understanding how MS licensing program works and now exactly know where I am in terms of the software license coverage. And as a bonus, I now have the license advisor as the personal contact right from inside Microsoft. Words from their mouth would be more authorized than other places. :)
So hopefully, this will help you if you somehow are going to this same route, either now or later on. And you can always throw questions to me if you have any concerns taking participate in this program, either leaving a comment here or contact me privately here.
]]>
So what’s the difference between the free and pro edition. To be honest, not so much. Let’s see what the free edition offers:
- Antivirus & Antispyware
- LinkScanner Active Surf-Shield, which protects in real time against poisoned web pages.
- LinkScanner Search-Shield, which real-time safety ratings for all search results in Yahoo, Google, and Bing.
- AVG Security Toolbar
And here are additional features Pro edition offers:
- Web Shield, which screens your downloads and prevents accidental infections through IM chats.
- Anti-Rootkit, which protects against hidden threats that deliver malicious content.
- Free support.
It’s not much originally charges $34US for these 3 features addition to free edition but it’s nice there is a way now you can get it for free. It’s your call whether or not it’s worth the effort completing other offers in order to get it.
Related posts:
]]>
Lately I started a couple of new blogs powered on the most popular Wordpress blogging engine. So far, I am really impressed. Two words if you ask me how it is, Awe-Some!!
I have been heavily using it for several months, including a lot of theme installation, customization, theme picking, and plug-in testing. And I even have a project coming up soon that requires me to re-build a website completely on Wordpress using a brand new theme, so I will have my hands on building a Wordpress theme right from scratch.
All that being said, I have quite bit hands-on experience about Wordpress. So I thought I can start a new blog specifically for this topic. I didn’t wait a second and got this domain iBlogWordpress.com registered. However, what turned out is that I didn’t seem to have the time to set it up, and I don’t seem to have enough time later on doing this project. Rather than having this buried in my possession, it might be better letting it pass to another capable hands. So that’s the whole story what behinds this sale. And here are the details.
Domain: iBlogWordpress.com
Price: $100US
Bonus:
- Link here at least for 3 months, starting at its launch time.
- Plus 2 unique posts from me. :)
- $50US more for the first year hosting.
If you are interested, feel free contact me, or leave comment if you have any questions. This is the first time I am trying to sale a domain, so not sure the details how to get the deal going. But, as far as I know, the payment will have to be through paypal. And once the payment is verified, domain will be transferred to wherever you wish to go.
I am also open for partnership too. So contact me if you are interested.
]]>But hey, there is one special day in every year that is only meant for us, system administrator, a day called System Administrator Appreciation Day that happens today this year, last Friday in July. And we will all be appreciated by people around us about our amazing work that keeps their work and life easier. So happy system administrator appreciation day to all sys admin or sys-admin-wanna-be fellows. We all deserve it. :) Special thanks to the sys admins participated on Server Fault sharing this awesome motherboard cake to all of us.

And because today is our day, we also should celebrate a bit more by sharing some of the cool stores with you, pretty much from one post on Server Fault. After all, we only have one chance every 365 days.
Start with having fun with the domains:
Once a nice, old lady called our company asking about an internet domain of her hotel. Her statement: "You are the company ".com", right?" and she wanted us to "redirect" all the email from one "city to another city", because during winter time she lived there. - @splattne
Followed by the power that we as sys admin can control the Internet:
The internet is down. Can you fix it? - @scraimer
Can you pop the Internet on a floppy for me? - @Wayne Koorts
I'm having troubles logging in to the site, can you come look at it for me? My address is 123 Main St, Pennsylvania. - @nickf who lives in Australia
Having fun so far? let’s keep going:
Me: Type A:
Customer: How do you spell that?
Me: The letter A, then the colon symbol
Customer: ...
Me: It's next to the L
Customer: which side?
- @Mr. Shiny & new
And end with one from myself:
I was in computer lab one day after having a basic computer class that taught us some of the very basic DOS commands. And that was my first time sitting right in front of the computer back to the mid 80’s when I was still in high school.
After a few tries without any success of practicing the commands I learned from the class. I finally shouted it out loudly that “where the heck is “dir” key on the keyboard?”. Obviously, I didn’t even know that I need to type them in letter by letter. Shame on myself.
If you like this post you may also like these:
]]>
The package came in with another two small white boxes in it, one of which has the brand new iPhone. However, it's not like the brand new one we usually get when we purchased it. It’s all naked without anything adhered to protect it. No accessories and I am not supposed to send mine back with the old phone either. The package even includes a small paper clip that helps you pop out the SIM card holder. Quite thoughtful as far as I can tell.
There is also one sheet with important notes on it inside the box alerting me that
The returned device will be inspected and tested by our technicians to determine the defect and ensure it has not been otherwise damaged.
If it is determined that the original device is damaged and the repairs are not covered under the manufacturer’s warranty, then a replacement fee of up to $550 will be applied to your Fido account and the damaged device will be returned to you.
That’s fine. I shouldn’t be worried in my case. So hope there will be no surprise later on after I mailed my defected iPhone to them.
Then I went on and started setting up the new phone:
- Backed up the old iPhone in iTune;
- Popped up the SIM card from the old phone and popped it back into the new phone.
- Updated the new iPhone to OS 3.0
- Restored the data back to new iPhone.
- Re-synchronized the new iPhone in iTune.to get all apps back. (I thought this step should be done in the step 4, however, it didn’t happen like that in my case)
- All set and ready to go.
But wait, after opening a few apps I found I actually have to re-configure all apps again because all settings in all apps are just simply not transferred. Pain but ok, still manageable.
Last step, wipe my old phone up so no data would be left on to embarrasses me later on. This process took quite long, approximately an hour.
Now, it’s safe to pack it up and mail it off to Fido, and let them to decide whether or not they want to surprise me.
If you like this post, you may also like these:
]]>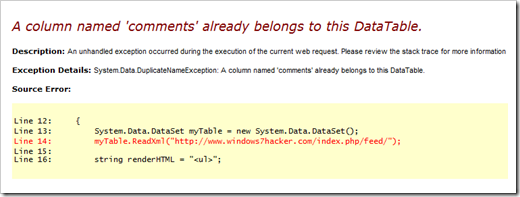
After googling a bit, this post seems to explain the reason why it happens when simply using ReadXml doesn’t work.
The problem is this:
An RSS typically uses multiple namespaces. It lets you have multiple tags with the same name - but using different namespaces makes them different - from the XML perspective. That is indeed the reason for namespaces - to avoid name collisions.
example below from Scott Guthries blog:
<slash:comments>32</slash:comments>
<comments>http://weblogs.asp.net/scottgu/comments/571505.aspx</comments>slash:comments is not the same as comments. But as I said - that's from the XML perspective. The ReadXml doesn't care about namespaces - it tries to create a column "comment" for the XML tag "comment" - and also tries to create a column "comment" for the slash:comment tag. Which gives us the name collision.
The author even offered a quick fix by just simply replacing the “:” with other recognizable character. His code doesn’t seem to work in my case so I re-wrote it my own with using his method of replacing the unrecognized character “:”. Here is mine:
string rssUrl = “rss feed”
XmlReaderSettings xmlSettings = new XmlReaderSettings();
xmlSettings.IgnoreComments = true;
xmlSettings.IgnoreProcessingInstructions = true;
xmlSettings.IgnoreWhitespace = true;
XmlReader xmlReader = XmlReader.Create(rssUrl, xmlSettings);string renderHTML = "<ul>";
while (xmlReader.Read())
{
if (xmlReader.NodeType == XmlNodeType.Element && xmlReader.LocalName == "item")
{
string title = "";
string link = "";
xmlReader.Read();
while (!(xmlReader.NodeType == XmlNodeType.EndElement && xmlReader.LocalName == "item"))
{
if (xmlReader.NodeType == XmlNodeType.Element && xmlReader.LocalName == "title")
{
xmlReader.Read();
title = xmlReader.Value;
}
if (xmlReader.NodeType == XmlNodeType.Element && xmlReader.LocalName == "link")
{
xmlReader.Read();
link = xmlReader.Value;
}
xmlReader.Read();
}
renderHTML += "<li>";
renderHTML += string.Format("<a href='{0}'>{1}</a>", link, title);
renderHTML += "</li>";
}
}
renderHTML += "<ul>";literalContent.Text = renderHTML;
The middle part is for how to rend the feed to the page so you can change to whatever you will like or ever use more tags for more content.
Hopefully, it helps to anyone who wants to read and show the feeds from other resources to their own website and don’t have a handy plug-in or web part to play with.
[updated on Aug14, 2009]
It appears that there is an open source toolkit named ASP.net RSS Toolkit on Codeplex that can do the same thing. Worth checking out if you ran into the same problem.
]]>
I came across this article today that mentioned a new subscriptions business model that is used on FT.com, a model that:
I like the subscription model the FT has been using for some time now. I may get the exact details wrong but its the idea that's important anyway. You can visit the ft.com domain something like nine times per month for free. They cookie you and when you stop by the tenth time in a month, they ask you to pay. And many do.
While I am not a typical marketing guy who can discuss this new strategy more thoughtfully, one thing that do pop up right in my mind is what if I clean up the cookie on my browser every so often, would that allow me to read their news free forever? A typical geek.
Moreover, what if I use the new private browsing, aka incognito first introduced in Google Chrome, that is now available on the latest version of IE, Firefox, and Chrome? Sure enough, because the private browsing wipes out all cookie at the time the browser is closed I sure can visit the site free forever without worrying about the final popup asking me to pay.
I am not saying this new subscription model will not work. Instead, I think it’s a great way of expanding the business. And this “hack” shouldn’t be any factor to be considered while thinking of adopting this model. After all, majority people online don’t even know there is an incognito way to keep themselves from leaving sensitive footprints online.
p.s. to quickly open this private browsing, use ctrl+shift+p on both IE and Firefox and ctrl+shift+n on Chrome.
]]>
Here are the 10 tips from 10 things over on TechRepublic, which you may find useful if being a boss is one of your career goal. Some of them may be different from the traditional way of being a leader but you may find that might be the way that’s should be.
- Become a small picture kind of boss
- Nuke the blackberry when at home
- Stop treating vacation as an option
- Improve the preparation for hiring new players
- Develop your memory, (that’s a good one, it’s so true that people work harder for those who care enough to remember personal things about them.)
- Exercise your body as well as your mind
- Learn these words:”I made a mistake”
- Track how you spend your time
- Don’t demi-task
- Celebrate success.
It seems that these tips are not only good for being a boss in IT industry but also generally useful to other areas too, for example, I can use all these tips to become a better leader and boss at home, I have one staff, soon 3 in total in my department. :)
10 great ideas from five great bosses [via 10 things at TechRepublic]
]]>
If you have ISA server running as security firewall in your office you might want to give this freeware from GFI a try. More specifically, if you want to monitor who is browsing the internet and downloading files in your organization in real time.
GFI WebMonitor™ for ISA Server boosts employee productivity by giving you control over what users are browsing and downloading in real-time. Research by IDC shows that up to 40% of employee internet access is non-work related. As a network administrator, you need the tools that enable you to have complete web monitoring and internet access control to monitor employees' web browsing activities and to ensure that any files downloaded are free of viruses and other malware.
It used to be charging $29.00 per seat for 10-49 users but now GFI offers a freeware version because of the economic downturn. The free version features the monitoring component of GFI Webmonitor that offers a comprehensive picture of
- who is browsing the internet
- which sites they are visiting
- what files are being downloaded and
- how much bandwidth is being used.
While the commercial version offers a little more features, the free version should be good enough for small-medium companies who use ISA as the firm firewall.
]]>
You probably have noticed that I just added a widget in every post that automatically shows some related posts, the picture above is one example from one of my posts.
I didn’t actually write any code for this. All I used is to subscribe the service from an online web app, named LinkWithin. I came across it from other blog the other day and couldn’t help but try it out almost instantly.
So why I need it in the first place? Well, the home page of LinkWithin summarized pretty well:
First, don’t let your past stories go to waste! Yes, simply because no one reads archives you need to present them in a way that can convince people to click.
Secondly, that can indeed help to increase the pageviews and keep readers engaged.
Utilizing it is actually quite easy, just provide your email address, blog link, platform type, and the number of posts you want to list in the form on the home page. And you will get what you need to upload to your blog in the next page.
If your blog is on WordPress, you can actually get to download the final widget. And all you need to do after is to just upload the widget to plugin folder on your WordPress, and enable it. No other settings or actions needed. Bing, and done. It works flawlessly.
If your blog is something like mine that is not on any mainstream blog platform, you can get the JavaScript code and insert them into your blog template manually after.
As they stated on the final page, the quality of recommended stories will improve once they complete their crawl of your blog.
And if you are running into any problem during the installation, simply shot them an email explaining what went wrong. They will response to you next day. The JavaScript code didn’t work on this blog when I first insert them, but they fixed the next day and replied my email very promptly.
It’s overall a nice designed little web app that only does one thing and does that quite well.
]]>
Jeff Atwood originally posted a question on the new launched Super User asking what your favorite harmless computer practical joke is, which turned out getting almost 200 creative answers as of now. When I say creative, they are indeed creative, full of imagination crazy jokes that are totally harmless but would make you laugh to death.
Prank #1
At work we once put on someones unattended laptop computer:
Outlook Rule that went something like this:
when receive email with subject 'duh'
delete email
launch the calculator
play a Homer Simpson audio clip 'lets do some calculating'
Later in a meeting while he was using that laptop for a presentation he would have mysterious calculators pop up with Homer Simpson sounds.
Prank #2
My all time favourite was a small application I wrote and installed on a colleagues computer.
It silently ran in the background and chimed every hour by opening and closing the CD tray and playing a "cuckoo" sound.
Effectively turning their PC into a cuckoo clock.
Note, the poster even shares the source code so you can easily download and play on it. But you will have to visit the site to find the link. :)
Prank #3
Every day, at the end of the day, he'd pick up the mouse and squeeze the mouse cord following it up back to the computer when she was watching - but not when anyone else was around.
Eventually her curiosity got the better of her, and she asked about his habit. He explained that he was pushing the electrons back up into the computer so the mouse wouldn't get bogged down with extra electrons every day and eventually get slower and slower.
She soon took up the habit, and hilarity ensued when her boss asked her about it.
Prank #4
Well, back in the day, I removed the ball from a friends mouse. Can't really do that one anymore... A lot of fun can still be had with Windows' startup sound if they've got speakers.
Commented by:
The first April 1 on my current job, I went around the office and put scotch tape on the bottom of everyone's mouse, including mine, except for one co-worker's.
Many more on the original post, check it out. Laughing is guaranteed. :)
And who once said geeks are stupidly boring?
]]>hotfile.com/.../...timate_Fart_Soundboard.zip.html ]]>
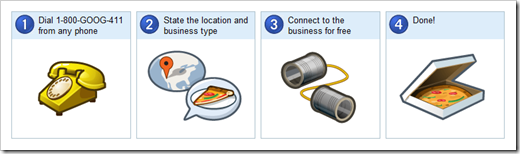
Not sure exactly when, but just noticed that Google has this new 411 service that you can use for free, though it’s only available in US and Canada, and for business listing only at the moment.
Simply, you can just follow the 4 steps shown in the picture above and GOOG-411 will connect you with the business you choose.
Better, if you are calling from a mobile phone, GOOG-411 can even send you a text message with more details and a map by simply saying “text message” or “map it”.
Sounds pretty sweet.
Check the official page for more details.
]]>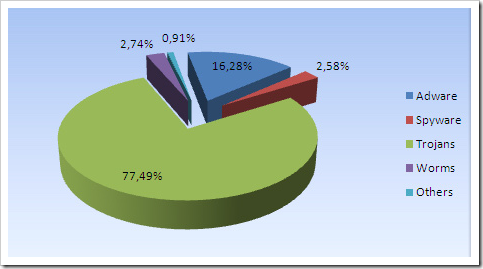
I believe most of people who have been using computer for a certain amount of time have encountered or even suffered this damned never end computer malware, either being a direct victim or being asked to fix it. Finding the better way and the better tool to fight with it seems to have become an inevitable mission to everyone who uses the computer, me included. And for that reason, here are 10 ways to detect computer malware from 10 things that came in quite handy, listed in 3 main categories.
Tools to create the baseline as an important reference
- Microsoft Process Explorer (formerly Sysinternals)
- Trend Micro’s HiJackThis
- Kaspersky’s GetSystemInfo
Tools to prevent from infected in advance
- Microsoft Baseline Security Analyzer, a vulnerability scanner that detects insecure configuration settings and checks all installed MS products for missing security updates.
- Secunia Inspection Scanners, a similar tool as MBSA with ability scanning hundreds of 3rd-party applications.
- Various AntiVirus programs, such as AVG, Avast, TrendMicro, and many more.
Tools to remove the bad malwares
- Microsoft’s Malicious Software Removal Tool
- SUPERAntiSpyware
- Malwarebyte’s Anti-Malware, the best as the author recommended.
- GMER, the best for removing rootkits.
Besides these 4 tools mentioned here, please also check the five best malware removal tools.
The best practice that makes in tough for these non-sense malware developers:
1. Make sure all software on your computer is up to date.
2. Run a baseline scan and save the log file. (You may need it later.)
3. Scan for malware on a regular basis, since sophisticated malware runs quietly.
10 ways to detect computer malware [via 10 things]
]]>Yahoo! Finance
It works on both iPhone and BlackBerry, and will compete with many other players in the market, e.g. Bloomberg, AOL daily Finance, etc. The app supports both portrait and landscape view. And in landscape, it shows a lot more detailed graph info than in portrait. It even pops a bubble telling you that you can rotate your iPhone to view a larger graph. Pretty slick.
And then here is what it looks like after you rotate it.
Yahoo! Fantasy Football
It also works for both iPhone and Blackerry. It’s the mobile version of the web’s #1 fantasy football game from Yahoo! Sports, offering features like live scoring, roster management, add/drop players, matchups, etc. If you are a fan of football, don’t miss this one.
Flickr
It only works on iPhone at the moment, and will compete with tons of already existing Flickr apps from 3rd party. But to me, it beats and kills most of them already. It shoots, uploads, shares not only photos but videos as well. And you can easily tag, group them all within the app. This is the one I particularly love and will be using a lot.
With that believe in heart, I hope they can keep their good work and have more awesome apps released soon and consistently. And with the prediction that mobile advertising will be a next big thing on internet marketing, all these 3 apps are free of charge. And I hope they keep that way. :)
]]>Step 1, fire up Photos app on your iPhone, and click the little icon at the bottom left corner to get into Select Photos view
Step 2, in Select Photos view, select all photos you want to email at once by simply tapping it. And tap Copy button at the bottom of the screen. I selected 4 photos in this case.
Step 3, close Photos app, and fire up Email and start a new email. Simply double tap in the message body area, which pops up the copy/paste dialog. Click Paste, and 4 photos picked at Step 2 will be pasted all together in the message body.
Step 4, once you finish typing all the words, click Send button at the top right corner to send it off. And you will be getting one that has all photos you attached earlier.
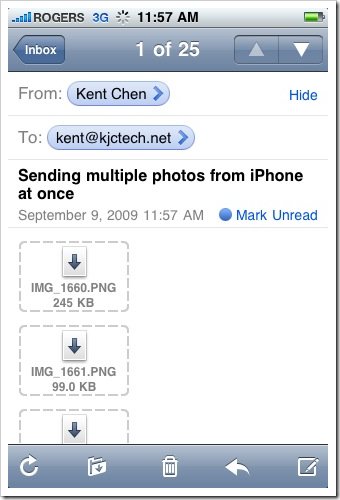
Isn’t that amazing? Enjoy and happy coping/pasting!
]]>
No, I am not telling you buy those illegal copies from many kinds of spam emails. These are tips from digital inspiration for buying legit copies of software through the authorized channels. It saves you money but not likely will be over 70% off, like those ones from the spams. It’s impossible to beat them from cost perspective.
Tip 1, always do comparison shopping.
Tip 2, always remember to check extras like free shipping.
Tip 3, if there is a software program that you want to purchase, go to the manufacturer’s website and subscribe to their email lists and also follow their blog, Twitter feed, or Facebook page.
Tip 4, make sure to purchase upgrade versions if you are eligible.
Tip 5, be sure to check the company’s website for upgrade requirements before you buy.
Tip 6, many software companies offer discounts on full versions of the software to registered users of a trial version of the software, or of the company’s limited versions of the same software or online services.
Tip 7, always check how many computers a program is licensed to run on.
Tip 8, if a program is available in multiple editions (e.g. Microsoft Office, Adobe Creative Suite or Autodesk Suite), try picking the edition that has the features you need.
Tip 9, if you are planning to use coupon codes with the order, make sure that all of the promotions can work together.
Tip 10, many software vendors offer large academic software discount to faculty, staff members, and students. Make sure to check these options.
Tip 11, sometimes you can buy an older version of software that still works at a lot cheaper price.
There are more details in each tip on the original post. Definitely worth checking it out.
How to Buy Genuine Software Online for Less [via digital inspiration]
]]>
IT consulting is not an easy industry. Instead, just like Erik Eckel says here,
IT consulting is a dynamic, ever-changing industry that requires practitioners to maintain multiple skills. Rapid technological shifts frequently change the way you work, the tools you use, and the operational procedures you require. To meet that challenge and stay in the game, you must learn early on how to avoid some of the more preventable pitfalls.
He then went on and shared 10 mistakes that consultants often make in their earlier path.
- Underestimating total project time.
- Failing to properly document project scope.
- Underestimating hardware costs.
- Trying to master all technologies.
- Waiting to send invoices.
- Scheduling too many calls.
- Failing to market the business.
- Overlooking travel costs.
- Charging too little.
- Working Saturdays.
Even only being an independent IT consultant part timely, I found I have made some of these mistakes, quite often in the early days. Man, I am going to send an invoice I have been waiting to send NOW.
10 mistakes that rookie IT consultants make via [10 things]
]]>
Hooray, and more interestingly, this .Net supported develop kit is not offered by Microsoft but its competitor, Novell. The toolkit is named MonoTouch, which will be released today, according to infoworld.
Novell on Monday will offer a kit for developers to build Apple iPhone and iPod Touch business applications using Microsoft's .Net Framework instead of the Apple-designated C or Objective-C languages.
Leveraging Novell's Mono runtime for running Windows applications on non-Windows systems, Novell's MonoTouch 1.0 is a commercial software development kit that lets developers utilize code and libraries written for .Net and programming languages like C#.
As a .Net developer (mostly on ASP.net), I am particularly excited about this news, though that doesn’t mean I will be moving to iPhone development. This is just another approval of the success of .Net platform.
However, while you are excited about this news like me, you may also be disappointed to the fact that it’s a commercial development kit, according to neowin.net
If you're interested in this, and you're not a high ranking member in a wealthy organization, then you're probably out of luck. The program is aimed at developing business applications, and as such, comes with a business-sized price tag. If you want a year long subscription for the Enterprise Edition, it'll set you back $999, compared to the $99 yearly fee which Apple charges; whether that's worth the saved time you'll get from not having to learn another language is up to the business, but it would certainly cost a fair bit (in terms of both money and time) to educate engineers on Objective-C.
Still, let’s see how the .Net community will take on this.
]]>sounds pretty cool !]]>
The very first one goes to this free complete WordPress Cheat Sheet, designed by the guys at ekinertac.com. It’s a must-have for those who develop or modify WordPress themes.
The cheat sheet is in PDF format so you can download it and print it for later use, even post it on a wall that close to you to make your WordPress-life easier.

Again, you can download a complete PDF copy at ekinertac.com
[update - Oct 1, 2009]
Considering WordPress is built in PHP, here is the PHP cheat sheet from Added Bytes as a bonus to those who are interested in developing more in WordPress.
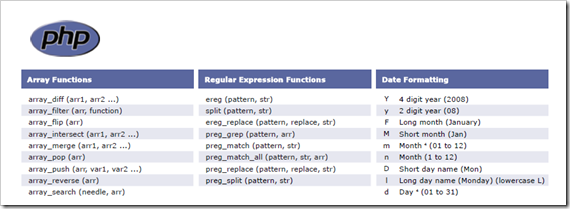

Two issues so far since I upgraded my iPhone 3G to 3.1 a few days back.
1. It has frozen on me at least 5 times. The whole thing went black and refused to response no matter what when it happened. The only thing I can do is hard boot it by pressing and holding both power switch and home button for long enough till the apple log shows up.
Apparently, I am not the only one experiencing the same problem. I have got a few replies saying the same thing after I tweeted it.
2. The awesome Tethering feature stopped working. You can still see it and enable it but once you have the device trying to connect it disappears without any sign indicating why.
Good news is I still should be able to downgrade my 3G to 3.0, which I will be doing so shortly. But for those 3GS owners, they might not be able to. Apple needs to get this fixed in a more timely manner.
So if you haven’t upgraded, you should wait until the next version released.
]]>First, add the System.DirectoryServices reference to my app project in Visual Studio, which adds a single line in Web.config file in <compilation> section telling the web server to reference the Directory Services library from the .Net platform.
Second, add the name space by putting the line “using System.DirectoryServices” at the top part of the code.
Then, in the code applet, do the following:
- Get the authenticated user identity.
string principal = this.Context.User.Identity.Name; - Declare an object referencing to an AD collection
DirectoryEntry entry = new DirectoryEntry(“LDAP://domain”, username, password); - Declare a search object with using login ID as the filter in this example.
DirectorySearcher dSearch = new DirectorySearcher(entry, string.Format(“(sn={0}”, principal)); - Generate a search by
SearchResult result = dSearch.FindOne(); - Get the result and display it on the page.
ResultPropertyCollection dResult = result.Properties;
Response.Write(dResult[“description”][0].ToString();
A few notes
The department information is saved in description field on AD, so that’s why I queried the “description” in this example.
The tricky part is the domain format in LDAP, you will have to put the right format in order to have the app to communicate with AD properly. And you will need a regular user account to connect as well in a real app environment. Here is an example of what LDAP domain should look like:
LDAP://developer.domain.com/OU=Users,DC=developers,DC=domain,DC=com
Basically, the above line tells the app to look for the users in Users organization unit in domain developer.domain.com.
More resources
This is just a very basic example of how to use DirectoryServices library to communicate with Active Directory app. If you are interested in more depth info regarding this topic, here are some great resource to look at.
.Net Directory Services Programming – C# – Part 1, Part 2, & Part 3
And a book that covers a lot more.
]]>
I upgraded my iPhone 3G from 3.0 to 3.1 a few weeks back, which is quite rare to me as I usually don’t upgrade until I am certain the new release is stable. Guess I put too much confident on them as they didn’t let me down for the past few upgrades. But too bad, I was wrong this time. The new firmware 3.1 didn’t do any good for me but bad.
As I posted a few days back suggesting that do not upgrade your iPhone to 3.1 if you haven’t done so, I have two issues with this 3.1.
1. It had frozen on me quite often.
2. No more tethering.
I probably can still live with the issue #1 but losing the ability of tethering really got me mad enough to downgrade it. I thought it was easy, but hell no. Apple puts it quite hard for consumers downgrade their iPhone to an older version. I got the following error in the end of installation every time when I tried.
The iPhone could not be restored. An unknown error occurred. (1015)
Then I followed this instruction from Redmond Pie and finally got my iPhone back to 3.0. However, note that if you want to restore your data back to your iPhone after you downgrade to 3.0 you will need one backup set that’s compatible with 3.0. Without it you will be facing to lose all your data and basically set up a new phone from scratch. I was able to find a copy that I made back in a few weeks, which means even though I got back to where I were I still lost a few weeks data, mostly photos and contacts.
So after wasting a whole night, I am downgraded.
To recap,
First of all, do not upgrade your iPhone to 3.1 if you are thinking of it.
Secondly, downgrade is doable but with cautious of losing your data.
Thirdly, you need a copy of backup that’s compatible with 3.0 if you want your data back.
Finally, if you still want to downgrade, follow this instruction step by step precisely, do no more or less.
]]>
If you are a web professional designer or developer in a small firm that has less than 10 employees and you are already using Microsoft technology, you definitely need to check this new program Microsoft just announced, called Microsoft WebsiteSpark. It’s a nice program that offers Microsoft web development software at no cost, including
- Visual Studio Professional
- Expression Studio 2 or 3 and Expression Web 2 or 3
- Windows Web Server 2008 or R2
- SQL Server 2008 Web Edition
You do have a few responsibility for joining the program, other than being a professional service firm with no more than 10 members. At least, you also need to deploy a new public and Internet-accessible website developed using Program software within 6 months from Program enrollment. The enrollment fee is free with $100US due when you exit the program. Other words, you will need to pay that $100US at the time when you decide not to renew the program in 3 years. For details, it will be a better idea to just read through the program guide. It’s in PDF version.
If you meet all their requirements and are interested, you can go and sign yourself up. You only need a Windows Live ID to start with.
PS, I just signed up a few minutes ago and was told the application is pending approval at the moment. I doubt I will get approved based on what I did but I applied anyway as a self-employed web developer.
]]>Windows Server 2008 Hyper-V: Inside Guide to Microsoft’s Hypervisor
 NetApp offers this book for free to everyone who register on their website by Nov 20th, 2009. The book has 384 pages long and was written by John Kelbley, Mike Sterling and Allen Stewart. Once registered, you will be able to download Chapter 9 immediately but will have to wait 2-4 weeks for delivery. However, the deal is limited to US only.
NetApp offers this book for free to everyone who register on their website by Nov 20th, 2009. The book has 384 pages long and was written by John Kelbley, Mike Sterling and Allen Stewart. Once registered, you will be able to download Chapter 9 immediately but will have to wait 2-4 weeks for delivery. However, the deal is limited to US only.
Register for a free Hyper-V book at http://www.netapp.com/us/forms/us-can-200908-hyper-v-book.html
Understanding Microsoft Virtualization Solutions from Desktop to Datacenter

It’s a book offered Microsoft Press, written by Mitch Tulloch and the Microsoft Virtualization Teams. The technologies covered include:
- Windows Server 2008 Hyper-V
- System Center Virtual Machine Manager 2008
- Microsoft Application Virtualization 4.5
- Microsoft Enterprise Desktop Virtualization, and
- Microsoft Virtual Desktop Infrastructure.
You will need a Windows Live ID to sign up in order to download the whole book in PDF format. It’s offered by Microsoft Press.
Thanks to Windows Server 2008 and Microsoft Virtualization blog for sharing these two awesome offers.
]]>All 5 cheat sheets are from Added Bytes, so
if you like the cheat sheets, and want to say thanks, please consider buying me something from my Amazon Wishlist. Thankyou very much to those who have already hunted it down and sent me something nice - I'm very grateful!
And here we go.
HTML Cheat Sheet
It’s a one-page A4 printable document in both PDF and PNG format.
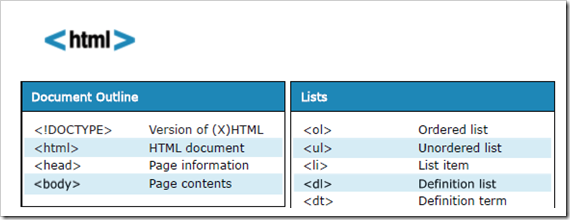
http://www.addedbytes.com/cheat-sheets/html-cheat-sheet/
HTML Character Entities Cheat Sheet
Ever wondered what the code in HTML for a copyright symbol? Here they are, available in both PDF and PNG format.
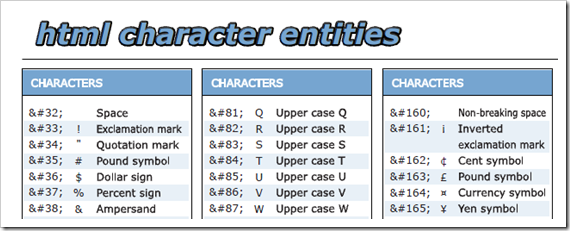
http://www.addedbytes.com/cheat-sheets/html-character-entities-cheat-sheet/
RGB Hex Color Chart
It’s a fairly large chart in both PDF and PNG format on a standard A4 paper. It shows the 216 so-called “web safe” or “non-dithering” colors. Personally, I never heard of what the “web safe” colors are.
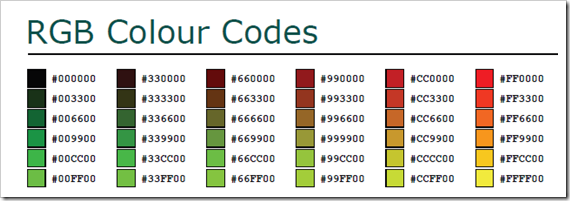
http://www.addedbytes.com/cheat-sheets/colour-chart/
CSS Cheat Sheet
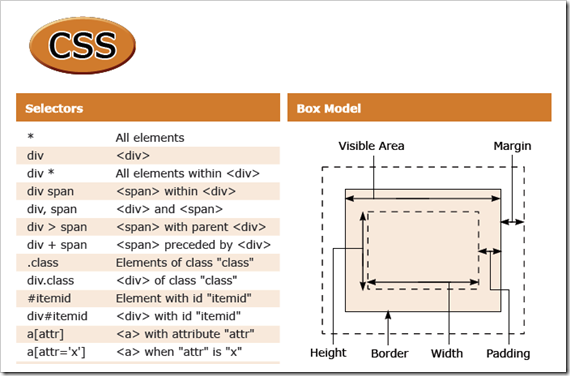
http://www.addedbytes.com/cheat-sheets/css-cheat-sheet/
JavaScript Cheat Sheet
I was never able to pick JavaScript up. So I am hoping this one will help me quite a bit in the future.
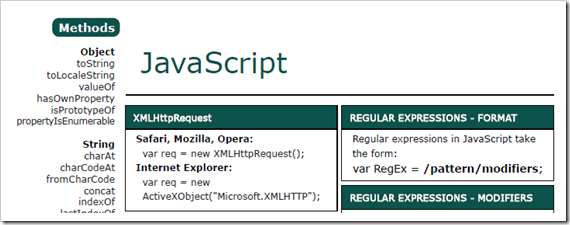
http://www.addedbytes.com/cheat-sheets/javascript-cheat-sheet/
That’s it. Thanks again to Added Bytes for providing us these awesome sheets.
]]>
My motivation of doing anything just got promoted triple times, which left me no time doing things that are wasting time, e.g. writing this post. :)
]]>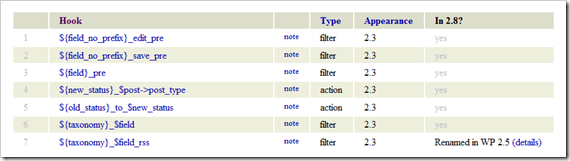
Note that all blue links are clickable, which takes you to the detail hook directory page that explains the specific hook in details.
List of all WordPress hooks via Adam R Brown, shared by @ali360 on Twitter.
You can also check out this free complete WordPress cheat sheet if you are currently looking for one.
]]>I created a new list called Windows-7-Giveaway at the time when I saw this new feature showing up, in a hope using it to manage the Windows 7 Giveaway contest we are running at the moment. So now when I log into my twitter account, first the following status area has changed.
And then the new Lists shown up in the right panel right above the Trending Topics, in which has my new created list Windows-7-Giveaway.
To add the twitters to the list, you will have to go to either the user page or the follower/following list first. And add the people to the list there.
It so far looks good and is very useful to person like me who usually uses the web interface for twittering when working on my laptop. I only use the Twitter apps on iPhone.
It also appears that this new feature is slowly rolling out to twitter users. I have two twitter accounts but only one has this new feature on. So if you haven’t seen it shown up you probably need to be more patient as the rolling out process may take time to finish.
]]>
As an IT pro, I feel always comfortable walking to a computer with a handful tools in my hands. Hunting for good tools in portable format is always on my top 10 list that I need to keep my eyes on it pretty much all the time. Why is portable applications so useful?
With portable applications, you can leave your laptop behind; plug in the thumb drive in any client machine, run the application without worrying about leaving anything behind. In this post, we attempt to show a collection of useful and free applications you can run independently from thumb drives, sorting by profession by general.
So thanks to the guys at Hongkiat for coming up a list of 70 useful portable tools that every geek should at least know about them.
]]>
The tool is so powerful and feature rich that I never found a need that requires me to use any type of plug-ins, even though there are tons out there on Windows Live Gallery for me to download for free. But I can’t ignore this new plug-in that was developed by developer Brandon Turner in Windows Live Writer team and was targeted specifically for WordPress. If you are using Live Writer to write the posts to your WordPress powered blog, you must check it out.
You can download the plug-in from Windows Live Writer Plug-ins on SkyDrive, and save it to the plug-ins folder in your Live Writer installation directory:
%ProgramFiles%\Windows Live\Writer\Plugins
Note that if you are running Live Write on Vista or Windows 7, you will need local administrator rights to save the plugin to the folder above.
This new plug-in offers three features, comments management, custom fields, and blog title/tagline editor. The first two of them will benefit me quite a lot down the road.
Comments management and Blog Title can be accessed from Insert top menu.
The Custom Fields will need to be enabled first and then will be popping up after the post gets posted.
Hide My Ass! helps hundreds of thousands of people daily by protecting their privacy and identity online. They offer a range of unique services, from our web proxy enabling you to surf the web anonymously to our free file hosting with advanced privacy features. Best of all, most of them are free of charge. Here are 3 most useful services they offer:
Free Web Proxy
It enables your online identity and become anonymous for every website you visit. IP address is your online “fingerprint”. By hiding your own fingerprint, you pretty much left nothing for others to trace.
Free Anonymous Email
The free anonymous email service enables you to create a disposable email address to protect your privacy online. If you need to give someone your email address, or need to sign up to a website which requires an email address, but you don't wish to reveal your identity then this free service for receiving emails is perfect. The email account you create will be receiving email only.
Pro VPN Service
It’s an ultimate solution that anonymously encrypts your entire Internet connection. However, it’s not free, and charges on monthly basis.
Check out their website for other services they offer, you may be surprised what you find out.
HideMyAss – Free Proxy, Anonymous Email and VPN service [via How To Hide Your IP]
]]> The book was written by Charlie Russel and Craig Zacker, along with the Windows Server Team at Microsoft. It’s a wonderful resource that can get your hands on this new released Windows Server. And what is more awesome is that Microsoft offers this introduction book through Windows Server 2008 R2 site for FREE. Not sure how long this offer will last, so go and grab your own copy before it’s too late.
The book was written by Charlie Russel and Craig Zacker, along with the Windows Server Team at Microsoft. It’s a wonderful resource that can get your hands on this new released Windows Server. And what is more awesome is that Microsoft offers this introduction book through Windows Server 2008 R2 site for FREE. Not sure how long this offer will last, so go and grab your own copy before it’s too late. The book includes 8 chapters that covers pretty all basic stuff that you need to get started. Here is the table of contents:
Chapter 1: What’s New in Windows Server 2008 R2
Chapter 2: Installation and Configuration
Chapter 3: Hyper-V: Scaling and Migrating Virtual Machines
Chapter 4: Remote Desktop – Services and VDI
Chapter 5: Active Directory
Chapter 6: The File Services Role
Chapter 7: IIS 7.5
Chapter 8: DirectAccess and Network Policy Server
Chapter 9: Other Features and Enhancements
Download your free e-book of Introducing Windows Server 2008 R2
]]>The Windows Automated Installation Kit (Windows AIK) is a set of tools and documentation that support the configuration and the deployment of Microsoft® Windows® operating systems. You can download the latest updated documentation from Microsoft website, which includes 6 separate documents that describe the current methods, tools, and requirements for deploying Windows.

There will be a lot of reading, testing involved if you want to get into it. So be prepared. :)
Windows Automated Installation Kit for Windows 7 documentation (October 2009 Update)
The Windows® Automated Installation Kit (AIK) for Windows® 7 (ISO image download)
]]>And if you are already thinking of jumping into it, you are much luckier than me because now you can have a complete Windows 7 product guide for free to start with, not like me poking around looking for what’s cool and what’s new.

The Windows 7 Product Guide provides a detailed look at the many new and improved features in Windows 7. The guide is designed as an accurate source of information that can help you to understand how Windows 7 Simplifies Everyday Tasks, Works the Way You Want, and Makes New Things Possible. The guide is also designed to provide IT Professionals with information about how to Make People Productive Anywhere, Manage Risk Through Enhanced Security and Control, and Reduce Costs by Streamlining PC Management. This is not a help and how to guide. Rather, it provides an overview of the many exciting features in Windows 7 and pointers to more information. The Windows 7 Product Guide is available in both XPS and PDF formats.
]]>In order to fully utilize all features existing in this new Remote Desktop Services, you will need an updated version of RDP client. Windows 7 already has the latest version built in and Microsoft has just released version 7 of RDP client for both Vista and XP.
So what the new features were added to this version of RDP exactly?
- Web single sign-on (SSO) and web forms-based authentication
- Access to personal virtual desktops by using RD connection broker
- Access to virtual desktop pools by using RD connection broker
- Status & disconnect system tray icon
- RD Gateway-based device redirection enforcement
- RD Gateway system and logon messages
- RD Gateway background authorization & authentication
- RD Gateway idle & session timeouts
- NAP remediation with RD Gateway
- Windows Media Player redirection
- Bidirectional audio
- Multiple monitor support
- Enhanced video playback.
There are also features that are only available when connecting to Windows 2008 R2 from Windows 7.
- Language bar docking
- Remote application task scheduler
- Aero glass support
- Start applications and desktops from RemoteApp and Desktop Connections
Now, let’s play. You can download it from following links.
Download RDP for Windows Vista 32-bit
]]>
Twitter ditched TinyURL for bit.ly as its default URL shortening provider a few months back, which basically put TinyURL to a very difficult position to survive and throw tr.im out of the business. I had been wondering why Twitter made the change because all in all, it’s just a service that shortens the URL and redirect them to the right place. Why does it all matter? I just didn’t quite understand up until now after I have been using it quite extensively for a while.
It’s not like bit.ly has a shorter domain than TinyURL.com. Otherwise, tr.im would have won the game. It’s the statistical tools that bit.ly offers to tracks the popularity of your shortened links matter the most. Basically, you can track pretty much all links shortened by bit.ly, not only yours but others as well, by simply adding a “+” at the end of the shortened link. For example, http://bit.ly/4qdChv is the shortened link for the twitter contest I am currently running on Windows7hacker.com. If you are interested how many hits I got, simply type in http://bit.ly/4qdChv+ in your address bar. And yes, you can do the same to pretty much all links shortened by bit.ly.
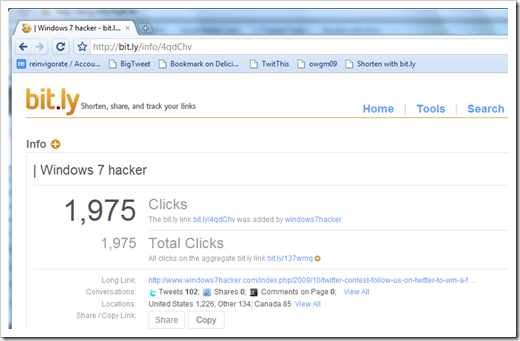
Not only that, if you sign up an account with them you can actually have all shortened links organized within your account. Plus, you get your own API Key that you can use with other application. For example, I use bit.ly as the link shortening service with the API Key in twitterfeed.com so every time when I have a new blog post here it will automatically post a tweet on twitter with bit.ly’s shortened link. So not only do I post tweets automatically but I can also track the detail statistics how many actually clicked and viewed my post.
It also provides a few tools for you to easily shorten the links with capability of posting to Twitter the same time. You can use browser bookmarklet, browser sidebar, or a plugin if you are using Firefox. And you can even use them without signing an account.
No wonder Twitter picked them. It beats TinyURL in almost every aspect. It’s certainly one of the best on the link shortening market.
]]>IIS SMTP Service Folder Structure
The Mailroot folder will be created automatically after you install and enable the IIS SMTP Service, with the subfolders listed below:
- Pickup: The SMTP service processes messages from the Pickup folder as outbound messages or as messages for delivery.
- Drop: Incoming messages intended for the local domains are placed in this folder.
- Queue: Messages that cannot be delivered immediately are moved by SMTP service to this folder from the Pickup folder.
- Badmail: It stores messages that could not be forwarded to the recipient, even after attempts have been made for a predefined number of times. This is the folder sometimes you need to keep your eyes on because these bad mails may eventually fill up your hard drive space.
- Mailbox, Route, SortTemp: They are no longer used in IIS 6.
How IIS SMTP service processes mail?
- The SMTP service, smtpsvc.dll, runs in-process in the Inetinfo.exe IIS process.
- Smtpsvc.dll monitors TCP port 25 for any incoming messages.
- It monitors the Pickup folder for all outgoing messages.
- SMTP places messages for users that are members of the local domain it manages in the Drop folder for delivery.
- If a message has to be sent to a user that is a member of a different or remote domain, an ASP application has to create and place the outgoing message in the Pickup folder. This is done through the ASP application using CDOSYS.
- The SMTP service then performs a DNS lookup on the name server so that it can find the SMTP host that manages the remote domain. The port used for this process is port 53. The SMTP service checks for the MX record for the remote domain.
- After the fully qualified domain name (FQDN) of the remote SMTP host is determined, the SMTP service attempts to create a connection with the remote SMTP host to transfer the message for the recipient to it. Port 25 is utilized for the message transfer.
- If a connection cannot be established with the remote SMTP host, the SMTP service places the message in the Queue folder.
- If a connection can be established with the remote SMTP host but the connection is rejected by the remote SMTP host, the SMTP service forwards the sender of the message a non-delivery report (NDR), and returns the message as well. The message is placed in the Badmail folder if it cannot be returned to the sender.
- If a connection can be established with the remote SMTP host and the remote SMTP host accepts the connection, the SMTP service transfers the message to the remote SMTP host.
- After the message is received by the remote SMTP host it is sent to the POP3 or IMAP mail server which contains the mailbox of the intended recipient.
- The message is downloaded when the client connects to the POP3 or IMAP mail server.
Note that these info are only useful to SMTP Service that come with IIS 6.0. I haven’t had chance working on the latest version yet. So I will update that later.
Again, thanks to Remote Server Support for sharing this useful info.
]]> Finally, it’s done. Being a long time fan of this glorious game, I have no doubt that this will be one of those movies that I am sure I won’t miss. Not sure if there will be episode II, III, or more but let’s just see how it goes this one first.
Finally, it’s done. Being a long time fan of this glorious game, I have no doubt that this will be one of those movies that I am sure I won’t miss. Not sure if there will be episode II, III, or more but let’s just see how it goes this one first. It was back to 1990 or 1991 when I first played this game on a computer that doesn’t even have Windows. Yes, the very first version of Price of Persia is on MS-Dos. :) I still remember it was a timer set to only 90 minutes for me to rescue the kidnapped Princess. I had to battle through many floors to get to the top to accomplish the mission. Too bad, never succeed. But the whole game has opened my eyes to what a video game could like. I was so addicted to it that I wasted many hours on keeping playing on it in a hope I can rescue the princess one day.
And then time forward to 2003 or 2004, I played a version of The Sands of Time on Nintendo’s Game Cube that I bought main for Super Mario. The game wasn’t as hard as Super Mario the Sunshine but it didn’t disappoint me either. I had played a few times after and enjoyed every second I spent on it.
And now, instead of another adventure on the Game Consoles, the unbeatable Prince has made its way to the much larger screen. Hopefully, it won’t disappoint all the fans out there.
]]>At the time it was the best action game I've ever played. My first impression was like watching a movie. and now can't believe they are actually making a real movie from it]]>
Will be posting more short posts like this later on to collect some of the good stuff I read online.
- Windows 7 sales exceed Vista sales by 234% [via Window 7 Team Blog]
- Announcing the launch of Remote Desktop Services Script Center to ease management [via Remote Desktop Services (Terminal Services) Team blog]
- Top 10 reasons to use Windows Home Server in your SOHO [via Windows Home Server Blog]
- William Stanek: Windows 7: Inside Track, Part 5 “Migrations with Windows Easy Transfer” [via Microsoft Press]
We've just activated a feature called retweet on a very small percentage of accounts in order to see how it works in the wild. Retweet is a button that makes forwarding a particularly interesting tweet to all your followers very easy.
Yes, finally Twitter decided to roll out this long-waited feature, a feature that should have been around since day 1. I am just fortunate that one of my twitter account @windows7hacker was selected as one of these beta tester, so I was able to see what this feature looks like and how it works and integrates in my twitter page.
First, this notification box appeared in my twitter page, right above the recent tweets from my following twitters.
And then a Retweet button also shows up in each tweets, right next to Reply. If you want to retweet a tweet, simply click it and confirm from the popup box.
Then, the Retweeted tweet will be easily spotted with a Retweet icon. Yes, you can even undo your Retweeted tweed right in the same place.
Unfortunately, I can’t do RT from a search page or saved search page. It would be nice if they do. Hoping they will fix it in the final version.
I also noticed another small feature that they added in this beta version. It shows how many new tweets that have been posted but haven’t been checked since last time I refreshed the page. They even put the number on to the page title so it gets showed on browser tab. Quite nice.
RT (Retweet) is not invented by Twitter, but by people who use Twitter. It’s a creative ways to get good stuff spread out quickly through the network. It’s so efficient and useful and has been used by almost every tweeter. I am glad Twitter finally made the move and started testing it out, even though it’s still in an early phase. It’s going to be a big improvement once it’s officially released.
]]>When talented people write badly it’s generally for one of two reasons:
Either they’re blinded by an idea they feel compelled to prove or they’re driven by an emotion they must express.
When talented people write well, it is generally for this reason:
They’re moved by a desire to touch the audience.
~Robert McKee
Good touch.
]]>no surprise here, they are Libraries, Aero Peek, Jumplists, Superbar, and Aero Snap, listed in descend order.
introduced an new killer High Availability feature in Exchange Server 2010, called the Database Availability Group (DAG).
a good list of services for those who often use VPN for their P2P downloading.
what happened this week in Microsoft, here are a list of them, Windows 7, Windows Live Wave 4, Microsoft Office Accounting, Patch Tuesday, Job Cuts, and Microsoft Business Productivity Online Suite.
the book is designed to be a concise and compulsively usable resource for Exchange Server 2010 administrators. This is the readable resource guide that you’ll want on your desk at all times. The book covers everything you need to perform the core administrative tasks for Exchange Server 2010.
- Windows Biometric Framework
- Extending Authentication Profiles
- Bitlocker To Go
- UAC Improvements
a fair respond to Sophos Windows 7 vulnerable to 8 out of 10 viruses
”There’s no way I would talk to our CEO about the cloud. For one thing, it’s a bad metaphor. It’s hard to get your hands around, it’s unstable as a weather element…I think it’s a term that should just go away.”
that means, pretty obviously, iPhone is coming to Telus and Bell. Rogers is no longer an exclusive iPhone provider in Canada. Good news to the consumers.
COFEE, Computer Online Forensic Evidence Extractor, is now available to individuals too.
words to remember, do not jailbreak!
If you are like me still sticking around with Exchange 2003, you can forget about Exchange 2007 and move on to 2010 instead. :)
Man, that’s a lot of reading for today.
What he basically claimed in the post was
When it comes to keeping your Windows PC secure, all of the scare tactics and overblown virus stories out there make it hard to feel safe online. The fact of the matter is that you don't need to pay for Windows security.
And he backs up with 6 reasons.
1. Microsoft Security Essentials is a GREAT anti-virus application
MSE is a important release from Microsoft. It closes one gap that should have been filled for a long time. It’s an all-in-one complete application that protects your PC against not only viruses, spyware, but also other malware too. And,
You don't have to take my word for it, however. Not only did AV-Test.org find that it detects 98% of their enormous malware database, but AV-Comparatives (a widely known anti-malware testing group) found that MSE was one of only three products that did well at both finding and removing malware, including the leftovers. It was also the only free product to grab their "Advanced+" rating—the top honor for an anti-malware solution.
Besides, you also have many other free options like AVG and Avast!.
2. Stop whining about “outbound” firewalls
This is a good one. I have been wondering the same too why being able to handling outbound connection in a PC is so important to many people, and why people still use either paid or free 3rd party firewall software to enhance their security. The fact is:
if you just look through your start menu you'll find a link for Windows Firewall with Advanced Security. You can head into there and pretty much configure any setting that you can possibly imagine, getting right down to the port level if you want.
And
The fact of the matter, however, is that outbound firewalls on a desktop PC are Completely Pointless. If the malware has made its way onto your computer, you have already lost the war. Your PC now belongs to whoever is running the botnet, and your outbound firewall isn't going to stop it—after all, the malware can simply add a rule to the firewall to allow access. It's better to focus on keeping malware off your PC in the first place.
Therefore, 1) Windows built-in Firewall is good enough, and 2) you don’t need to worry about outbound connections on your firewall too much.
3. User Account Control (UAC) is NOT a security tool
For those people out there who don’t run any anti-virus software on their computer because of UAC,
The fact of the matter is that unless you've pushed the UAC slider all the way to the top, it's not meant to be a security feature.
So please, do yourself a favor, either install an good free anti-virus software or push the bar all the way to the top.
4. Keep Windows Updated
Needless to say, make sure Windows Update is turned on and reboot your computer at least once a week. Note that MSE data update is also part of the Windows Update.
5. Keep applications like Acrobat and Flash updated, or uninstall them
Here is the point:
Keeping your applications updated is critically important to protecting your security. Your firewall won't protect you, and an antivirus software is unlikely to help if you're using an old, vulnerable version of Flash in your browser
And what you need is a tool that scans your computer and make sure that you are using the latest versions.
6. Stop Downloading Questionable Files
It’s quite common sense but still a few his hints would help us a bit more.
How have I managed that, while being a geek and testing software all the time? There's a couple of simple rules that will protect you:
- Use an online scanner like VirusTotal to scan questionable files before installing them.
- Don't download and install those questionable files in the first place.
- Use some common sense. That pre-release copy of the latest video game you got from a torrent? Yeah, it probably has a virus in it.
So here is the conclusion, “Stop paying for Windows security.” Period! Save that money for good use.
[via lifehacker]
]]>here is the point: At any rate, Chrome OS in on the way and that likely means we'll finally get our hands on the elusive GDrive as well. Here's hoping it does, anyway.
just another big merge. bye-bye 3Com.
Microsoft confirmed that it’s looking into a report of a vulnerability in Windows 7 and 2008 R2 that could be used to remotely crash PCs.
Good news to Mac users
there is strong lobbying in Google to introduce a new ranking factor into the algorithm. The new ranking factor has to do with how fast a site or page loads. Matt described this as one of his ‘what to expect in 2010′ bullet points in his presentation yesterday evening in Las Vegas.
Would that be a big thing? I believe so. Not only does it make those webmasters try hard to crack their code to make their site faster, but it’s also going to squeeze those hosting companies that can’t make the top speed for its customers out of the business. It’s going to be quite a big thing on the Internet. Even though it’s just one of the ranking factors among other 200, it gives you one more reason to speed your site up.
Matt even mentioned that Google has opened up a site that specifically focus on helping you optimize your site so that it can be browsed as fast as flipping pages of a magazine.
In case you don’t know, Matt Cutts is a high-profile Google guy who works on Google’s web spam team. His word can be considered an official answer to your Google ranking. You can also check his webmaster channel on youtube for other great information about Google ranking.
]]>Basically, Desktop Virtualization is the act of running a virtual machine on a desktop PC while the Desktop Virtualization is having the virtual machines running on a server in the datacenter.
So if you have a running virtual machine on your desktop using Virtual PC, VMware Workstation, Sun VirtualBox, etc., you are using Desktop Virtualization. If you are using Virtual Machine via Remote Desktop connection, you are using Virtual Desktop because simply the virtual machine is running on the server not on your local desktop. The picture below is a typical use of Virtual Desktop.

I have two Virtual Machines running on Virtual PC on my local 32-bit Windows 7 RC, so yes I am using Desktop Virtualization technology at the moment. But I am planning on moving both of them off to the Hyper-V machine I am building, so soon I will be using Virtual Desktop technology instead to free up my Windows 7 resources.
[via IT Pro Connection]
]]>
Clicking Learn More opens a web page that explains a little bit more why it happens but offers no good. You basically only have two choices, either buy one from their online store or uninstall it from your computer. If you are using a pirate or counterfeit copy of Office, you should stop reading and do either of these two options Microsoft suggests. However,
The problem is, this is a genuine copy of Microsoft Office but is only used on a computer that is not physically sitting in the office. What they suggest in the case like this is to ask system administrator, which is me in this case. But I didn’t know how to fix it.
After digging a little bit further, it appears that this kind of notification was caused a recent Windows update, named Office Genuine Advantage Notifications (KB949810), which provide periodic reminders to help you take the appropriate action if your copy of Office doesn’t pass the genuine validation.
According to the KB, this update cannot be installed once it’s installed, and there is no option to temporarily stop the notification messages. It appears that this is just a notification application that won’t prevent you from using the Office. You can still use your copy of Microsoft Office, and you can still get the updates from Microsoft. Nothing really has been changed, except that the annoying notification message is now stick on your office toolbar quite firmly.
However, if you are the victim of this update like my colleague and are using the legit copy of Microsoft Office, you can try one of the 5 hacks to disable or remove this OGAN first, and an automated solution to remove OGA second to see if you are lucky enough getting rid of this notification permanently from your computer.
]]>Step 1: Get a copy of VMDK image from gdgt.com
You will have to sign up an account in order to get to the download page. The download file is about 320M big in ZIP format. Once it’s extracted, it becomes 737M big which perfectly fits in 1G flash drive.
Step 2: Extract the VMDK file and save it to your local disk
For example, I saved this VMDK file to c:\-data\virtual images\Chrome OS folder.
Step 3: Fire up VMware Player, and create a VMX file
Well, if you don’t have it yet, you can get one from VMware for free. It’s one of a few products VMware offers for free.
Because I couldn’t get VMware Player to run the VMDK file without the configuration file (.VMX) in place, I had to run through the process of Creating a New Virtual Machine to create one. To do so, you can simply click Create a New Virtual Machine icon to start.

Then, select I will install the operating system later option in the next window and click Next.
Select Other in the next window, and click Next.
Name the Virtual machine name to Chrome OS, and select the folder where I saved the Chrome OS image file. Click Next to carry on. You may get a warning message saying that there is already one VMDK file in the same folder. That’s fine, just click Continue to move on.

Once the New Virtual Machine Wizard is finished, open Windows Explorer and browse to the folder where all VMDK and VMX files are saved, replace the new created VMDK file with the Chrome OS image. Before you firstly launch it, make sure to give the virtual machine at least 512M of RAM.
Step 4: Launch and Enjoy
That’s it, in a short while after starting the virtual machine, I can start tasting the goodies that Chrome OS brings to us.